- 04 Sep, 2022
- Topic of the Month

1. Introduction
“Just as drivers who share the road must also share responsibility for safety, we all now share the same global network and thus must regard computer security as a necessary social responsibility. To me, anyone unwilling to take simple security precautions is a major, active part of the problem.” - Fred Langa
Cyberspace has become one of the most defining dimensions of our everyday life: it affects every segment of our lives, not only at the individual- but also at the national and global economic levels.
Services in cyberspace are becoming more and more dependent on us. The outage of these systems and services can cause severe disruptions in our everyday life. Today, they may also seriously threaten people’s lives in addition to material damage. Cyberspace and the security to be implemented in it are thus of fundamental interest to all countries. The importance of cyberspace can no longer be questioned. Accordingly, challenges and threats in cyberspace must be addressed strategically.
The answers to this question are most reflected in the strategic ideas of individual countries about national cybersecurity since, in addition to the global powers, smaller countries are also trying to find solutions to security issues related to cyberspace at the national level.

Photo by Christina @ wocintechchat.com on Unsplash
European countries used two approaches when developing their cybersecurity strategy. Some countries approached the development of their cybersecurity strategies from the information society and its security aspects. In contrast, others approached it from the point of view of critical information infrastructures and their security issues.
However, cyber threats take on new forms almost every day, and therefore countries also have to think about their responses to constantly changing challenges. For this reason, many countries are developing newer and newer cybersecurity strategies. This is not surprising since the well-being of a given country and the people living there depends mainly on the ‘health state’ of the cyberspace surrounding them.
The question arises whether the security of cyberspace can be created at the national level, as geographical boundaries are complicated to interpret in cyberspace. It is easy to see that taking national borders as a basis for cybersecurity is not an appropriate approach. Cybersecurity can be implemented at a high level and satisfactorily if it is unified and regulated on a larger territorial scale, including more and more countries.
At the same time, when developing national cybersecurity strategies, it cannot be neglected what questions the given strategy addresses and how and in what form it intends to deal with cyberspace challenges. Therefore, it is necessary to consider the recommendations made by international organisations, which can serve as a basis for developing a country’s national cybersecurity strategy. In this way, the possibility can be created that although countries make cybersecurity strategies at the national level, they are nevertheless created in harmony with each other and based on strategic ideas acting in the same direction.

Photo by Shamin Haky on Unsplash
Cyber threats are occurring globally in increasing numbers and frequency, including large-scale cross-border cybersecurity incidents and pressure cyber operations. The Council draws attention to the need to strengthen cybersecurity and the fight against cybercrime in the EU and partner countries through international cooperation and assistance in cyber capacity building.
In cyberspace, strengthening reliability and security is essential to exploit the potential inherent in digitization and prevent new threats and attacks.
2. Strategic challenges and threats in cyberspace
“Technology trust is a good thing, but control is a better one.” - Stephane Nappo
Assessing cybersecurity threats is extremely important, but at the same time, it is also a complicated task. The reason for this is twofold: on the one hand, new attack methods appear every day, and on the other hand, in many cases, it is difficult to distinguish between the different levels and volumes of threats.
In any area of life, it is true that ‘unity is strength’. This is also true for cybersecurity, which can only be implemented effectively in stable cyberspace based on international cooperation.
In order to implement cybersecurity, it is necessary to have all the technical, regulatory and human tools and capabilities that contribute to the creation and maintenance of security with a whole series of activities during the application and operation of the digital ecosystem.

