- 01 May, 2022
- Topic of the Month

1. Introduction
“If security were all that mattered, computers would never be turned on, let alone hooked into a network with literally millions of potential intruders.” - Dan Farmer
Perhaps the most dynamic of the many changes in the new millennium has been information technology. The mass proliferation of networked IT tools has opened up a new world for everyone. A world that offers many opportunities but at least as many dangers.
The explosive development of information systems has also attracted the interest of various criminal circles. At a time when an increasing proportion of citizens have a computer, a smartphone, or an Internet connection, anyone in cyberspace can quickly become a perpetrator or a victim.
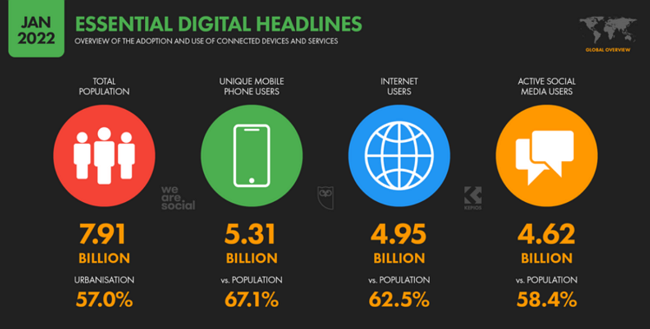
Nearly 8 billion people live on Earth, and 4.95 billion have access to the Internet. It means that 62.5% of humanity uses the Internet more or less regularly. However, anyone with access to it could become a potential target for cybercriminals.
According to a Data Reportal article, 192 million new Internet users have joined the network in the last 12 months. Internet users are currently growing at 4 per cent a year, averaging more than half a million new users a day.
The proliferation of mobile devices has given the expansion of the user base a huge boost. The popularity of mobiles is growing, with many more people choosing smartphones than laptops or tablets because of their ease of use and mobility. Mobile dominance is unquestionable: 92.1% (!) of Internet users use a mobile device to access the Internet.
Global adoption and use of connected devices - Data Reportal
This trend is not expected to change in the future, but you can be sure that it will bring new opportunities and growing threats. The number of devices connected to the network is multiplying, and this applies not only to our phones, tablets, and computers but also to passive devices. IoT (Internet of things) devices such as smart refrigerators, smart homes, in-car computers or wearable technologies and other platforms with an online data connection make our lives easier, but they also have potential vulnerabilities. And there are more and more people who take advantage of these.
With the spread of the information society, the weight of cybercrime has also increased significantly. The threat is global, cross-border, and security issues related to cybercrime are also comprehensive. Adequate protection and detection are essential in a new knowledge-based society. And this cannot be without the full cooperation of law enforcement authorities.
The types of cybercrime have changed today, with faster and more sophisticated methods of committing them. These crimes are mainly committed on the Internet, an ideal crime scene due to their specific characteristics.
New types of crime require a new approach and serious training from both the legislator and the law enforcers. New questions and situations arise, such as whether we can provide justice to a victim whose credit card details were obtained during an online purchase and then used to make purchases abroad. Or how can someone who paralyses a foreign website with a DDoS attack be prosecuted, or the person who does the same from abroad against a website registered in our own country?
The other group of crimes, on the other hand, is already directly linked to the information system. These offences relate to a breach or circumvention of a technical measure to ensure the protection of the information system. Their primary aim is to obtain or alter data stored in the information system or enter false data.

Photo by Towfiqu Barbhuiya on Pexels
In the globalised world of computer systems, the implementation of even the most basic procedural acts is facing severe difficulties. The evidence is primarily based on digital data concerning crimes committed in the cyber environment.
However, one of the critical features of cybercrime is the extremely rapid change in data, which includes the ability to remove evidence effectively. Determining the location of uploading and creating computer data - often due to the lack of cooperation between service providers - sometimes poses an insurmountable task for law enforcement agencies.
Similarly, clarifying the identity of a user can be extremely difficult, given that more than one person often uses the same system. It is also a significant challenge to unlock the increasingly widespread and sophisticated encryption techniques.
Effective detection of cybercrime, in addition to strong national action, requires well-functioning international cooperation.
The basic requirements for the operation of information systems (availability, operability, security) are threatened by various threats. These can be force majeure (such as downtime, natural disasters, war), innocent human acts and deliberate and careless human behaviours. This article focuses on those forms of human action that are intentional harm or negligence in cyberspace and sanctioned as a crime.
2. What is cybercrime?
“Cybercrime is the greatest threat to every company in the world.” - Ginni Rommety
Cybercrime refers to a group of crimes committed with the help of computer devices or targeting individual computers, computer systems or networked devices and the data stored on them.
The importance of cybercrime over the Internet has grown in particular as the computer has become a central component of commerce, entertainment and government. Cybercrime is an extension of existing crime alongside some new forms of illegal activity. Most cybercrime is an attack on information in relation to individuals, corporations, or governments.
Our virtual identity is an essential element of our daily lives in the digital age. We are only encrypted codes in government or corporate databases, and access to our bank account is based on encrypted channels and multi-step authentication. Cybercrime highlights the central role of networked computers in our lives and the fragility and vulnerability of our identities and data.
One of the critical features of cybercrime is its global nature, as huge geographical distances are not an obstacle either. The consequence of cross-border cybercrime is the presence of different jurisdictions and interpretations of law, which often pose severe problems for law enforcement. The fight against cybercrime requires international cooperation.

