- 01 Nov, 2021
- Topic of the Month

1. Introduction
“The five most efficient cyber defenders are: Anticipation, Education, Detection, Reaction and Resilience. Do remember: “Cybersecurity is much more than an IT topic.” - Stephane Nappo
By the 1990s, computer networks and systems had reached a complexity that no single person could fully comprehend. The technologies used to interconnect the systems and provide IT services were thus divided into different disciplines.
Nowadays, specialists in one field are often unaware of the challenges and technological solutions of other fields. Different protection procedures can be applied, for example, for Windows and Linux systems, not to mention mobile technology, which requires a different approach.
The security of IT systems is no longer a purely technological challenge: more and more other disciplines are playing an important role, and cyber security issues in different disciplines require a slightly different approach.
Due to the complexity of cybersecurity, teamwork has now become an essential feature of experts. The willingness to cooperate is of paramount importance in managing IT security incidents nowadays, as the joint work of several disciplines would not be smooth in a stressful situation caused by a security incident.

Photo by John Schnobrich on Unsplash
This article addresses one of the group forms of preparing for technical challenges: technical cyber security exercises. Some of these deal with preparing for attacks (cyber security “war games,” also known as Red team - Blue team exercises) while others focus on searching for vulnerabilities; these are called flag capture (CTF) exercises.
Nowadays, both are needed because if we do not know the mindset of the attacker, we cannot develop an effective defence. They also complement each other, as it would be impossible to practice the defenders without simulated attacks.
2. Cyberspace and physical space
“If security were all that mattered, computers would never be turned on, let alone hooked into a network with literally millions of potential intruders.” - Dan Farmer
Cyberspace refers to the virtual computer world, specifically, an electronic medium used to facilitate online communication. An essential feature of cyberspace is an interactive and virtual environment for a wide range of participants.
In contrast, physical space is the perceptible tactile space that surrounds us. But why is this distinction important? During cybersecurity exercises, actors present in the physical space try to perceive changes in cyberspace and respond to them appropriately.
Cyberspace is man-made, and for this reason, we could assume that the rules and laws of cyberspace are given, that the events that take place there can be calculated and easily understood. But due to the complexity and global scale of the technology used and its rapid, unregulated development, this is unfortunately not true.
Photo by Markus Spiske on Unsplash
In many cases, events in cyberspace take place invisibly for users, and their effects are not directly perceptible. For example, a data theft or data leakage incident does not cause a directly perceptible loss, as the data remains available to the original owner (unlike in physical space, where the lack of what has been stolen is well perceptible).
In many cases, we use concepts in cyberspace (e.g., Trojans, viruses, worms, firewalls, etc.) that already exist in the real world because we try to draw parallels between the real world and cyberspace for easier comprehension.
Exercises are also required to carry out attacks. There can be a myriad of reasons why an information security mature organisation recognises the threats to its IT systems (and expects security incidents to occur) and, therefore, organises such exercises in preparation.
3. What is a cyber exercise?
“Cyber exercises do essentially the same “issue finding” as pentests, except they aim to find issues in how people work and not in the technology they use.” - Clear Cut Cyber
3.1. Cyber exercises
A cyber exercise is an event where the organisation models and tests its preparedness for various cyber incidents.
By doing cyber exercises, companies can understand and benchmark the impact of a cyber security incident and improve their responses to them over time. As they focus on business impacts, they can be used to decide where and when to apply risk controls such as pentests. Cyber exercises also allow companies to estimate the potential costs of various incidents and inform decision-making about cybersecurity investments.
The course of a cybersecurity exercise can be divided into several stages, and different groups can be defined in different ways to categorise these stages. However, in general, there are the following four major stages in a cyber security exercise:
It is not the purpose of this article to present the course of a cybersecurity exercise; instead, in the next section, we present the different types of exercises.
3.2. Pentests
A penetration test (also known as pentest or ethical hacking) is an authorized simulated cyberattack on a computer system performed to evaluate the system’s security. This type of test is performed to identify a system’s weaknesses (also referred to as vulnerabilities) with a defined scope. Penetration tests do not focus on the blue team’s ability to detect and respond, as the blue team is aware of the scope of the test performed.