As per the Embroker Team, the top 10 cybersecurity threats in 2022 are as follows:
- Social Engineering
- Third-Party Exposure
- Configuration Mistakes
- Poor Cyber Hygiene
- Cloud Vulnerabilities
- Mobile Device Vulnerabilities
- Internet of Things
- Ransomware
- Poor Data Management
- Inadequate Post-Attack Procedures
What they all have in common is that although these are technical threats, there is always the human factor somewhere, the possibility of making mistakes. Therefore, we cannot fail to emphasize that the development of knowledge and raising awareness in connection with the development of cybersecurity is unavoidable, no matter what kind of advanced technology we are talking about.
3. What is cybersecurity capacity building (CCB)?
“Cybersecurity capacity building is the development and reinforcement of processes, competences, resources and agreements aimed at strengthening national capabilities, at developing collective capabilities and at facilitating international cooperation and partnerships in order to respond effectively to the cyber-related challenges of the digital age.” - Barbero and Berglund, 2021
In international cyber capacity building projects, countries, companies and organizations help each other across borders to develop functioning and accountable institutions that respond effectively to cybercrime and strengthen the country’s cyber resilience.
Based on what was described in the previous chapter, there is a considerable need for this. There are also countless articles about the enormous rate at which the number of cyber attacks is increasing and the massive damage they can cause. What used to be just a prank and only affected a few people can now affect millions and cause billions in damage.
Cybersecurity capacity building (CCB) is a form of international cooperation to share the knowledge and skills needed to protect the digital environment. This collaboration involves many different communities of practice, from technical incident responders to cybercrime police to civil society educators.
The parties share a common interest in helping governments, organizations and individuals in countries outside their own to protect their safe, secure and open access to their digital environment.
During lengthy negotiations, the countries participating in international CCB agreed that the use of these capabilities should be limited and regulated by international law and the norms of responsible state behaviour. They also agreed that further measures are needed to build trust between countries to reduce the chances of misunderstandings and ease differences.
The short animation below articulates what CCB is and outlines its importance in maintaining international peace and stability in cyberspace.
How does capacity-building make cyberspace better? - Chatham House (YouTube)
Just as building national cyber capacity improves a country’s ability to detect, investigate and respond to threats, so can countries participating in the CCB project improve these capabilities by working together to improve and maintain the health of the common cyberspace.
4. Where does cyber capacity building come from?
“We are vulnerable in our military and our governments, but I think we are most vulnerable to cyber attacks commercially. This challenge is going to significantly increase. It’s not going to go away.” - Michael Mullen
International cybersecurity capacity building emerged in the mid-1990s as a mechanism for countries and organizations to help each other across borders to protect the safe, secure, and open use of the digital environment.
Although cyber security capacity building has a history of 20-30 years, it still does not have a commonly accepted definition. The European Cyber Security Agency (ENISA) compared the definitions and proposed the following as a standard definition of cyber security:
“Cybersecurity shall refer to the security of cyberspace, where cyberspace itself refers to the set of links and relationships between objects that are accessible through a generalised telecommunications network, and to the set of objects themselves where they present interfaces allowing their remote control, remote access to data, or their participation in control actions within that Cyberspace.” - (ENISA et al. 2015, 7).
Some people replace ‘cybersecurity’ with ‘cyber’ while others use ‘capacity development’ instead of ‘capacity building’. Because there are many variations of the term cybersecurity capacity building, there is no standard definition.
However, more important than defining the definition is that this type of international cooperation, which seeks to raise the level of cybersecurity, is growing. CCB began sometime between the 1990s and 2000s.
At the same time, there is a limited amount of published data available on program investments, and there can be large differences between them, depending on where the data comes from. For example, as per the European Commission’s International Cyber Capacity Building: Global Trends and Scenarios report, at least 250 CCB projects have already been implemented in 2021. However, according to Cybil, we exceeded the annual number of 250 projects already in 2018, and in 2019 and 2020 there were around 300 CCB projects.
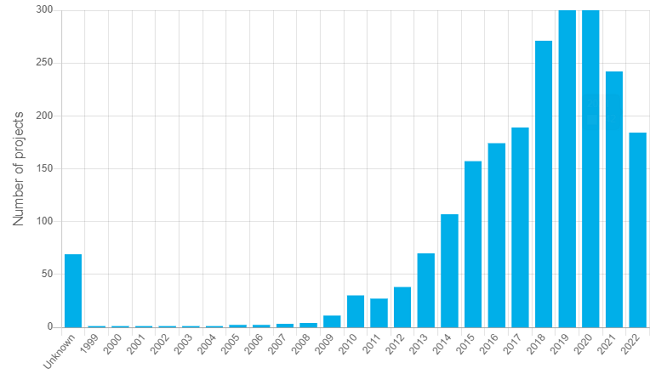
Number of CCB projects per year between 1999 and 2022 by Cybil
The number of countries and organizations participating in capacity building, as well as the goals of the projects, has expanded over time. The projects initially focused on cybercrime, but this has expanded to include incident response, protecting critical national infrastructure, raising public awareness, and many other objectives.

Photo by Lars Kienle on Unsplash
.
5. Why developing cybersecurity capabilities is necessary?
“Threat is a mirror of security gaps. Cyber-threat is mainly a reflection of our weaknesses. An accurate vision of digital and behavioural gaps is crucial for a consistent cyber-resilience.” - Stephane Nappo
There is a growing need for an advanced and coordinated response in cybersecurity as the number, scale and consequences of cyber attacks continue to grow, seriously affecting our security.
The EU cyber security strategy contributes to realising a secure digital economy and society. Cybersecurity communities, including civil, law enforcement, diplomatic, cyber defence communities, and private sector partners, often operate in isolation. In order to act effectively against large-scale cyber attacks, information and knowledge sharing between these communities are essential.
All this would be true in peacetime when there are no problems, economic development is unbroken, no hunger, drought, global warming, lack of raw materials, migrant crisis and health crisis.
In an age when we have not yet recovered from the pandemic, but a war is taking place in our neighbourhood on the European continent with its many catastrophic effects, security in both physical and cyberspace is increasingly valued.
The economic and social destabilization, the migrant crisis, the lack of parts and chip shortages due to the stuttering logistics supply chains, the lack of food and the resulting increasing hunger present us with a chaotic and destabilized Europe and the world.
In such circumstances, collaboration, selflessly helping and supporting each other, is our primary human duty. One manifestation of this can be the expansion of cyber capacities and the sharing of resources and information, which are vital to increase cybersecurity.