Image by Kalhh from Pixabay
Therefore, the situation is complicated since different jurisdictions may interpret the same act differently or impose different sentences on the same offence. In this case, the question arises as to where the cybercrime was committed (which country’s jurisdiction and laws should be authoritative)? Is it where the computer with which the crime was committed or the country where the crime took place (the two locations are often in two different countries)?
The Internet offers many hiding places for criminals. However, cybercriminals also leave clues as to their identity and whereabouts. But in order to follow such traces across national borders, international treaties against cybercrime need to be ratified.
3. The history of cybercrime
“Actually think that history has fed off the restlessness of cyberspace, of kind of the frantic, segmented nature of the way we lead our lives. People want to be connected.” - Simon Schama
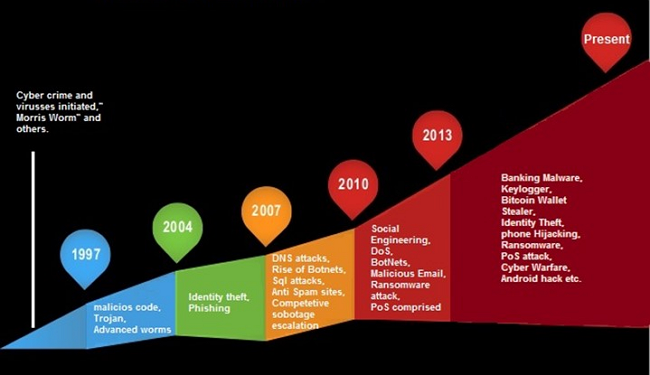
Although the Internet is only about 30 years old, the first cybercrime case happened much earlier. Two thieves hacked the French telegraph system and stole financial market information in 1834. You may listen to a podcast (Human insecurity) about this case in which, among other things, they seek an answer to the question of what lessons can be learned from this incident regarding network security in the modern age?
From the turn of the 1800s to the 1900s, we can talk about hacking telephone systems. Two years after the phone was invented, teenage boys broke into Alexander Graham Bell’s telephone company and caused complications by diverting calls. Phone hacking, also known as phreaking, became popular later in the 1960s and 1980s.
In the 1980s, the advent of e-mails was accompanied by phishing scams and malware transmitted through attachments. By the 1990s, web browsers became widespread, and people started to surf the ever-increasing ‘distance’ of the Internet’s ocean. Indeed, they were increasingly wandering into unfamiliar waters where they could be exposed to viruses and other cyberattacks.
Evolution of cybercrime - InfoSec
And while the above-mentioned pranks were only isolated cases, as diverting a phone call elsewhere would only cause inconvenience to a few people, cybercrime in today’s sense only started after that. The proliferation of web browsers and the drastic increase in the number of e-mail users have laid the groundwork for the rapid spread of malware that causes significant harm to many people over a short period in the network.
At first, cybercriminals attacked individuals the most, but more and more companies were targeted later. Over time, cyberattacks have become more frequent, dangerous, and damaging.
Cyberattacks have caused more and more economic damage, and their importance has grown. Cybercrime has been classified as an economic crime and is already being dealt with at a legal level.
The emergence of cybercrime in the legal environment can be traced back to 1981 when the Committee of Ministers of the Council of Europe issued Recommendation No. 12 on economic crime. The name ‘cybercrime’ was included in point 4 of the recommendation.
The Committee of Ministers of the Council of Europe later (in 1989) issued another recommendation that summarised the new types of offences as computer-related crimes.
The proliferation of social media at the beginning of the 2000s increased cybercrime, and data theft in particular, due to the nature of these platforms.
The 2001 Budapest Convention was the first binding, multilateral and one of the most significant legal documents to date to lay the foundations for the fight against cybercrime. The Budapest Convention promotes the fight against cybercrime at the international, EU, and regional levels, mainly through standard procedural rules on criminal law and a clear definition of technical concepts. It provides a framework for international cooperation for acceding countries and is open to states, not members of the Council of Europe, including the United States. The second additional protocol of the Budapest Convention on enhanced co-operation and disclosure of electronic evidence will be open for signature signed on May 12 and 13 2022, in Strasbourg.
The other major step forward at the EU level was the 2013 Directive, which addresses attacks on information systems by creating the necessary minimum standards. One of the main merits of the Directive is that it has created a harmonised and consistent set of rules in both criminal and procedural terms. This should be emphasised because cybercrime is cross-border, and perpetrators take advantage of the regulatory gaps and differentiation of the legal systems of different countries.
The next level of cybercrime has been caused by the explosive upsurge of IoT devices, which has increased the number of vulnerable objects connected to the Internet.
“IoT without security = Internet of threats.” - Stephane Nappo
The spread of the Internet of Things opened up new vulnerabilities for cybercriminals discovering and exploiting many creative, new ways to attack.
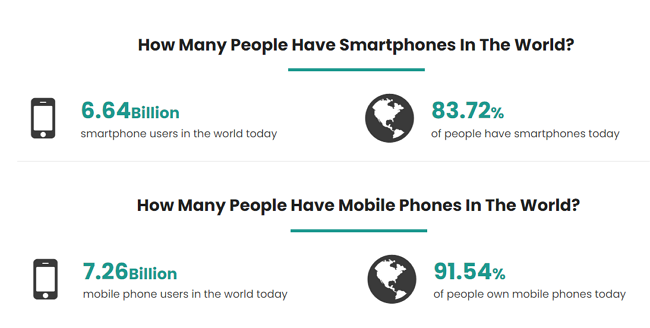
And let us not forget about smartphones either, as more and more people are using smartphones than personal computers. In 2022, the current number of mobile phone users is 7.26 billion, which means that 91.54% of the Earth’s population has a mobile phone.
How many smart- and mobile phones are in the world? - BankMyCell
Seeing the vast numbers above, it is no wonder there were many cyberattacks on mobiles as well. And in many ways, mobiles can be even riskier than a desktop or laptop. In the case of mobile phones, a unique risk element is their high degree of portability and thus their easier theft.
But when you consider how many children receive a mobile phone from their parents as a gift and what kind of sites these young people visit and what attachments they download, it is no surprise that there are many cyberattacks on mobile phones every day.
It is likely that government agencies, offices, and companies will be attacked mainly on servers and desktops, while individuals will be attacked on mobile phones in the future.
4. General characteristics of cybercrime
“Cyberattacks rain down on us from many places. You have to make your systems secure and safe and teach your people cyber hygiene.” - Kersti Kaljulaid
Cybercrime has a wide variety of forms, but in addition to its versatility, it also has certain general or common features as follows:
4.1. Anonymity
Anonymity makes it challenging to link crimes to a specific person. It also harms norms and compliance: people wrapped in anonymity behave differently and are less afraid of sanctions.
4.2. High latency
Most cases remain hidden from the authorities: the victims either do not detect the attack or detect it late or do not report it (because of the possible shame) or do not know where to turn for help.
4.3. A large number of victims
With the generalisation of Internet use, spam, phishing scams, and malware spread extremely fast through networks.

Photo by Madartzgraphics on Pixabay
4.4. High number of infringements
Many spam e-mails, computer viruses, ransomware, and DDoS attacks are rushing at us daily. What is more, malware is popping up more and more in cyberspace and is becoming more sophisticated and can have an increasingly devastating effect.
4.5. High speed and impact
Technological developments allow this type of crime to be committed quickly: the spread of computer malware and the achievement of the desired adverse effects are also rapid. The perpetrators can disappear quickly before the victim notices the attack and the damage.
4.6. Significant damage
Due to a large number of Internet users and technical factors (like the possibility of rapid spread), cybercrime is causing increasing damage.
4.7. Quick adaptability
The methods of cybercriminals are rapidly following the advancement of technology and the use and habits of people. A new trend is that the target is increasingly shifting from computers to mobile devices, as people increasingly use them, but most of them are not yet ready to protect them.
In addition, it can be observed that cybercriminals exploit the current political situation (Russian-Ukrainian war) or some crisis (such as a pandemic) to bombard their victims with spam e-mails and cause damage to their victims.
4.8. Globality and internationality
Geographical barriers do not limit cybercrime. Globalisation makes it more challenging to detect cybercrime and reduces the accountability of cybercriminals (it is much more complex, lengthy and complicated to interpret the current legislation in force in different countries, find the relevant legislation, and bring those responsible to justice).