Organisations focus on possible business impacts of a cyber incident as pentests of people and processes. The pentests’ indisputable advantage is that they allow organisations to develop and test their incident response procedures in a safe and controlled environment.
Pentests have different methods, like external, internal, blind testing, double-blind testing, targeted testing.
Source: What is Penetration Testing?
The concise video above answers the fundamental question of what a pentest is and its benefits.
4. Types of cyber exercises
“As we’ve come to realise, the idea that security starts and ends with the purchase of a prepackaged firewall is simply misguided.” - Art Wittmann
There are many different types of cyber exercises. Basically, any controlled examination of your processes can serve as an exercise. The choice of a suitable exercise depends on the objectives, the target group, and the available resources of the exercise. The objective and the participants should be decided before the method is chosen. Certainly, different exercises should be used for decision-makers (tabletop or functional exercises) and technical staff.
4.1. Tabletop exercise
Tabletop exercises are discussion-based meetings where team members meet in an informal classroom setting to discuss their role in an emergency and their responses to that particular emergency. Participants practice decision preparation and decision-making in a series of specific practical situations developed by the moderator. This type of exercise is often used for people who are in managerial positions to develop and test communication and improve decision making. Tabletop exercises have the following features:
- Applicable at all organisational levels
- Based on written material
- The most easily implemented exercise type
- The most common exercise type
- Easy to arrange, does not require many preparations
- The outcome is usually written answers to questions
- No technical environment is needed to organise it
- Not suitable for testing technical procedures and skills; therefore, it is necessary to combine it in a real or simulated environment exercises
- Suitable for creating, testing and developing information flow, decision preparation and decision-making processes
It is unnecessary to present the solution in a technical sense tested, and the exercise does not take place in real-time. The emphasis is on justifying the choices made and their longer-term applicability and minimising harmful side effects.
For this type of exercise, it is essential to check that existing plans are up-to-date and adequate to analyse the cause of the incident or to handle technical details. Tabletop exercises also work well as an introduction for more intensive exercises. This way, the participants can get in the mood for more complex or technical exercises or revise their knowledge and skills.

Photo by Campaign Creators on Unsplash
4.2. Root cause exercise
Suitable for forecasting problems and targeting risk management measures. A root cause exercise, also known as a pre-mortem, is organised similarly to a tabletop exercise. This type of exercise aims to identify the original causes (root cause) of risks resulting in a cyber incident. A cyber accident is presented to the participants, whose task is to consider which factors may lead to the described end result.
4.3. Functional exercise
Functional exercise is a more realistic method than a tabletop exercise. Time constraints, for example, are more stringent as participants process scheduled injections. Injects are individual messages that describe what happens during the exercise and thus influence its process. An inject may be any piece of information that moves the exercise forward, for example:
- Emails
- Phone calls
- Text messages
- Videos
- Newspaper articles
- Social media posts
- Technical reports
- Etc.
This type of exercise provides an opportunity for participants to communicate with each other and develop an up-to-date picture of how the events of the exercise affect the organisation.
The participants receive information about the events bit by bit, and social media can easily be included in the game utilising news items and social media messages commenting on game events. An efficient and dynamic control room plays a crucial part in a functional exercise. It is a separate area from the war room where the game planners direct the game. The game planners lead the game and send injects to the participants during the exercise.
4.4. Technical exercise
This type of cyber exercise requires plenty of preparation. The goal is to transfer the exercise results directly to the IT environment by collecting the experience of an emergency situation. During a technical exercise, various events, failures, and threats can be simulated. The exercise itself consists of identifying, investigating, eliminating and documenting the emergency.
This type of practice can get very close to actual operational models and processes; therefore, it is recommended to conduct technical exercises for organisations where the emergency response has already been examined, ensuring that their processes are effective and up to date. Alternatively, a technical exercise can also be implemented in a fully simulated environment.