Photo by Hannah Busing on Unsplash
6. Types of cybersecurity capacity-building frameworks
“Cybersecurity is a subject that requires logic, knowledge, thought and commitment.” - Ian R. McAndrew
When discussing cybersecurity capacity-building frameworks, we also need to talk a little about the evolution of CCB projects over time. At the start of CCB projects, it was widely believed that cybersecurity capacity building was either for developing countries or for achieving development goals.
One of the earliest and still quite common forms of cybersecurity capacity building is when a developed country in the North supports a poorer beneficiary country in the South (Type 1: Nort-to-South).
The second type of capacity-building framework gives a slightly more nuanced picture when capacity-building projects also appear between southern countries (Type 2: North-South-South).
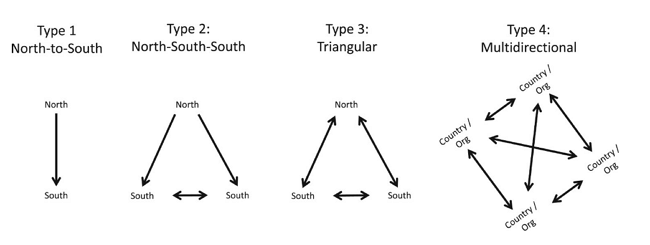
Frameworks for cybersecurity capacity building – Journal of Cyber Policy
The third type of framework (also called a triangle) represents the next level since, in this case, capacity-building projects between poorer countries already positively affect the capacity of the more developed partner.
The most advanced framework for cybersecurity capacity building is the multidirectional framework (Type 4), in which any country can provide assistance to another country without distinguishing itself according to the more developed or less developed North or South or any other definition.
The network of connections between the actors of cybersecurity capacity building is very complex, and in reality, the multidirectional framework best describes the real situation.
7. Characteristics of cyber capacity building
“As the world is increasingly interconnected, everyone shares the responsibility of securing cyberspace.” - Newton Lee
International cyber capacity building projects may take many forms, yet there are common characteristics to describe them. In this chapter, we look at these characteristics of CCBs to understand them better.
7.1. Cyber capacity building should be a long-term and sustainable framework
Governments, international organizations and the private sector increasingly recognise the importance of capacity building in cyberspace. Although actors are under pressure to achieve quick results, capacity building should not be treated as a sprint but as a marathon: the ultimate goal is to create a resilient ICT space that supports the economy and society in a long-term and sustainable way.
7.2. It proceeds from smaller units to larger ones
Cyber capacity building efforts should be designed as a chain process, where small initiatives contribute to a larger project. Therefore, cyber capacity building should always progress from smaller to larger units.
7.3. It requires clear communication and common language
Cybersecurity needs to be demystified. The growing reliance on ICT in all areas of life is completely transforming our societies and governance systems. Since cybersecurity permeates every aspect of life today, many people interpret cybersecurity itself in many different ways.
References to cyber security are often politically influenced, which also causes problems in the implementation of CCB projects. Therefore, open and clear communication must be incorporated into all capacity building efforts.

Photo by Campaign Creators on Unsplash
7.4. It is not only about security
More and more countries rely on the Internet for governance and services (e-government, e-health, e-education, online banking, etc.). Therefore, cyber capacity building is not only about security but also dramatically impacts social and economic development worldwide.
7.5. It presents different challenges for donors and beneficiaries
One of the biggest challenges for donors is the development of scalable models for capacity building, i.e. how a specific project can be developed sustainably in the future. Another task for donors is to define the strategic framework for capacity building, involve stakeholders, and build and maintain local and national coordination with the appropriate partners.
The most significant challenges for the beneficiaries are implementing the plans, determining priorities and activating the managers involved to implement the project successfully.
7.6. Donors and beneficiaries have different priorities
The priority aspects for donors during the implementation of a capacity-building project are to increase the access and skills of people in the donor country to the Internet, to spread the safe Internet model, and to create legal frameworks that protect the rule of law and human rights.
On the other hand, the supported parties see essential benefits in realising a capacity expansion project in personalized training, acquiring the necessary knowledge and skills, and constructing the appropriate IT infrastructure.

Photo by Alex Kotliarskyi on Unsplash
7.7. Although there are many common features, each project is unique
In order to develop a framework for capacity building in a given country or region, it is also necessary to consider the country’s cultural, political and social characteristics. Although the overall approach and the specification of the objectives are often similar, the individual components of the implemented frameworks are always case-specific
Concerning cyber capacity expansion, the existence of national cybersecurity strategies is vital, the elements of this strategy are generally similar, but the level of their implementation is usually different.
During the development of the framework, the challenges of creating policies and creating legislation are solvable problems. However, we must not forget that the project participants must take responsibility for the contents of the framework. The beneficiaries need to act in writing and action so that a given capacity expansion project can be successfully implemented.
7.8. It needs international coordination
In the case of cyber capacity building projects, international cooperation and division of labour are essential. On the one hand, cyber threats know no geographical boundaries; on the other hand, international communication, relationship building and coordination are necessary to use the investment fully.
Participating partners in the project (donors and beneficiaries) should make significant efforts to learn and recognise good and bad practices, share information about capacity building efforts, and coordinate resources appropriately.

Photo by Mimi Thian on Unsplash
A critical condition for the implementation of a successful project is that the various actors in the project (governments and actors within governments) recognize the needs, successfully identify the failures and better understand the specific conditions influencing the results.
International cooperation is needed to map the resources needed to implement the capacity building project and to use the resources more efficiently.
It is beneficial if the governments of the partner countries provide a platform that facilitates the monitoring of the distribution of resources and thus ensures the transparency and measurability of the project.
7.9. It requires stakeholders’ cooperation
Cooperation can bring various advantages for those involved in the cyber capacity expansion project. The private sector has an important role to play in raising cyber security awareness and helping governments understand the importance of cyber issues. Civil society organizations are also essential in identifying the needs of capacity building efforts, including the social and economic impacts of Internet proliferation.
After the implementation of the project, it is a serious challenge for the participants to find out how to report incidents. The situation in effective incident management is often complicated by the lack of trust between the actors involved and the unclearly defined procedure regarding whose duty it is to report a specific incident and how.
7.10. It requires an appropriate priority level
In many supported countries, cybersecurity is not prioritized at an adequate level. Many times it is because there are more pressing issues for them whose presence is visible: such as food security (hunger), adequate hygienic conditions, crime, infrastructural backwardness, etc. In contrast, cybersecurity risks are less visible and pressing: risks that have not yet been materialized and had no impact falls into the less important category.