Image by Pete Linforth from Pixabay
4.9. High heterogeneity
The types of crimes, tools, and perpetrators are also very diverse.
4.10. Difficult to detect
It follows from the above (anonymity, latency, globality, etc.) that cybercrime is difficult to detect. Victims often do not even realise, or only after months, that a cyberattack has taken place to their detriment. It is often the case for individuals and companies that it takes months to discover that someone has broken into their system and stolen some data or caused other damage. There are cases of cybercrime when the perpetrators do not want to cause sudden damage, but on the contrary: they want to keep the attack a secret for as long as possible.

Image by Alexas_Fotos from Pixabay
In such cases, they commit the crime for a long time, even without years of harm: they steal data from the competition, monitor the operation of a competing company, commit cyberespionage to the detriment of institutions in another country, and so on.
4.11. High exposure and hazard
We use IT systems in almost every area of social and economic life, so the risk and threat of attacks are increasing. The risk of such cyberattacks is exceptionally high: they may attack vital industries, power grids, nuclear power plants, transport network systems and cause significant disruption and chaos. At the NATO Summit in Warsaw in June 2016, cyberspace was officially declared the fifth battlefield besides the previous four physical dimensions (land, air, sea, cosmic).
5. Grouping of cybercrime
“From bank accounts to financial systems, power grids to air traffic controls - our most critical infrastructure remain attractive cyber targets, and if they are ever compromised, the effects could be devastating.” - Mike Quigley
Cybercrimes can be divided into traditional abuses and crimes related to the IT system and space. This article does not address traditional abuses but instead attempts to present some possible variants of cybercrime that threaten us in cyberspace.
5.1. Traditional abuses
This group includes illegal activities related to the sending and posting various illegal content in cyberspace. These may include extremist ideas, hateful, harsh posts, child pornography and videos, content that harasses others, violates privacy, misleading ads that promote drug use, or calls for other illegal activity or violations.

Photo by Towfiqu Barbhuiya on Pexels
Guns, drugs, fake passports, other documents, assassins and botnets can be ordered or rented on the dark web. These communications are, in fact, virtual manifestations of traditional crime: cybercrime.
We may say that an average person does not search for anything on the dark web, nor does he know how to get there. But if we think about it a little more carefully, we can already see its dangers: by uploading to IT networks, this content can reach countless users. Linguistic differences are no longer an obstacle, thanks to online translators. Dissemination of dangerous ideas and incitement to illegal activities is a crime already.
5.2. Abuses and crimes related to cyberspace
IT systems are protected by several security solutions, from the physical protection of computers to access control systems to complex and frequently changed passwords. The employee’s expertise and loyalty are also essential security elements.
5.2.1. Social engineering
Unauthorised intrusion into electronic data processing and transmission systems is called hacking. While hacking is typically a ‘direct’ attack on technical means, social engineering is an ‘indirect’ one exploiting the weaknesses of human resources (the purpose of this attack is similar to hacking to gain access to an IT system).
The perpetrator uses openly available information on the Internet and tries to find out as much as possible about the target organisation and the user. Data collection can be continued on-site.

Shoulder surfing – a social engineering technique – SecureOnlineDesktop
The basis of social engineering is that the weakest link in the security chain is usually the person who can be deceived, bribed, coerced, threatened, and blackmailed for different pieces of information (personal data, login IDs, passwords). The perpetrator is typically a kind, flattering, confident person who quickly builds relationships and trust.
The perpetrators try to get into the trust of the target person by using their charm to get to know the interests and habits of the target person. The ultimate goal is to discover the victim’s personal information (such as a password left on a desktop, calendar, or monitor). Social engineering is a complex attack that can be implemented in many different ways. You may read about it in more detail in the article Social engineering: the art of manipulating people.
5.2.2. Phishing
Phishing is a method of social engineering. It is also about getting users’ data. There are many ways to implement it: for example, an e-mail, SMS, or a prominent advertisement on a social site entices the user to click on a link.
Fraudulent advertising suggests that victims can read and obtain additional information if they visit a particular website. Attackers include in their messages a URL or an embedded link that redirects the unsuspecting user to a malicious website (which can also be a clone of a legitimate website). On these pages, additional contact information (addresses, telephone numbers, bank account details, number of personally identifiable documents, etc.) is requested from the victim for fraudulent purposes.

Photo by Tumiso on Pixabay
5.2.3. Pharming
The above is, in fact, typical of pharming. It is an online scam where people are directed to fraudulent websites that mimic authentic ones.
Phishing and pharming are very similar, but while phishing attacks are often carried out via e-mail (and can therefore be considered a slightly more targeted attack), pharming takes place on fraudulent websites where, in principle, anyone arrives by accident ‘without special invitation’.
Phishing attempts can tell private users and employees about fake information, pretexting, for example, asking for help in fraudulent fundraising with false reasons and promises, say a winner in non-existent sweepstakes. They may ask the user to join or support a political or community campaign.
5.2.4. Whaling
A special version of phishing is the so-called whaling attack when the target person is the higher leader of a given organisation or institution. “Trash” - especially when disposing of expired calendars or notebooks - is an excellent time to learn about the data written and forgotten there. It also applies to diaries and calendars thrown away by private individuals at home, but documents created and made redundant during daily work can also serve as a source of information.
For further information on phishing, please navigate to and read the article Phishing: the most common cyberthreat and the everlasting fight against it.
5.2.5. Malware
If private users and employees click on a fake e-mail, they can easily fall victim to a malware attack. The term malware is an acronym formed from the English ’malicious software’ combination. Malware is a summary name for malicious computer programs, and so they may include viruses, spyware, aggressive adware, rootkits, Trojans, and more.
This topic is also a very diverse area from which you can read a lot in the following article Malware: the type of software you should avoid.

Image by 200 Degrees from Pixabay
5.2.6. Ransomware
Ransomware is a type of malware that encrypts the files on a victim’s device or a network’s storage devices. Based on its frequency, the extent of the damage it causes, and its danger, it is one of the biggest cyber threats. Its significance is enormous, and defending against it mainly involves prevention. For more information about ransomware, please read the article Ransomware: better to be afraid than to be frightened.
5.2.7. Data and program manipulation
Electronic data has meaning only for the data subject, the data collector and other information holders in a specific medium and at a specific time. This data may be unlawfully obtained, modified or completely deleted, and shared with other domestic or foreign users. Depending on their content, manipulating the data may cause significant damage and violate copyright and personal rights.
5.2.8. Cyberbullying
Cyberbullying is the collective name for online harassment. It has many forms. These include illegal behaviours such as online stalking, sexual harassment, doxing (posting someone’s personal information on the Internet without the person’s consent), and fraping (breaking into someone’s social media account and posting fake posts on their behalf).