Advantages of technical simulation exercises
- It mimics real situations well: the execution environment is similar to the real one
- It is excellent for assessing and evaluating technical skills, as well as for practising technical activities and routine acquisition
- The virtualised environment can be flexibly adapted to the needs, well scalable, quickly restored to a known good state
- The virtualised environment is easy to manage during practice
- The technical simulation allows you to perform specific and very diverse tasks
The disadvantages of technical simulation exercises
- The execution environment does not precisely match the real environment
- It requires careful planning and considerable preparation of 6-12 month
- Potentially requires a large organising team (practice depending on size)
- Because of the above, it can have high costs
- It is primarily useful for participants with adequate technical skills
- It is less common to repeat than tabletop exercises

Photo by Marvin Meyer on Unsplash
4.5. Capture the flag
In Capture The Flag or CTF, participants or teams earn points by finding “flags” in IT systems. These flags can be certain strings and letters that the participant enters the scoring system after finding them. The popular type of CTF is called ‘attack and defence’, where participants try to compromise the others’ systems and at the same time try to defend their own. Participants must have access to a protected system and conduct various investigations to discover the flags. CTF is a technical practice (and a type of cyber war game) in which competition between participants or teams plays a major role.
CTF exercises can also be organised in connection with various events or training days. The CTF challenge is an easy way to organise technical exercises initially. Public CTF training platforms are less suitable for examining an organisation’s own processes but work well to develop the skills of technical staff.
4.6. Major joint exercises
Cyber Security Statistics for 2021
- Cybercrime has increased by 600% due to the pandemic (PurpleSec)
- Ransomware cost $6 trillion annually by 2021 (PurpleSec)
- The frequency of ransomware attacks increases rapidly (2016 40sec, 2021 11 sec) (Embroker)
- The average cost of a ransomware attack on businesses was $133,000 (PurpleSec)
- 95% of cybersecurity breaches are caused by human error (Cybint)
- The worldwide information security market is forecast to reach $170.4 billion in 2022 (Gartner)
- The discovery of a security breach takes an average of 197 days (Embroker)
- Telecommuting increased the average cost of data leakage by $ 137,000 (TitanFile)
- 43% of cyberattacks target small businesses (Cyberint)
Instead of improving the organisation’s internal processes, the goal of joint exercises relates to the study of networks and value chains. Common situational awareness and coordination of the organisation’s activities and its partners are in the focus of the joint exercises.
Objectives often include the practice of exchanging information and a shared understanding of the attacker’s motives, methods of operation, and objectives. Some joint exercises are played as a technical game in which the participating teams compete with each other, protect their playing environment and score points.
Typically, participation in joint exercises is by invitation. If your organisation is invited to a joint exercise, you may want to take this opportunity, as joint exercises are excellent opportunities to learn about different practice methods.
Your organisation should define its own goals and be prepared as much as possible before the exercise. In this way, you can get the most out of the joint exercise. Particular care should be taken to consider the role and responsibilities of those employees sent to the exercise, ensuring that they best meet real-life situations.
4.7. International cyber exercises
For the tabletop, root cause, functional, technical, and CTF type of cyber security exercises, the implementation, purpose, and structure were different. In the case of joint exercises, the difference was that cyber security exercises no longer occur within a given organizational unit but are practised jointly by several otherwise independent organizations. During an international cybersecurity exercise (as its name suggests), there are international participants in the joint practice.
The structure, purpose, and history of the practice are usually entirely fictitious. The invited participants, organized into different groups (attackers and defenders), try to break each other’s line of defence for a given purpose.

Source: International Cyber Defence Exercise
On the one hand, this is an excellent opportunity for participants to test their cybersecurity skills and knowledge. These benefits are, of course, valid for all exercises. In this case, however, due to exceptional circumstances, the successful implementation of the exercise requires coordinated cooperation at the international level.
The most significant advantage of participating in such an exercise is that the participants can develop their international cooperation skills, expand their professional knowledge and international network.