Photo by Pexels on Pixabay
Cybersecurity risks have already been recognized in most countries, and they are also aware of their highly harmful potential effects. The main problem that prevents them from changing the situation is mainly the lack of money, inadequate infrastructure and the availability of the right amount and quality of human resources.
7.11. It requires constant development
Capacity building programs must evolve to align objectives with the changing environment, needs, and maturity of a given actor’s cyber policy framework. While trial and error must be part of the effort in the cyber capacity building process, learning mechanisms must be involved in the process, and participants must be ready to adapt to a changing environment.
Among the conditions for a successful project are criteria such as open international cooperation, well-thought-out strategy and goals, flexibility, adequately trained and numbered personnel, an adequate technical network and IT infrastructure, etc.
8. Challenges in cyber capacity building
“A modern cybersecurity program must have Board and Executive level visibility, funding, and support. The modern cybersecurity program also includes reporting on multiple topics: understanding how threats impact revenues and the company brand, sales enablement, brand protection, IP protection, and understanding cyber risk.” - Demitrios ‘Laz’ Lazarikos
Cyber capacity building faces many challenges. In theory, cyber capacity building allows more developed nations to share their knowledge with developing countries and help them build their cyber capacity framework. In reality, however, most challenges have only one root: how to make it happen.
Most of the problems are more with how the CCB project is implemented. The practical implementation of cyber capacity building requires a horizontal approach in different areas of development policy, focusing on improving governance, protecting and developing infrastructure, and knowledge transfer.
Many national and international organizations are trying to expand cyber capacity in developing countries. The approaches and focus of these organizations related to cyber capacity expansion can be very different geographically and in terms of topic.
One of the challenges is establishing the infrastructure, institutional stability, and background as soon as possible while constructing cyber capacities and then integrating them into the local system.
Before carrying out the capacity building project, it is necessary and helpful to learn from the capacity building experiences of other sectors. Projects created and implemented mainly by external donors are less likely to be successful and sustainable in the long term than projects owned internally, in which representatives of the supported countries are also more involved.
8.1. Challenges for developing countries
8.1.1. Access versus IT infrastructure
The number of users and access to cyberspace is growing faster than the frameworks, and the IT infrastructure used to support it. In order to solve the problem, the IT infrastructure must be developed, capacity must be expanded, and the critical infrastructure must be

Photo by George Slabov on Unsplash
8.1.2. Affordability
In general, host countries lack the resources needed to build and maintain the capacity to implement secure cyberspace. In connection with a CCB project, the assistance provided to ensure and maintain cyberspace capacity and create infrastructure can only be used to a limited extent by the host country if it cannot maintain these mechanisms and use the assistance offered. For this reason, the challenge is often to put a specific developing country in a position to properly use the offered assistance even before the CCB project is launched.
Creating an appropriate framework and infrastructure that can be sustained long-term is essential to a successful CCB project. Training the host country’s personnel is critical for the host country to maintain its IT infrastructure in the long term.

Photo by Rachel Claire on Pexels
8.1.3. State and private sector cooperation
Close cooperation between the state and the private sector is essential to achieve adequate security in cyberspace. The task of the government, among other things, is to create an appropriate legal framework and act supportively with the private sector participants. Part of this is building an environment where private enterprises can develop healthily and are motivated to prioritise cyber security.
Private sector players need to be aware of the threats they face in cyberspace and the costs of not securing their cyber systems. Education, organization of training, sharing of information, development of employees’ awareness, and participation in courses are all steps that raise the level of cyber hygiene and increase the security of cyberspace in the given country.
8.1.4. Building knowledge and awareness
The increasingly intensive use of cyberspace and the ever-increasing number of users make it essential to educate and raise awareness of the risks of threats related to cyberspace. It is in the primary interest of every country that their computer users use cyberspace consciously and have an adequate level of knowledge in the field of cyber security and cyber hygiene to achieve a sufficient level of online protection.
For the success of a cyber capacity expansion project, it is also essential for the partners to have an adequate level of knowledge in cybersecurity. As a first step, the government of the host country needs a comprehensive understanding of the need for cyberspace security and the fundamental technological challenges and development needs.
The government must provide the legal framework in which a CCB project can be successfully implemented. In addition to the government, all those organizations and partners that participate in a given CCB project must be similarly committed and prepared for the successful implementation of the project.