Photo by RODNAE Productions on Pexels
5.2.9. Cryptojacking - Updated
Cryptocurrency is digital money that allows you to make secure and anonymous online payments without the involvement of a bank. A cryptocurrency is a digital token or “coin” that exists in a distributed and decentralised ledger called a blockchain. Bitcoin was the first such coin, but nowadays, there are more than a thousand different types (like Ethereum, Litecoin, Cardano, Stellar, Dogecoin, Monero, etc.) of cryptocurrencies.
Crypto mining is a legitimate business where companies or individuals dedicate a considerable amount of CPU power to solve complicated mathematical problems to earn cryptocurrency. However, in the case of cryptojacking, hackers use your device to mine cryptocurrency without your knowledge or consent.
Cryptominers do this by using JavaScript to infect your device after you visit an infected website. Since crypto mining is a CPU intensive process, you may experience performance issues and high electric bills, whereas cryptojackers earn big profits.
5.2.10. Cyberespionage
Not only can cybercriminals be lonely offenders, they often carry out their illegal activities in a well-organised and group manner, often supported by the state of a country. Perhaps the best example of this is cyberespionage, carried out by state-sponsored groups on behalf of the government of one country to gather information about other countries.
Computer espionage is primarily used to collect classified information and trade secrets that the aggressor may use to create a competitive advantage or sell it for financial gain. Cyberespionage is possible not only between countries but also between competing companies or businesses, especially to steal material profits and intellectual property.
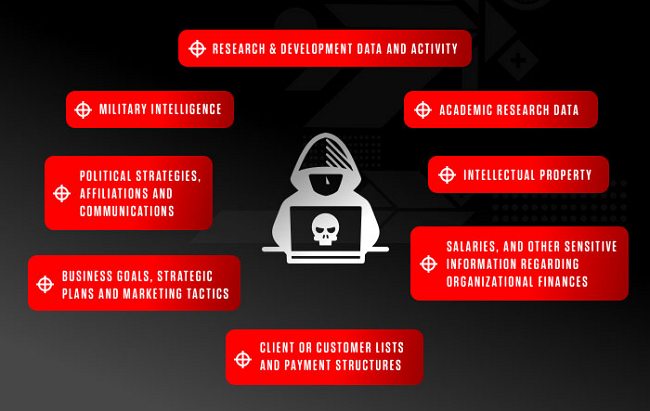
Cyberespionage targets - Crowdstrike
6. The dark side of the Internet
“We live in a world where all wars will begin as cyber wars… It’s the combination of hacking and massive, well-coordinated disinformation campaigns.” - Jared Cohen
6.1. Deep web
The deep web is the part of the Internet that is not accessible by standard search engines (Google, Firefox, Bing). In other words, these websites and web pages are not indexed by search engines, so you cannot find them in the search results.
But do not think you have never been to the deep web before. It is very likely that you visit it several times a day and spend several hours there daily. The deep web contains any web page protected from being openly accessed: pages behind firewalls, authentication forms, login information, or passwords. E-mail, private social media accounts, online banking accounts, and subscription services are among these websites - just to name some.
6.2. Dark web
The dark web, or darknet, is a subset of the deep web that requires a unique browser, such as Tor, to access it. While the dark web alone is not illegal, its anonymity makes it a hotbed for crime. The dark web provides anonymity by encrypting communications and controlling online content through multiple web servers. Access to the dark web requires special software that preserves anonymity.
The use of the dark web is legal. The fact that communication is encrypted and the identity of users cannot be revealed does not mean that everyone is preparing for or participating in a crime.
However, it is possible to buy and sell illegal drugs, malware, and illegal content on the dark web. It also happens that personal data (e.g. passwords, bank card data, etc.) and dangerous chemicals and weapons are sold and traded there.
Some hackers offer ransomware as a service (RaaS) when self-appointed cybercriminals can “rent” ransomware from these hackers. In the event of successful extortion, the renters can pay a certain percentage of the ransom they receive to the hacker.
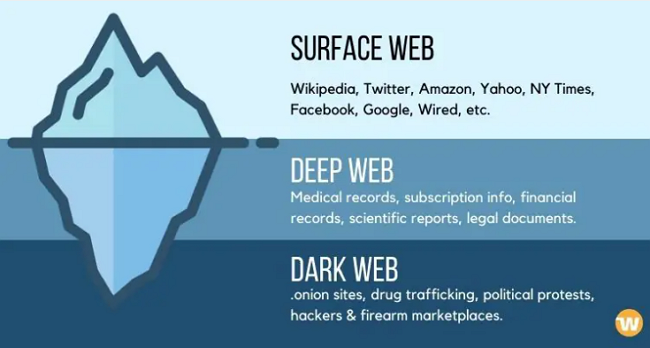
Surface web – deep web – dark web - WebHostingSecretRevealed
Other hackers may sell software exploits that other cybercriminals can use to infect victims with malware and steal personal information. These acts are a great danger in themselves, but the biggest problem is that in such cases, one who wants to carry out a cyberattack or a cybercrime does not have to have much expertise. This kind of illegal liberalisation of cybercrime further increases the threat to healthy cyberspace by multiplying malware.
7. Cybercrime trends nowadays
“Cyberwar takes place largely in secret, unknown to the general public on both sides.” - Noah Feldman
According to an article by Govnet Technology, the 5 most risky trends in cybercrime today are as follows:
7.1. COVID-themed cyber security threats
The epidemic has forced many to work from home, which is risky as it blurs the line between professional and private tools. The transition to work from home had to be solved by millions of people suddenly. The unexpected life situation and the stress and mental pressure that comes with it have unprepared for both individuals and companies.
According to Tech Republic, around 25% of COVID-related domains are malicious, and nearly 2,000 malicious COVID-19-themed domains are created every day.
There is also a significant risk of (apparently) fake e-mails from the World Health Organization (WHO) sent by cybercriminals for phishing attacks. Google says 18 million deceptive messages are sent to virtual mailboxes every day, a substantial potential risk.

Photo by Obi - @pixel6propix on Unsplash
7.2. Prevalence of IoT
As per CompTIA, there will be 18 billion IoT devices by the end of 2022. According to Cisco forecasts, their number is expected to reach 500 billion by 2030. More devices mean more potentially vulnerable endpoints, and the number of attacks on IoT devices has multiplied in recent years.
The small size of the devices, the high degree of mobility, and the considerable number of devices in both companies and private individuals make it difficult to keep track of their inventory: who has how many devices, where they are located, what software version is running on them, etc.
Ransomware attacks can compromise the IoT device’s functionality, and sensitive data can also be stolen from devices like these. For detailed information on IoT devices, please consult the article IoT: Is it a blessing or a curse?
7.3. Malware-as-a-Service is on the rise
While only a tiny percentage of people have the skills and abilities to carry out effective cyberattacks, malware is already available to those who do not have such skills.
Unfortunately, the digital environment is conducive to the spread of the Maas (Malware-as-a-Service). It is a subscription-based service that anyone who tries to scout their victims with e-mails containing malicious attachments can access through the dark web. Maas is a type of organised cybercrime; it is a criminal version of SaaS. And MaaS, just like legitimate software, is even regularly updated.
7.4. Increasing malware and ransomware attacks
Ransomware attacks are one of the most devastating cyberattacks that seem to stay with us in the future. The victim’s files are locked during the attack, and they can only access them if they pay a ransom for them. However, we know that there is no guarantee for this.
Unfortunately, the pandemic has exacerbated the situation, making individuals and companies extremely vulnerable. Switching to remote and flexible work means more vulnerabilities for extortion viruses and malware. Employees working from home have less protection than working in a traditional office environment, without work servers or Wi-Fi supported by purpose-built cybersecurity.
The annual cost of ransomware for organisations worldwide is rising sharply. Of further concern is the increase in the number of incidents and the average amount of ransom paid per incident.
Unfortunately, ransomware attacks are evolving rapidly and will be used even more frequently in increasingly complex and powerful attacks. For further info, please check the article Ransomware: better to be afraid than to be frightened.