4.7.1. Locked Shields
Locked Shields is the largest and most complex international cyber exercise in the world. It has been an annual event organised by the NATO Cooperative Cyber Defence Centre of Excellence (CCDCOE) since 2010.
Source: Locked Shields 2021
More than 2000 participants from nearly 30 countries took part in Locked Shields 2021.
5. Participants of exercises
“We discovered in our research that insider threats are not viewed as seriously as external threats, like a cyberattack. But when companies had an insider threat, in general, they were much more costly than external incidents. This was largely because the insider that is smart has the skills to hide the crime, for months, for years, sometimes forever.” - Dr Larry Ponemon
Participants of a cyber exercise can be grouped according to their roles, tasks and skills. The most commonly used terms are as follow:
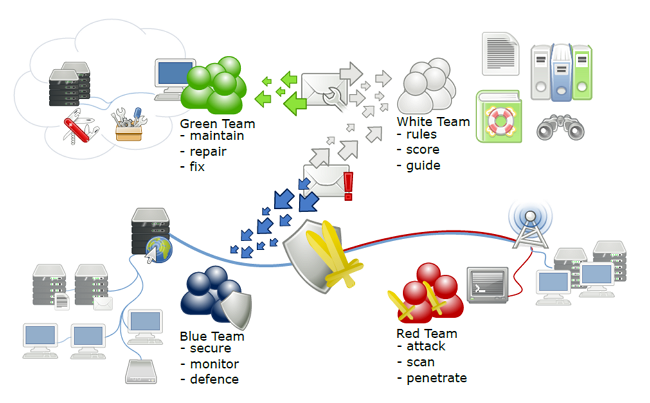
5.1. White team
The functions of a white team are as follows: referees, organisers, exercise managers and instructors. The white team provides the background story, the rules of the exercise, and so the framework for the Red and Blue teams’ competition. They assign tasks (called injects), provide basic hints to the Blue team, and act as instructors.
5.2. Blue Team
The team members are responsible for securing vulnerable networks and managing the attacks of the Red Team. These participants are usually grouped into several Blue teams.
Source: Red Team vs blue team Penetration Testing
5.3. Red Team
This team acts as an attacker in the cyber game and is made up of cyber security professionals. They do not accidentally attack targets in the Blue Team’s infrastructure but carefully follow a predetermined attack scenario to burden the Blue Teams equally. That is, the Red Team takes advantage of the vulnerabilities left in the Blue Team’s network. No other arbitrary means of attack may be used against the Blue Teams. They also cannot attack the service infrastructure. Based on the success of the attacks, the Red Team assigns penalties to the Blue Teams.
Source: Red Team vs blue team Penetration Testing
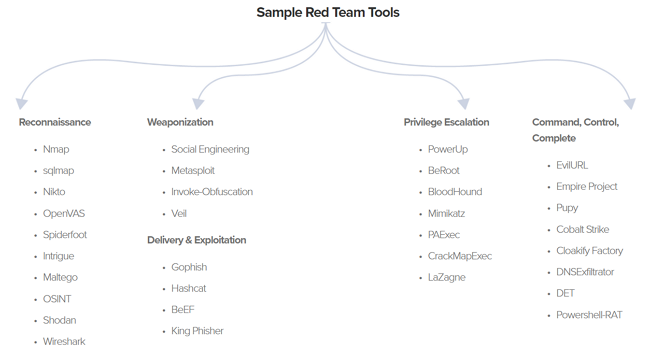
Members of the red team mimic a hacker’s mindset. Not only do they need to be very prepared and skilled, but they also need to think outside of standard processes (think outside of a box). The tools used to support the Red Team are diverse but can be categorised based on the process described below.
Source: Sample Red Team Tools
The short video below shows the difference between the red and blue teams. It also helps you decide which one to choose if you consider becoming a cybersecurity professional and the consequences of your decision.
Source: Red Team vs Blue Team | How to Get Started in IT
5.4. Green Team
Also known as the ‘background team’: they are a group of operators responsible for the exercise infrastructure (the sandbox in this case). They configure all virtual computers and networks, monitoring and scoring infrastructure. The Green team also monitors the sandbox’s health status and fixes crashes and infrastructure issues if needed
The schematic diagram below illustrates the interactions between the green, white, blue, and red teams and the tasks of the different teams during a cyber security exercise.