Photo by Ben White on Unsplash
8.1.5. Legal framework
The appropriate legal environment is essential for creating secure cyberspace. There is no dispute between the partners about the necessity of the legal framework. Instead, disagreements arise as to how well these laws can be integrated into the legal framework of the given country and how permissive or strict they should be. If they are very strict, observing and enforcing them is cumbersome. At the same time, a weakly regulated framework does not provide adequate protection and background for these projects to be implemented safely and properly.
8.2. Challenges for donor countries
8.2.1. Lack of adequate data
The first and most significant challenge for a donor country is to create the right image of the host country participating in the CCB project. The background to this is usually that the data is unavailable in sufficient quantity and quality. Therefore, it is laborious to draw realistic conclusions about what level of cyber security the host country has achieved, what it needs and how it could be implemented.
It is difficult to collect data through the country receiving aid since it depends on the country in question, what data it shares in what detail, and this data does not always cover the reality.
Photo by Stephen Dawson on Unsplash
8.2.2. Finding suitable partners
Another challenge is finding the right CCB partners willing to put cybersecurity and capacity building on their agenda and make it a priority. The number of government and private sector people who have recognized the importance of cybersecurity capacity building and are willing to deal with it alongside or before other development projects is often limited.
Before starting projects or in the initial stages, mistrust and security issues can hinder functional cooperation between potential partners. Finding suitable partners is a time-consuming process: it requires long-term relationship building, openness, honesty, and the establishment of a friendly relationship.
During relationship building, laying the foundation stones of cybersecurity and building awareness are essential steps in launching a successful CCB project. In addition, political stability within the host country and the willingness to cooperate with partners are necessary conditions for realising a long-term fruitful relationship and project.
8.2.3. Communication and cooperation
Clear and honest communication between partners participating in the CCB is indispensable for successful cooperation. Good communication with the recipient countries must be established to ensure appropriate assistance goes where and when needed. This is just as true between the assisting and the host country as between all other partners (be they host countries, organizations, members of the private sector, etc.).
8.2.4. Training
Education and awareness-raising are needed in the field of IT, especially in relation to cybersecurity. IT preparedness can ensure the safe and efficient use of the capacities for the host countries.
Without this preparation and knowledge, there is a risk that the host countries will become dependent on the donor countries and will not be able to maintain their cyber capacities in the long term. This situation must be avoided at all costs because, as the saying goes, ‘You have to teach people to fish, not always supply them with it’.

9. GCI Index and capacity building
“IT is ever-changing, and there is the need to evolve in order to stay relevant.” - Ryan Ogilvie
9.1. Global Cybersecurity Index
- There is a limited amount of published data available on program investments
- Approximately 200-300 CCB projects are launched annually
- In 2018, the total investment was somewhere between €85m and €250m
- The number of actors involved in CCB projects is growing rapidly
- Not only the number of actors but the complexity of the projects is also growing
The GCI index, i.e. the Global Cybersecurity Index, is a reference calculation created by the ITU (International Telecommunication Union), for which the necessary data is provided voluntarily by the participating countries. This index makes it possible to compare the commitment of individual countries to cybersecurity on an international level and assess how effectively a given country can handle cyber threats and challenges in cyberspace.
The GCI is built on five pillars: legal measures, technical and procedural measures, organizational structures, capacity building, international facilitating and enhancing cooperation.
However, the most critical goal of the GCI is not only the comparison and the creation of a corresponding ranking but also the promotion of international cooperation and knowledge exchange in cybersecurity. The program’s primary goal is the effective development of the security of the information society based on international cooperation that minimizes overlaps between different areas and activities.
9.2. ITU and capacity building
ITU collects data, analyzes it, and then prepares reports, among other things, in the field of cyber capacity building. As per the GCI Fourth Edition Report,
“Countries that tend to do less well in the Global Cybersecurity Index are more likely to be least developed countries and to have a high percentage of their populations unconnected.”
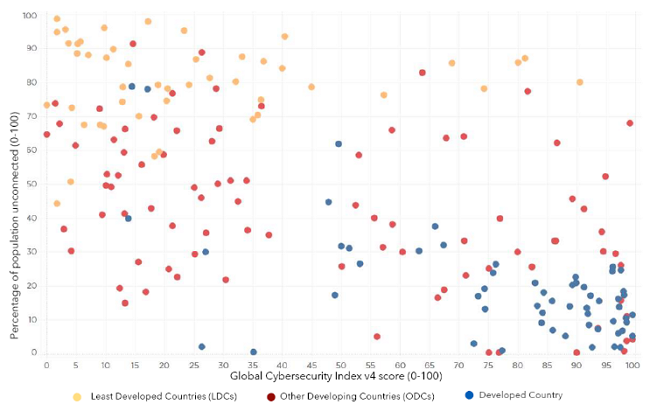
The correlation between GCI and the unconnected population of countries to the Internet - ITU
However, mainly in these countries, the number of new users connected to the Internet, whose level of cyber hygiene falls short of the required level, is proliferating. Besides, many least developed countries face challenges in bridging their cybersecurity gap to physically and virtually protect their ICT systems.
Governments have a vital role in motivating the private sector to adopt cybersecurity as widely as possible. Such an incentive mechanism could be, for example, the creation and application of tax incentives based on cybersecurity parameters. Raising the adoption of cybersecurity at the national level should be achieved by promoting a cybersecurity culture by changing the mindset of business leaders. Indeed, business leaders tend to view cybersecurity as an abstract information technology problem rather than one of the essential tools to improve overall business efficiency.
If we look at the territorial breakdown of where and in how many countries cybersecurity capacity building in the private sector is encouraged with incentive mechanisms, then according to the ITU’s measurements, we get the following figure:
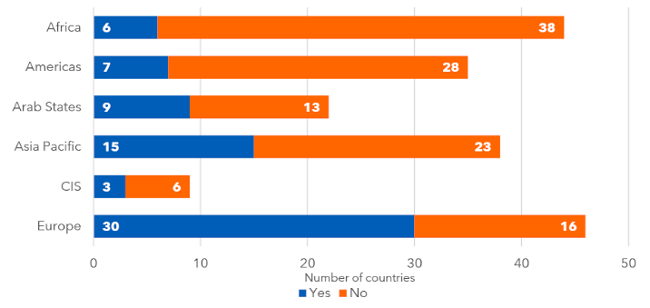
Number of countries with CCB incentive mechanisms - ITU
10. ENISA
“Together, ordinary people can achieve extraordinary results.” - Becka Schoettle
One of the most significant cybersecurity organizations of the European Union is ENISA, which since its foundation in 2004, has been involved in the creation of the national CSIRTs (Computer Security Incident Response Teams) and effectively contributed to the development of their capabilities. ENISA is responsible for achieving a high level of cybersecurity across Europe.
CCB projects
- must be based on long-term agreements and understanding
- require clear communication and common language
- need international coordination and cooperation
- present different challenges and priorities for donors and beneficiaries
- require constant development and willingness from all parties
ENISA plays a vital role in developing the national cybersecurity strategies of the member states because, as a consultative organization, it contributes to them with international good practices and advice.
Through knowledge sharing, capacity building, and awareness-raising, the Agency collaborates with the most significant stakeholders to strengthen trust, increase the flexibility of the EU infrastructure, and ultimately preserve the digital security of European societies and its citizens.
For a country to adequately respond to cyber threats despite the ever-changing nature of cyberspace, it needs flexible and dynamic cybersecurity strategies. Naturally, due to the nature of cyberspace, international cooperation is essential to achieve this goal.
One of the primary conditions for countries to participate in international cooperation is to have cybersecurity guidelines (laid down in comprehensive strategies) and an effective organizational system capable of implementing them.
As part of the development of the national cybersecurity strategy, the role of existing national cybersecurity and incident response teams (CERTs – Computer Emergency Response Team) in both the public and private sectors should be analyzed and defined. In addition to surveillance activities, a national or governmental CERT may be tasked with information sharing and the protection of critical information infrastructures. CERTs can play a crucial role in cooperation and information exchange with other similar organizations at both national and international levels.