Photo by Elchinator on Pixabay
7.5. Cryptojacking
Recently, we have seen an increase in the number of crypto-specific cyberattacks. One of the most popular forms of cyberattacks of this nature is cryptojacking, where malicious programs are used to attack a system and then illegally mine cryptocurrency.
Cryptojacking is a very lucrative market as some cryptocurrency markets are worth billions. The process is relatively simple, requiring no further steps to remove or launder stolen money. Due to its relative simplicity and low risk, it is a popular type of cyberattack.
Besides the above 5, let us mention an additional factor that may be a matter of serious concern.
7.6. AI in the wrong hands
According to IT experts, current and future trends point in the direction that cybercrime could become a war of artificial intelligence over time: attacks and attempts to defend them will be increasingly dominated by automatisms. Artificial intelligence plays a significant role in detecting incidents. The next stage of development will be when artificial intelligence recognises the signs of an attack and responds to it independently.
8. Cybercrime data and statistics
“Cyber weapons won’t go away, and their spread can’t be controlled. Instead, as we’ve done for other destructive technologies, the world needs to establish a set of principles to determine the proper conduct of governments regarding the cyber conflict.” - Jared Cohen
8.1. Global statistics and situation
According to Cybersecurity Ventures, the cost of global cybercrime will reach $ 10.5 trillion by 2025, compared to $ 3 trillion in 2015.
- 495 million ransomware attacks occurred in the first nine months of 2021 (SonicWall)
- 14.46 million ransomware attacks were blocked in Q2 2021 (Kaspersky)
- There were 153 million new malware samples from March 2021 to February 2022 (AV-Test)
- Cryptomining malware increased 117% in Q1 2021 (ENISA Threat Landscape 2021)
- In Q4 2021, the number of DDoS attacks increased more than 4.5 times over the same period in the previous year (Kaspersky)
- It takes an average of 280 days to detect and curb a cybersecurity incident (IBM)
- It is projected that by the end of 2022, there will be 18 billion IoT devices (CompTIA)
- 95% of cyber security incidents are due to human error (The Hacker News)
- Russia (24,7%) and Germany (14,1%) were the top spam-source countries in 2021 (Kaspersky)
- The most frequently impersonated brands in Q4 2021 were DHL (23%) and Microsoft (20% of the time) (CheckPoint)
- Women represented 25% of the global security workforce in 2021 (Cybercrime Magazine)
- Nearly 2,000 malicious COVID-19-themed domains are created every day (Tech Republic)
These figures are likely to be significantly underestimated, with some estimates suggesting that only about 10% of cybercrime is reported each year.
The reasons for this may be different: on the one hand, the fear of shame or damage to reputation, and on the other, the assumption that law enforcement agencies cannot help or victims do not know where to turn.
In addition to being significantly underrepresented, the above data is very general, as there are many cybercrime variants. Therefore, instead of using general data, it may be more reasonable to discuss and link data to different types of cybercrime separately. As cybercrime refers to a wide variety of cyber-attacks, here are some snatched examples of the economic damage caused by certain types of cybercrime.
Ransomware
Ransomware attacks are not only becoming more severe, targeted, and more noxious, but also their frequency is dramatically and constantly growing. While in 2015, there was a ransomware attack every 120 seconds, their frequency has increased dramatically by 2022. Nowadays, a ransomware attack is carried out every 11 seconds.
CyberSecurity Ventures predicts that annual damage to ransomware will rise from $ 5 billion in 2017 to $ 20 billion by 2022.
Ransomware is an excellent source of revenue for individual attackers. It does not require much skill, as ransomware kits can be purchased on the dark web.
On the page of Dataprod, there are a number of thought-provoking facts about ransomware, including that 95% of the profit from ransomware is laundered through the cryptocurrency exchange.
Crypto crime
Crimes linked to cryptocurrencies show a similar trend: their frequency and the damage caused are also increasing. Cybercrime with cryptocurrencies caused $ 17,5 billion in damage in 2021. By 2025, that value is estimated at $ 30 billion.