Source: Lessons learned from Complex Hands-on Defence Exercises in a Cyber Range (Interactions between the exercise participants)
Besides the above four, there may be Purple Teams (Blue Red Teams) and Tiger Teams. Purple Teams are like a mixture of the Red and Blue Teams: they have offensive and defensive functions. They usually make information exchanges between the attackers and the company defenders. The function of a Tiger Team is similar to the Red team. They are a team of professionals put together to solve a particular problem.
6. Planning an exercise
“Threat is a mirror of security gaps. Cyber-threat is mainly a reflection of our weaknesses. An accurate vision of digital and behavioral gaps is crucial for a consistent cyber-resilience.” - Stephane Nappo
The organisation’s leadership, the planners, the participants, and the facilitators play a crucial part in the exercise. The greater the practice, the more people are needed in different roles. Management should clearly express its commitment to the exercise and the lessons learned from it. Failure by managers to support the practice may have a negative impact on planning and design, as designers may feel that their working time is wasted on unnecessary work.
The lifecycle of an exercise can be divided into three stages: preparation, implementation and evaluation. Analysis of the exercise and putting the lessons learned into practice are particularly important for the better functioning of the organisation in the future.
The essential tasks and arrangements in planning and implementing an exercise are as follows:
6.1. Convening a planning team
Preparing a story and injects for the exercise requires meticulous planning and a lot of time. Members of the planning team (also known as a project group) should not be participants, as their advanced knowledge of the game’s events would inevitably influence the course of the exercise. The planning team should have a leader who convenes the team and takes responsibility for leading the exercise.
The team should have experts who have adequate knowledge of how the organization works and thus be able to select and plan tasks most effectively in terms of the content of the exercise. Each member of the design team should be familiar with their roles and responsibilities.
External experts or partners can also participate in the teamwork and take charge of different roles, like organising team meetings or assigning roles for the team members.

Photo by Brett Jordan on Unsplash
6.2. Selecting participants
Participants should be selected according to the objective of the exercise for which the team is preparing. In case the aim is to improve the operation of the production system in an emergency, employees working in production should be selected as participants. Similarly, if the goal is to improve leadership in a crisis, participants should involve at least the leaders and communication unit of the organisation. In case of a technical exercise, the organisation’s IT personnel and their supervisors should participate.
Depending on the type of exercise and the assignments involved, different personnel groups should attend the exercise. Also, the participants’ roles in the cyber exercise should be relevant to their real-life job descriptions.
6.3. Preparing for an exercise
The participants should be informed in advance of what accessories or tools they need: the invitation should clearly state what they should bring and what tools should not be used during the exercise.
6.4 Supporting tasks and observers
Employees of other organisations or departments may also be assigned to on-call roles during the exercise. Observers can also take part in the exercise as their work is necessary for the evaluation phase. An observer makes observations but does not interfere in the actions of the players. After the exercise, they also report their observations to the participants and the organisers. Observers should not communicate with the participants: they must not interfere with the players’ moves or decisions.
In the evaluation stage of the game, though, the observers give feedback to the participants and organisers. They may also submit a finalised memorandum on their observations at the end of the exercise. Alternatively, the observers are asked to fill out a questionnaire, in which they receive questions about the participants.
7. Why should you take part in a cyber exercise?
“Even the bravest cyber defence will experience defeat when weaknesses are neglected.” - Stephane Nappo
Many organisations understand the need to build protection and develop policies to reduce the risk and potential impact of a successful cyberattack, still only a few test rigorously these protection tools.
In this chapter, we look for the answer to the benefits of participating in a cyber security exercise. When we engage in an exercise, we always (either on a theoretical level or in practice) model a cyber security attack and practice what response should be given to them, which would be the most effective, the fastest, and so on.