ENISA – the EU Cybersecurity Agency
It is imperative how quickly the actors responsible for implementing the cybersecurity strategy can share, for example, information warning of cybersecurity threats. Based on these warnings, citizens or the private sector can take effective cyber protection measures or start preparing for cyber defence. On the one hand, this requires an organizational system that continuously monitors cybersecurity threats. On the other hand, it should have a communication network to analyse and share information to reach all those affected. CERTs are the most suitable units for securing, building and operating this organizational system.
Information and communication technology systems and the services provided through them fundamentally contribute to the security of the European Union. Networked information and communication technology systems have become the primary target of malicious actors who want to cause harm to these systems.
Attacks on the vulnerable points of network devices have now been supplemented by attacks on critical (information) infrastructures, and there are also many attempts to steal data. The complexity of cyber-attacks has also increased, and even hybrid warfare – the use of a mixture of computer and conventional war operations – has come to the fore to achieve geopolitical goals.
The Covid-19 epidemic has highlighted the need for greater security in the digital world. People have increased their online presence to maintain personal and professional relationships. In contrast, cybercriminals have taken advantage of this situation, mainly targeting e-commerce, e-payment businesses, and the healthcare system.
11. National CSIRTs and CERTs
“There’s no silver bullet solution with cybersecurity; a layered defense is the only viable defense.” - James Scott
11.1. The need for national CSIRTs
The need for the ability to respond to and manage cybersecurity incidents has long been unquestioned. Governments must have CSIRTs (Cyber Security Incident Response Teams) that can effectively manage and mitigate cybersecurity incidents, perform incident analysis, and provide information assurance and situational awareness services.
To perform their functions well, these teams should keep in touch with each other and form a network like weather forecasting stations, which predict ‘bad weather’ and inform each other about possible ’thunderstorms’.
The most important tasks of national CSIRTs include:
- Provide incident detection and management services to the government;
- Protect critical information infrastructure;
- Be the designated government point of contact for cybersecurity issues;
- Become a member of international CSIRT communities to share knowledge and improve overall cybersecurity resilience
11.2. The difference between CSIRT and CERT
Sometimes the abbreviations CERT and CSIRT are used synonymously. Jamison Cush made this short insightful video about the difference between the two:
CERT vs CSIRT vs SOC: What’s the Difference? - YouTube
CIRCL is the CERT (Computer Emergency Response Team) for the private sector, communes and non-governmental entities in Luxembourg.
12. Cyber capacity building in developing countries
“We need a cybersecurity renaissance in this Country that promotes cyber hygiene and a security-centric corporate culture applied and continuously reinforced by peer pressure.” - James Scott
12.1. Why is this a particularly pressing problem for developing countries?
Cyberspace is growing at an unprecedented speed, and it is an integral part of the development of every country. The rapid growth and global access to IT technologies coupled with economic growth have resulted in many early adopters in developing countries: Asia and Africa are experiencing the fastest growth in the number of Internet users.