Photo by Roger Brown on Pexels
Phishing
As per the Associated Press, there has been a 600% rise in malicious e-mails during the coronavirus pandemic. Trend Micro researchers say more than 90% of cyberattacks start with phishing e-mails. According to the above, if we could somehow mitigate the damage associated with phishing e-mails, we would make a significant step toward reducing the cost of cyberattacks on individuals or companies.
The question arises as to which are the countries where we are least at risk of becoming a victim of a cyber attack. The following picture shows the 10 countries where cybersecurity is most robust, and people are most protected from cybercrime through legislation and technology.
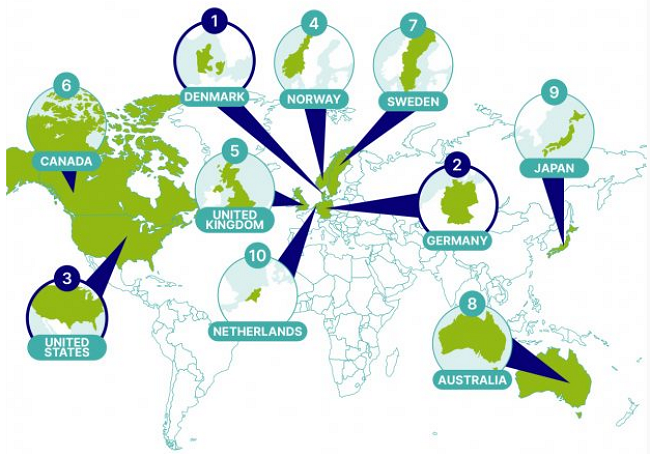
The Most Low-Risk Countries for Cyber Threats – SEON Global Cybercrime Report
At the other end of the line are the countries where people, businesses and the state itself are most exposed to the dangers of excellent cyberattacks.
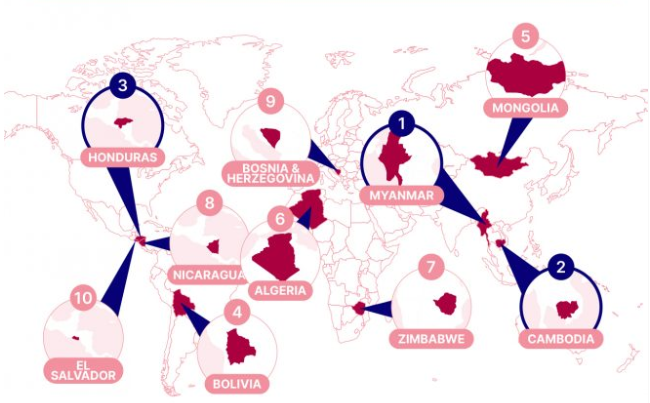
The Most High-Risk Countries for Cyber Threats – SEON Global Cybercrime Report
Cybercrime Ad Hoc Committee
Curbing a global threat requires global cooperation, an excellent example of which is the recent UN initiative. The UN General Assembly has decided to set up an intergovernmental commission of experts from all regions to draw up a comprehensive international convention to combat the use of information and communication technologies for criminal purposes.
The open-ended Ad Hoc Committee considers existing international instruments and efforts at national, regional and international levels in its work to combat cybercrime. The Committee was mandated to develop a new convention against cybercrime by 2023.
The first two week meeting took place on 27 February – 11 March 2022 in New York. Thus, the formal process of negotiating a global convention against cybercrime at the UN has begun. Participating countries can submit their proposals, and then members can discuss the motions at the consultations.
8.2. Situation in Europe
8.2.1. The birth of the Network of National Coordination Centers
As in any corner of the world, cyberattacks and cybercrime are becoming more and more sophisticated across Europe, and cybercrime is a major threat to European citizens, businesses, and the economy.
Recognising the gravity of the situation, the European Commission and the European External Action Service (EEAS) presented a new EU Cybersecurity Strategy in December 2020. This strategy aimed to strengthen Europe’s resilience to cyber threats and ensure that all citizens and businesses have full access to reliable digital services and tools.
On 22 March 2021, the Council adopted conclusions on a cyber security strategy, highlighting a number of areas for action in the coming years. One such effort was to set up a network of security operations centres across the EU to monitor and forecast attacks on networks.
The Network of National Coordination Centers (NCC) consists of 27 centres, one from each Member State. The Competence Centre, located in Bucharest, together with the Network of National Coordination Centres, will contribute to strengthening European cybersecurity capacities.

The European Cyber Security Competence Center (ECCC) and the Network of National Coordination Centers (NCC) are Europe’s new frameworks for supporting cybersecurity.
8.2.2. The European Cybercrime Center
The European Cybercrime Center (EC3) was set up in 2013 by Europol to strengthen the EU’s cybercrime law enforcement response, helping to protect European citizens, businesses and governments from cybercrime. EC3 focuses on cyber-dependent crime, child sexual exploitation, and payment fraud-related crimes.

Europol – European Cybercrime Centre – EC3
The main achievements of the European Cybercrime Center in reducing cybercrime are as follows:
- EC3 took a significant role in the takedown of one of the most significant botnets of the past decade, EMOTET
- EC3 has also been involved in one of the largest and most sophisticated law enforcement operations in the fight against encrypted crimes called Operation Trojan Shield/Greenlight
- One of the most significant achievements of EC3 was the cracking down on the illegal use of Sky ECC’s encrypted communications by large-scale organised criminal groups. As a result, critical information has been gathered on more than a hundred planned large-scale criminal operations, anticipating potentially life-threatening situations and potential casualties.
- EC3 has also achieved noteworthy success in the fight against ransomware: Operation TALPA, Operation GOLD DUST / QUICK SAND and Operation FIFTH.
- Most recently, as a result of Operation TOURNIQUET, the illegal marketplace “RaidForums” has been closed and its infrastructure seized.

The illegal RaidForums marketplace was closed as a result of Operation TOURNIQUET
Each year, EC3 publishes the Internet Organized Crime Threat Assessment (IOCTA), a strategic report on the key findings of cybercrime and emerging threats and developments. IOCTA provides a law enforcement-focused assessment of evolving threats and critical developments in cybercrime. The main findings of the 2021 report on the state of cybercrime in Europe are as follows:
- Criminals continue to abuse legitimate services such as VPNs, encrypted communication services, and cryptocurrencies
- Ransomware associated programs allow larger groups of criminals to threaten large companies and public institutions with DDoS attacks
- Malware is becoming more prevalent on smartphones, and these programs are trying to bypass security measures such as two-factor authentication
- The explosive growth in online shopping has led to a sharp increase in the number of online scams
The Internet Organized Crime Threat Assessment report - IOCTA 2021
8.3. Situation in Luxembourg
As per the e-Governance Academy Foundation, the Global Cybersecurity Index of Luxembourg is 13th, whereas the National Cyber Security Index is 38th in 2022. The full report can be downloaded from here.
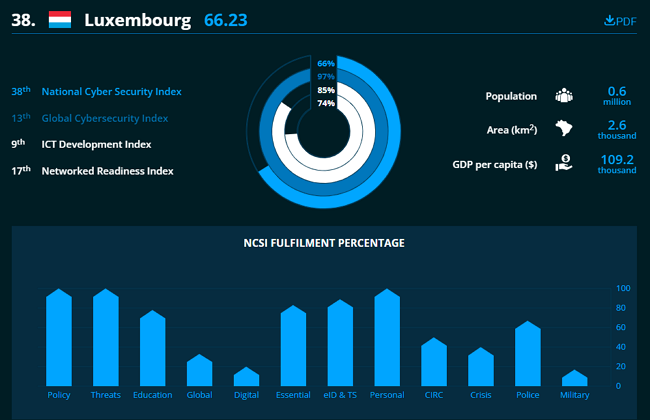
Luxembourg Cybersecurity Index - e-Governance Academy Foundation
And while Europe is the safest in cybercrime compared to other continents, and Luxembourg ranks high in Europe and the world, we must nevertheless remain vigilant and further strengthen our action against cybercrime.
As per Europol’s National Central Bureau Luxembourg (NCB), organised crime groups operating in Luxembourg are mainly involved in drug crime, car trafficking and fraud. Police officers working at the NCB are trained experts in the fight against terrorism, crimes against children, cybercrime and financial crime.
Because cybercrime has a wide variety of manifestations and cybercriminals often perform their activities in an extremely organised and helpful manner or in groups, we can only fight them successfully if we act against them with a similar organisation and unity.
On 16 February 2022, Pascal Steichen, CEO of SECURITYMADEIN.LU was elected Chairman of the European Cybersecurity Competence Centre (ECCC).
“I welcome this appointment with great enthusiasm and pride. A major task awaits us, to build and continually strengthen this European cyber community. Joining forces to strengthen research, innovation, and the response to emerging threats is a key factor in increasing Europe’s cybersecurity capabilities and competitiveness”. – Pascal Steichen