Cybersecurity exercises are useful simulations of different cyberattack scenarios that allow organisations to gain valuable insight into their real response. In this regard, each time, participants test their actual and perceived cybersecurity preparedness and receive feedback during the exercise on how the previous two relate to each other.

Photo by Headway on Unsplash
Based on the results, the company can get a comprehensive picture of where to invest in workforce training and new technologies. Cybersecurity exercises can demonstrate the effectiveness of a defence strategy or highlight vulnerabilities that require immediate attention.
For participants (whether security teams or management), participating in as many exercises as possible provides a sense of routine, reduces stress, and forges their team better. In a real-life situation, the experience gained is an invaluable advantage in crisis management over companies that have not been involved in similar activities and lack routine, consistency and experience.
It is also true in crisis exercises management that theoretical knowledge is worth very little without experience. In the absence of experience, even the best-trained people in theory only model what they have learned.
Do not forget that problem-solving skills can best be developed only in real situations where unexpected and sudden events occur and often need to be improvised when selecting responses. Better team cohesion and a higher level of theoretical and practical preparation have a beneficial effect on morale.
The effectiveness of the response to cyber threats is primarily determined by human factors such as professionalism and the best possible team spirit. Therefore, it is easy to see that a company’s resilience to cyber attacks is positively affected by the collaborative work of experienced team members. In summary, the following benefits may come from participating in a cyber security exercise:
Improve your response
Cybersecurity exercises provide you with an opportunity to improve your response to future attacks.
Train people
An exercise provides employees with hands-on experience in handling cyberattacks.
Increase threat awareness
Raising awareness within the company is the first step to tackle cyber threats, as cyberattacks are inevitable.
Identify possible external needs
There are very few companies that can handle any attack scenario professionally without outside help. Cybersecurity practice can point out which attack scenario requires outside help and how quickly external expertise can be provided.
Identify your strengths
Most people pay attention to the weaknesses and problems that arise during a cybersecurity exercise, but recognising what works well for your organisation is also essential. If we know something is working, then that method can be used in a real-life situation.
Identify your weaknesses
Cybersecurity exercises can expose technical vulnerabilities and reveal the professional or theoretical shortcomings of participants. Identifying vulnerabilities is very important in order to develop recovery plans and take immediate actions in the event of a possible cyberattack.
Collect metrics
It is imperative to have data on how quickly the various aspects of an attack need to be handled, how effective the defence should be, and how quickly the company can respond. These metrics are essential for developing a future strategy against cyber-attacks; otherwise, we are only groping in the dark.
Setting costs and deadlines
In preparation for attacks, several assumptions and estimates arise about what resources are needed to deal with different scenarios and how long it takes for normal operations to recover after the attack.
Update your policies
A cybersecurity exercise may also be suitable for reviewing your current policies and standards to see how effective they are. Regular policy reviews are imperative, and security exercises can provide constructive evidence for review.
Avoid Non-Compliance Risks
The potential costs of violating legal, regulatory, or contractual requirements are significant, even if the violation is unintentional. Cyber security exercises can help uncover irregularities, provide an opportunity to correct them and avoid unnecessary legal and financial exposure.
A cybersecurity exercise can have several purposes, of which, without wishing to be exhaustive, we may mention the following:
- assessment of current incident management capabilities
- evaluation of training results
- testing current incident management processes
- validation of new processes
- routine acquisition, practice
- public awareness formation
8. ENISA - Cyber Europe
“If you think technology can solve your security problems, then you don’t understand the problems, and you don’t understand the technology.” - Bruce Schneier
8.1. Cyber Europe
ENISA manages a programme of pan-European cyber exercises called ‘Cyber Europe’. Cyber Europe is a series of EU-level computer incidents and crisis management exercises for the public and private sectors in the EU and EFTA Member States, held every two years since 2010.
Cyber Europe exercises are simulations of large-scale cybersecurity events that may turn into cyber crises. Due to the global pandemic, Cyber Europe 2020 has been postponed and will be held in the summer of 2022 as Cyber Europe 2022 (CE2022).