Photo by Emmanuel Ikwuegbu on Pexels
Since cyberspace knows no geographical boundaries, developing countries may face the same cyber threats as the developed world. However, developing countries often lack adequate IT infrastructure, security and legal frameworks, and they have less ability to deal with these challenges than developed countries. The above factors make developing countries vulnerable to cybercrime and increase their chances of being attacked.
The low cybersecurity awareness among people in developing countries leads to general poor security habits that allow cybercriminals to thrive. Efforts should be made to increase cybersecurity awareness locally, especially in impoverished areas, regarding various cyber attacks.
The insufficient infrastructure to deal with cyber attacks and the increased use of technology are both pressing issues. These two together are thus the worst possible combination since increased access and use are not combined with an adequate level of protection and security.
This is why building cyber capacity in developing countries has become crucial. This is the only way donor countries can ensure the minimum level of cybersecurity worldwide.
It is also essential for developed countries to achieve a minimum level of cybersecurity. Like during the COVID pandemic, developed countries helped less developed and more vulnerable countries with vaccine shipments. In the case of cyber capacity expansion, the transfer of knowledge and increasing the security of networks are in everyone’s common interest.
12.2. ACRC – Africa Cybersecurity Resource Centre
ACRC aims to build one of Africa’s largest groups of experts to provide cybersecurity services and information sharing in Africa to protect the financial sector and its clients. Gradually, three sub-regional offices will be established in Senegal for French-speaking countries and East and West Africa for English-speaking countries.
The ACRC is led by a non-profit consortium of public and private partners in Luxembourg and Africa, bringing together more than 365 high-level experts. These experts come from
- SECURITYMADEIN.LU
- Cybersecurity Research Centre of the University of Luxembourg (SnT)
- Excellium Services
- Suricate Solutions
In the Lëtz Talk about Cyber series, Dr Pascal Steichen interviewed Dr Tegawendé F. Bissyandé, an ERC fellow, Associate Professor of Computer Science at the University of Luxembourg. If you want to read more than just abstract conclusions about the principles and challenges of cyber capacity building, I recommend this informative discussion. On the one hand, you get a picture of an exciting life path, but not least, you may also gain insight into the challenges African countries face and how they participate in CCB projects.
Prof Tegawendé also talked about the LuxWays project, a capacity building project initiated by the University of Luxembourg’s Interdisciplinary Centre for Security, Reliability and Trust (SnT) and supported by the Luxembourg Ministry of Foreign and European Affairs. Within the framework of this initiative, Master’s students from the Universities of Burkina Faso and Senegal can join SnT in Luxembourg and earn their PhD degrees in computer science.
“This project will create so many opportunities for young researchers who will now be able to study computer science at home, instead of only a select few leaving the country, as I did in order to follow my chosen research path.” - Prof. Tegawendé Bissyandé
The full video can be watched on our PeerTube channel.
Lëtz Talk about Cyber with Prof Dr Tegawendé F. Bissyandé
ACRC provides innovative services covering all aspects of strengthening the cybersecurity ecosystem, including capacity building in the African region. ACRC took a very active role, participated in the openECSC Challenge, and attended the Paris Peace Forum 2021 and the African Finance Cybersecurity Conference.
SECURITYMADEIN.LU supports relationship building, knowledge transfer and, among other activities, capacity building in the cyber security sphere with all possible means. An example of this is the 43rd Cybersecurity Breakfast, the topic of which was How Luxembourg and Africa cooperate for building capacities?
Of course, projects related to capacity expansion do not only exist about cyber security. BLF (Business Partnership Facility) is an excellent example of this. BLF encourages the Luxembourg (or European) private sector to establish partnerships with organizations in developing countries to create sustainable business projects.

Photo by Sammyayot254 on Unsplash
12.3. Asia Pacific’s cyber capacity building
There are significant differences between countries in the pace of cyber capacity building in the Asia Pacific region. ASEAN (Association of Southeast Asian Nations) is an essential link between these countries. Its cybersecurity cooperation strategy for 2021-25 can be found here.
Singapore has been putting much effort into enhancing its national cybersecurity capabilities: in 2019, it launched a five-year-long project called the ASEAN-Singapore Cyber Security Center of Excellence. This was a huge step forward, as it opened up the possibility of offering policy and technical programs to the participants of the member states to strengthen the regional cybersecurity capabilities.
Japan gradually increased its participation in CCB projects. At the 2009 ASEAN-Japan Cyber Security Policy Meeting, Tokyo gradually expanded its CCB relations with Southeast Asian states to include cooperation in mutual incident notification and joint governmental and academic cooperation. The ASEAN-Japan Cybersecurity Capacity Building Centre (AJCC BC) was set up in Thailand to enhance cybersecurity awareness and promote information sharing.
India has also made significant progress in training thousands of government officials in cybersecurity and establishing non-ASEAN partnerships with Japan, Israel and Bahrain. Under the Indian Ministry of Electronics and Information Technology, the National e-Governance Division (NeGD) established cyber labs for an Online Capacity Building Programme. Another CCB initiative is led by the Manohar Parrikar Institute for Defence Studies and Analyses (MP-IDSA).

Photo by RODNAE Productions on Pexels
13. Global Cyber Security Capacity Centre (GCSCC)
“More and more, modern warfare will be about people sitting in bunkers in front of computer screens, whether remotely piloted aircraft or cyber weapons.” - Philip Hammond
Global Cyber Security Capacity Centre (GCSCC) is an international research centre that helps increase the effectiveness of cybersecurity capacity building initiatives worldwide. The Centre has created a unique model that examines the maturity of cybersecurity capacity in five areas. It allows nations to self-assess and compare their achievements with those of other countries to better plan their investments and national cybersecurity strategies and set priorities.
The GCSCC has established regional collaborative partnerships with centres elsewhere in the world. The first collaboration was established with the Oceania Cyber Security Center (OCSC) in Melbourne, but the Centre is planning similar collaborations in Africa and Asia.