National Cybersecurity Coordination Centre Luxembourg - NCC-LU
9. The impact of cybercrime
“We face cyber threats from state-sponsored hackers, hackers for hire, global cyber syndicates, and terrorists. They seek our state secrets, our trade secrets, our technology, and our ideas - things of incredible value to all of us. They seek to strike our critical infrastructure and to harm our economy.” - James Comey
We all know that the impact of cybercrime can be devastating. This chapter looks at the severe effects cybercriminals and cyberattacks can have on individuals, companies, and countries.
9.1. On individuals
- Use firewall and antivirus software
- Use two-factor authentication
- Use a professional VPN service and secure networks
- Choose strong passwords and use password managers
- Update your software regularly
- Always back up, make online and offline copies
- Think before clicking on links
- Make cyber hygiene a part of your daily routine
The adverse effects on individuals can be very diverse. Cyberattacks and cybercrime have many faces like data leakage, identity theft, and device problems (when the attack hits their device, cell phone, or laptop).
You may be charged suspicious charges on your credit card following identity theft. But it is also possible that after a ransomware attack, you cannot access your files on your device and the cyberattacker demand money from you to release the locked files.
An exceptionally high electricity bill could arouse suspicion of cryptojacking. But there are also many life situations where the attack cannot be monetised: such cases include cyberbullying or sexual harassment.
9.2. On businesses
Organisations in all industries are exposed to some form of cyberattack daily. Not only the big brands are at risk of falling victim to social manipulation attacks, extortion programs, or other cyber threats. Even the smallest businesses are not small enough to stay away from the radar of cybercriminals. If your business uses a single computer or smartphone to operate, you risk falling victim to a cybercriminal.

Photo by Towfiqu Barbhuiya on Pexels
Moreover, according to Accenture Ninth’s Annual Cost of Cybercrime Study, while many large businesses have suffered infringements, small and medium-sized businesses have been easier targets for hackers due to a lack of resources and security expertise. And because they are easy targets, cyberattacks on small and medium-sized businesses are becoming more frequent, targeted, and complex.
The most common types of attacks on small businesses include (Forbes):
- Phishing/Social Engineering: 57%
- Compromised/Stolen Devices: 33%
- Credential Theft: 30%
And the most Targeted Sectors Worldwide by Hackers in 2021 (Forbes):
- Education/Research sector up by 75%
- Cyberattacks on the Healthcare sector up by 71%
- ISP/MSP up by 67%
- Communications +51%
- Government / Military sector up by 47%
Businesses of all sizes can suffer huge losses from sensitive data loss, substantial financial burdens and brand damage. Data leaks can also have a massive impact on companies and their customers, with a loss of service resulting in a significant loss of revenue. However, the damage to reputation and disengaging customers is often far more significant than that caused by the original cyberattack.
Therefore, companies themselves report data theft to reduce the harmful effects of a cyberattack and make it meaningless to pay the money blackmailed by cybercriminals. In this way, the reputation has been damaged less, as customers may feel that the company has not concealed the fact of the cyberattack. In fact, the company has informed its customers that such an incident has occurred and thus still appears to be a more reliable and transparent company.

Photo by B_A/34 on Pixabay
9.3. On governments
Not only can cyberattacks be perpetrated against individuals or companies, but countries can also conduct cyberattacks against each other
The 10 most cyberattacked industries are healthcare, manufacturing, financial services, government, transportation, retail, energy and utilities, media and entertainment, legal, and education.
As per the Microsoft Threat Intelligence Center (MSTIC) and the Microsoft Digital Crimes Unit (DCU), nearly 80 per cent of nation-state attacks were directed against government agencies, think tanks, and non-government organisations.
As for the most targeted countries, the United States remained the most highly targeted, followed by Ukraine. Microsoft also reported that 58% of cyberattacks from nation-states originated in Russia, and most of these attacks heavily targeted Ukraine.
On the Center for Strategic and International Studies (CSIS) website, you may find a list of significant cyber incidents since 2006. The list includes 9 incidents as of March 2022, of which the following are the most interesting:
- Pakistani government-linked hackers targeted Indian government employees in an espionage operation.
- At the start of the Russian invasion, an attack on a satellite broadband service run by the American company Viasat disrupted internet services across Europe, including Ukrainian military communications.
- The U.S. Department of Justice charged four Russian government employees involved in hacking campaigns between 2012 and 2018. The hacks targeted critical infrastructure companies and organisations mainly in the energy sector. The hackers sought to install backdoors and deploy malware in the operational technology of their targets.
- According to the Russian Ministry of Digital Development and Communications, hackers defaced and disrupted several Russian government and state media websites.
- Hackers linked to the Chinese government penetrated the networks belonging to government agencies of at least 6 different U.S. states in an espionage operation.
It is clear from the list above that there is a war going on in cyberspace between countries, one of the manifestations of which is cyberespionage. Even more striking is that the frequency of these attacks and espionage is very high (the list includes only the most significant cases).
10. What can you do?
“A security system with several layers is difficult to hack. So, even if your data is targeted, getting through the many tiers of security will be a hassle. The simplest of programs, such as free online e-mail accounts, have multi-layered security, too. Even if accessing your accounts takes a few extra steps, it is still worth the effort, certainly better than losing your data. Using a firewall, making sure your antivirus software is updated, running antivirus checks frequently and updating your programs regularly are all part of maintaining your personal data security.” - Doug Theis
Defending against cyberattacks should be a continuous and uninterrupted activity. Everyone who uses the network must do so responsibly, and everyone has the duty and responsibility to take measures in their territory to prevent or avoid cyberattacks. Most of these tips are almost self-evident, and everyone has heard of them, yet we face countless successful cyberattacks every day.
How can you defend yourself against cybercriminals?
- Protect your devices! Use firewall and antivirus software that scans your web pages, downloads, attachments, and external hard drives.
- Use secure networks! Do not connect your devices to Wi-Fi networks that you are unfamiliar with or unable to determine how secure they are.
- Choose strong passwords! Use password managers. Two-step identification can also help a lot, reducing the risk of abuse.
- Update your software regularly! The latest version of security software always provides the highest level of security.
- Always back up! If your critical data is stolen or destroyed, it can be life-saving to have a copy on hand. It’s best to make offline and online copies of your data (such as cloud-based).
- Click carefully! Uncontrolled communication channels also pose serious risks. Never click on an e-mail attachment, social media message, or text message that you don’t know the source of - it could carry potential dangers.
- Don’t share personal information on social media! If you share everything that happens to you, it can be an excellent resource for scammers who can use them for phishing or identity theft.
- Permanently delete your data from your unused devices! If you sell your laptop or tablet, make sure you have all your personal information removed.
- Make cyber hygiene a part of your daily routine. If you follow the above, you may never become a target for cybercriminals.