Because of the pandemic, it is not surprising that the Cyber Europe 2022 scenario will revolve around healthcare. As part of cybersecurity practice, participants should analyse and resolve real-life health-related technical events, forensic and malware analysis, and non-technical events.
Cyber Europe, among many other things, is different from other cybersecurity practices in that incidents turn into a serious crisis at all levels: local, organisational, national and European. Participants need to develop business continuity plans and crisis management procedures, and solutions to European challenges need to be addressed in close cooperation with other actors.
8.2. Cyber Exercises Platform
The Cyber Exercise Platform (CEP) is a test environment of ENISA where participants can conduct complex cyber security exercises and improve their response to cyber security attacks and challenges.
The main goal of CEP is to enable users to gain international hands-on experience in a well-thought-out test environment instead of local cyber security practices.
This platform supports the management of complex exercises and includes data on upcoming and past exercises and a sandbox environment.
9. Luxembourg Cyber Range
“Luxembourg has become a key ICT actor in the European Union. We have invested massively in connectivity and IT infrastructures over the last years, with the aim of becoming a ‘smart nation’ and one of the most dynamic digital economies in Europe. All of this requires protection, and with our national cybersecurity strategy, we are aiming, together with NSPA and CybExer, at building a highly capable training environment that can prepare our cyber security teams for the most advanced threats.” - Ben Fetler
On October 20, 2021, François Bausch, Deputy Prime Minister and Minister of Defense, launched the “Cyber Range” platform for defence in Luxembourg. With his announcement, a cooperation with the “Luxembourg Cyber Security Competence Center” of the cybersecurity agency SECURITYMADEIN.LU has been initiated to complete the cyber training program. The “Cyber Range” platform is an integral part of Luxembourg’s defence efforts and Luxembourg’s Cyber Defense Strategy.
A cyber range is a simulation environment for IT systems that enhances an organisation’s cyber defence capabilities through training and testing activities. The Luxembourg Directorate of Defence recently developed its cyber defence capabilities and established a cooperation with the NATO Support and Procurement Agency. The Directorate also awarded an Estonian cyber security company, CybExer, a three-year contract to acquire the cyber range. Luxembourg is launching its cyber range in October 2021, and it allows cyber experts to train in a virtualised but realistic environment.
In the latest part of the Lëtz Talk About Cyber series, Pascal Steichen, CEO of SECURITYMADEIN.LU, talked to Ben Fetler, Cyber Defense Principal Advisor at the Luxembourg Directorate of Defence. When asked what the cyber range is, Ben made the following analogy:
“You can compare it with a flight simulator where you can simulate and train different scenarios of attacks in a realistic environment.”- Ben Fetler
As Ben Fetler said, the cyber range is not just for Luxembourg professionals: it is more than an international competence center with the objective that experts get to know each other and are able to work together in the event of a major crisis efficiently.
Watch the full interview below:
Cyber ranges represent complex virtual environments: they are used for cyberwarfare training and forensic analysis, resilience improvement, and other cyber-related issues.
10. How can SECURITYMADEIN.LU help?
“There’s not a ‘one and done’ solution for cybersecurity, no silver bullet as we like to call it. With cyber, there needs to be continuous caring and feeding of the program. It’s a program that requires ongoing improvement. And that’s something very important to explain to the board.” - Zaki Abbas
10.1. SECURITYMADEIN.LU
SECURITYMADEIN.LU fosters new market segments with high added value (for example, cyber exercises, threat intelligence or cyber insurance). In collaboration with the leading players from the national information security sector, SECURITYMADEIN.LU promotes and delivers high-quality tools & services accessible to municipalities, SMEs and companies of all sizes by developing new solutions and competent services for the Luxembourg economy.
10.2. C3 - Cybersecurity Competence Center Luxembourg
The Cybersecurity Competence Center Luxembourg is part of SECURITYMADEIN.LU. It helps organisations reach a mature level in managing their cybersecurity competence. It can be developed both at the individual and collective levels. Competence stays a problematic concept for organisations to grasp. It is the combination of technical skills, know-how and experience. Therefore, the C3 strengthens competence building and cybersecurity awareness through a set of audience-centred and personalised activities. These include the delivery of experience-based cybersecurity awareness training, cybersecurity crisis simulation exercises and specific technical courses.