Photo by FLY:D on Unsplash
11. How can SECURITYMADEIN.LU help?
“Most people are starting to realise that there are only two different types of companies in the world: those that have been breached and know it and those that have been breached and don’t know it. Therefore, prevention is not sufficient, and you’re going to have to invest in detection because you’re going to want to know what system has been breached as fast as humanly possible so that you can contain and remediate.” - Ted Schlein
In Luxembourg, the following authorities and departments are responsible for preventing, analysing and combating cybercrime.
National CERT Luxembourg (NCERT.LU), the CERT of the Government of the Grand Duchy of Luxembourg (GOVCERT.LU) and the Computer Incident Response Center Luxembourg (CIRCL) are the main actors responsible for the detection of and response to incidents.
SECURITYMADEIN.LU is the national cyber security agency for the Luxembourg economy and municipalities. The Agency has been appointed as the National Cybersecurity Coordination Centre (NCC) and represents Luxembourg within the European NCC network in the framework of the establishment of the European Cybersecurity Competence Centre (ECCC).
It provides extensive cybersecurity expertise and solutions to SMEs and companies of all sizes and municipalities through its three departments: CIRCL, CASES and C3, in close collaboration with the CYBERSECURITY Luxembourg ecosystem’s players.

While CASES (Cybersecurity Awareness and Security Enhancement Services) has multiple services available to the public to raise awareness concerning cybersecurity, C3 (The Cybersecurity Competence Center Luxembourg) helps organisations reach a mature level in managing their cybersecurity competence.
CIRCL (The Computer Incident Response Center Luxembourg) is also part of SECURITYMADEIN.LU, with the initiative to gather, review, report and respond to computer security threats and incidents. One of their services is information leak analysis, and you may check the list of reported detected information leaks in Luxembourg. The CIRCL team does malware analysis, reverse engineering, forensic analysis, and security vulnerability analysis. In the D4 Project and VarIOT, CIRCL monitors the activity of devices connected to the network. The D4 Attack Map allows visual representation of real-time SSH brute force attacks against such devices.
You may use their online tools for quick and straightforward document analysis (Pandora) or check and review suspicious URLs and websites (Lookyloo). You can also report an incident by contacting CIRCL via e-mail or phone or an Anonymous Incident Report Form.

While ANSSI and GOVCERT serve the public sector, SECURITYMADEIN.LU considers the support and service of the private sector to be its most important task. SECURITYMADEIN.LU also organises the information gathering and management of vital services provided by the Luxembourg Ecosystem, maps their availability within the ecosystem, and enhances potential cooperation among them. In collaboration with Luxinnovation, it also promotes the ecosystem within the Greater Region and in Europe.
The Agency has not only three departments, but also its mission is based on three pillars:
- Protect & Prevent against cyber threats
- Test & Improve your cyber resilience
- Detect & React to cyber incidents
All three pillars are essential for a successful defence against cyber threats, and they work hand in hand and protect cyberspace users.
12. Conclusions
“We need to take lessons learned from fighting terrorism and apply them to cybercrime.” - Robert Mueller
Cybercrime is part of our everyday lives; it affects everyone. Cybercrime is distinguished from other traditional forms of deviance by its methods, use of tools, environment, rapid spread, global, constantly changing nature, the significant extent of its damage in a short time, and its social perception. It is now an organised industry: it has a vast market and growing revenues of thousands of billions of dollars. Black Fog reported last year that cybercrime caused six trillion dollars in damage in 2021, double the 2015 value.
As the number of users grows, so does the number of cybercriminals lurking for users’ money. For this reason, however, it would be a shame to condemn digitisation or the expansion of the user base - this is not the fault of our devices.
The magnitude and severity of the damage caused and the degree of risk to individuals, institutions, and countries are significant. We might think that it could logically lead to a general social condemnation of cybercrime and the marginalisation of cybercriminals. On the contrary, certain types of cybercrime are accompanied by social recognition.
Movies and books are made about talented hackers, presenting them as brilliant users of the latest technologies. Hackers are often symbols of rebellion against the existing social order, actors at the forefront of social control and feedback. Such portrayals of hackers in the media affect the social perception of cybercrime, the self-image of cybercriminals, and, consequently, the effectiveness of curbing cybercrime.

Photo by Bermix Studio on Unsplash
Online attacks have become increasingly sophisticated in recent years: criminals are rapidly adopting and integrating new technologies when committing various crimes and using business models that are increasingly based on the use of the Internet. The exploitation of IT innovations can be observed, including, for example, illegal online commerce and the use of encrypted communication channels.
New technological advances have a significant and lasting impact on the nature of cybercrime. Traditional organised crime is already reaping the benefits of the Internet, such as engaging in illegal commercial activities in Darknet marketplaces and forums with a high degree of anonymity.
- European Cyber Security Competence Center (ECCC)
- European Cybercrime Center (EC3)
- National Information Systems Security Agency (ANSSI)
- Computer Emergency Response Team Luxembourg (GOVCERT)
- Computer Incident Response Center Luxembourg (CIRCL)
- Internet Organized Crime Threat Assessment (IOCTA)
- Europol’s National Central Bureau Luxembourg (NCB)
- Microsoft Threat Intelligence Center (MSTIC)
- Threat Landscape Report 2021 (ENISA)
- DDoS attacks in Q4 2021 (Kaspersky)
- Action against Cybercrime (Council of Europe)
- Serious and Organised Crime Threat Assessment (Europol)
- Human Insecurity (Podcast)
In addition, new cybercrime groups have emerged that use a specific business model to provide the tools and services needed to commit cybercrime.
Nowadays, crimes connected with cryptocurrencies are increasing (e.g. as a means of payment in fraud, cybercrime, extortion, illegal transactions).
One of the biggest challenges in the fight against cybercrime is the issue and establishment of jurisdiction, which often causes a very significant procedural problem: cybercrime is often cross-border or transnational. The perpetrator and the victim are often in different countries, and the crime is committed through an information system in a third country.
The anonymity technologies used by criminals complicate the situation because they can easily hide, making them geographically unidentifiable.
States follow the traditional territorial principle in determining their jurisdiction, but this is not the case for cybercrime. There are two crucial legal instruments available at the EU level: the GDPR obliges businesses to report data protection incidents without delay. The NIS Directive imposes obligations on essential service providers to maintain information and network security.
Closer cross-border cooperation and information sharing are needed to achieve an effective and successful fight against cybercrime. Facilitating increased international cooperation, especially between the private sector and law enforcement authorities, is essential for successful detection and effective investigations. If jurisdiction is established and the proceedings are successfully concluded, extradition may still be an additional problem.
Furthermore, prevention, especially user-centred education and dissemination, is paramount, as cybercrime could often be avoided if they were more careful. Legal regulation, investigative work, and technical protection of IT systems are necessary but not enough to stop cybercrime: great attention must also be paid to human factors and the social context. It is essential to understand the causes and circumstances of cybercrime and victimisation to take effective action against it.
The fight against cybercrime will continue in the future, cybercrime (as well as traditional crime) cannot be eliminated, but it must be tackled continuously by all possible means.

Photo by Shopify Partners from Burst
Revisions
- Original document: 01/05/2022
- First revision: 14/06/2022, Chapter 5.2.9 was updated