C3 also contributes to strengthening the available pool of cybersecurity talents through various activities, including the development of challenges-based initiatives, its support to cybersecurity capacity-building projects, and its participation in cybersecurity events organised by SECURITYMADEIN.LU, the Lëtz Cybersecurity Challenge, involvement in partners’ cybersecurity events, press and communications and other missions.
C3 identified the need for testing as a requirement for organisations to identify their gaps in terms of cybersecurity competence. Testing is a broad domain, starting with fully automated tests of specific infrastructure elements and going up to sophisticated and highly manual penetration tests.
C3 considers the human dimension as the cornerstone of a cybersecurity system. We teach through experience to develop competence:
- Train by doing (Experience-based)
- Develop reflex action
- Grow individual and collective competence in cybersecurity crisis management
Source: Room#42 — 10 Things To Know About The Cyberattack Simulation Game
The ROOM#42 simulator is one of the vital training infrastructures of C3 and a unique concept in Europe. Its specific immersion training approach brings up to 8 trainees in a one-hour realistic cyber-attack simulation, offering deep and comprehensive learning based on an intense experience. It is an innovative and unique concept in Europe, through which “participants” are in a cyberattack and have to react to it.
ROOM#42 demonstrates the need to consider people and competencies as vital elements of cybersecurity.
Key competence and capacity in the incident and crisis management lack many organisations, as show the lessons learned from 3 years of experience with C3’s ROOM#42. In 2020, beyond the exercises conducted, the C3 developed new ROOM#42 scenarios aimed at public administrations as part of its partnership with INAP.
10.3. CASES
CASES (Cybersecurity Awareness and Security Enhancement Services) is also part of SECURITYMADEIN.LU. It has multiple services available to the public to raise awareness. The goal is to give every organisation the necessary tools (Fit4Cybersecurity, CASES Diagnostic, Monarc, TACOS, etc.) to define its risk maturity and improve it.
Being aware of the risks and threats is the first step in recognizing them and choosing the proper defence. In addition, in the fight against cyber security threats, human capabilities such as the willingness to cooperate, quick decision-making in stressful situations are becoming more and more valuable.
10.4. CIRCL
CIRCL (Computer Incident Response Center Luxembourg) gathers, reviews, reports and responds to computer security threats and incidents. CIRCL is the CERT for the private sector, communes and non-governmental entities in Luxembourg.
This group of highly trained IT experts takes the stage when the trouble has already happened. CIRCL provides a reliable point of contact for users, companies, and organizations based in Luxembourg to handle attacks and incidents.
This team acts like a fire brigade, with the ability to react promptly and efficiently whenever threats are suspected, detected, or incidents occur.
11. Conclusions
“As cybersecurity leaders, we have to create our message of influence because security is a culture, and you need the business to take place and be part of that security culture.” - Britney Hommertzheim
At the NATO Summit in Warsaw in June 2016, cyberspace was officially declared the fifth battlefield besides the previous four physical dimensions (land, air, sea, cosmic).
Priority must be given to preventing threats from cyberspace, responding to events that have already taken place and defending.
Preventing various cyber attacks is a complex task that also requires cooperation at governmental and organisational levels. The first step in developing cybersecurity is training and education, of which cybersecurity practices are an integral part.
Cybersecurity threats pose a significant risk to the survival and success of modern companies. Every company, regardless of size, is constantly at risk of falling victim to destructive attacks such as phishing, DDoS or extortion programs. Every organisation needs to use incident management to develop and continuously maintain capabilities. These capabilities should be identified, developed and measured at all organisational levels.
In this regard, cybersecurity practices play a crucial role in modelling and testing responses to cyber threats and thus preparing company employees to respond to a potential cyberattack.
Such exercises aim to improve an organisation’s structure, procedures, communication, and coordination through lessons learned.