The Global Cyber Security Capacity Centre (GCSCC) at the University of Oxford
14. The European Cybersecurity Competence Centre and its Network of National Coordination Centres
“The single biggest existential threat that’s out there, I think, is cyber.” - Michael Mullen
14.1. The European Cybersecurity Competence Centre
The European Cyber Security Competence Centre (ECCC) based in Bucharest aims to increase Europe’s cybersecurity capacity and competitiveness. It coordinates and cooperates with a Network of National Coordination Centres (NCCs) in all of the 27 EU Member States by awarding grants and conducting procurements.
The ECCC is jointly financed by the financial contributions of the European Union and Member States. The ECCC administrative and governance structure includes a Governing Board, an Executive Director and a Strategic Advisory Group.
The two main frameworks in which the ECCC operates are the Digital Europe Programme (DEP) and Horizon Europe.

Introducing the Digital Europe Programme
While the Digital Europe Programme is intended to support cybersecurity in order to protect the digital economy and society of the EU, research and innovation in cybersecurity are supported by Horizon Europe.
In the new Digital Europe Programme framework, the European Commission has put forward an investment of 2 billion euros in 2018 to protect the EU’s digital economy, society and democracies by financing state-of-the-art cybersecurity equipment and infrastructure.
On 16 February 2022, Pascal Steichen, CEO of SECURITYMADEIN.LU, was elected Chairman of the European Cybersecurity Competence Centre (ECCC). On his election, Pascal Steichen stated:
"I welcome this appointment with great enthusiasm and pride. A major task awaits us, to build and continually strengthen this European cyber community. Joining forces to strengthen research, innovation, and the response to emerging threats is a key factor in increasing Europe’s cybersecurity capabilities and competitiveness”.
The Governing Board of the European Cybersecurity Competence Center recently held its first physical meeting in Bucharest. The Governing Board consists of the representatives of the Member States of the European Union (EU) (27 members), the European Commission (two members) and the European Union Cyber Security Agency ENISA as a permanent observer.
14.2. The European Cybersecurity Competence Network of National Coordination Centres
The Network of the European Cybersecurity Competence Centre consists of 27 National Coordination Centres (NCCs) designated individually by the different Member States. The National Coordination Centres represent the different national cybersecurity ecosystems and also implement the overall strategic direction.
They also function as contact points at the national level for the Competence Community and the European Cybersecurity Competence Centre. The key function of the NCCs is national capacity building, which is carried out in the framework of the NIS through effective cooperation with industry, academia and research communities, as well as with the public sector and the authorities.
This initiative aims to significantly contribute to the creation of a connected and widely autonomous EU-wide cybersecurity industrial and research ecosystem. The European Union recognized that the overall cybersecurity level of its Member States could only be increased by using resources in a unified network that should as well enable better coordination between the different local ecosystems. The network also provides an opportunity for the Member States to better resist cyber threats and better tackle cybersecurity challenges.

The European Cybersecurity Competence Centre
The European Cybersecurity Competence Network also supports its Member States in identifying and developing long-term strategic perspectives in their individual cybersecurity policies. One of the main strengths of the network is that it enables the research and industrial communities, so as public authorities to access and combine critical resources such as testing and experimental facilities.
Further, NCC’s will monitor and promote technological capacities, disseminate information, tools, materials and resources and promote participation in cross-border projects and in cybersecurity actions funded by relevant Union programmes. They will also organize cybersecurity events and attend/ promote stakeholder events.
14.3. The European Cybersecurity Competence Centre and its Community
The ECCC Regulation foresees that in the EU there is one cybersecurity Community, where entities from all 27 Member States can become members. Nevertheless, it is clear that there is a need for cooperation also at the national level. The NCCs should play a role as the Community gatekeepers, at the initial stage through the application assessment procedure and later on actively organizing and supporting the cooperation of national members of the Community.
Based on the Article 8.2 of the Regulation (EU) 2021/887 (the Regulation), the Community shall consist of industry, including SMEs, academic and research organisations, other relevant civil society associations as well as, as appropriate relevant European Standardisation Organisations, public entities and other entities dealing with cybersecurity operational and technical matters and, where relevant, stakeholders in sectors that have an interest in cybersecurity and that face cybersecurity challenges. The Community shall bring together the main stakeholders with regard to cybersecurity technological, industrial, academic, and research capacities in the European Union.
The Community contributes to the mission of the ECCC and the Network, enhances, shares and disseminates cybersecurity expertise across the EU.
14.4. The National Cybersecurity Coordination Centre Luxembourg (NCC-LU)
Within the Network of National Coordination Centers established by EU Regulation 2021/887, SECURITYMADEIN.LU has been designated as the National Coordination Center (NCC) of Luxembourg in December 2021. The Luxembourg National Cybersecurity Coordination Center (NCC-LU) serves as the single point of contact for the ECCC, the European Network of National Coordination Centers (NCCs) and national stakeholders in Luxembourg.
The focus of activities is on open, agile and adaptive cooperation between different stakeholders, so as to promote synergies and mutual understanding. Key attributes of the NCC-LU include connecting different capabilities and stakeholders in order to prevent fragmentation. Networking shall help to build a safe, resilient and trustworthy ecosystem.

The logo of the Luxembourg Cybersecurity Coordination Centre
NCC-LU aims to promote the European and the Luxembourg Cybersecurity Ecosystem. It also ensures coordination between other NCC’s within the Network. NCC-LU’s key role is to connect stakeholders to build a secure, resilient, and reliable ecosystem. The beneficiaries of the NCC-LU are as follows:
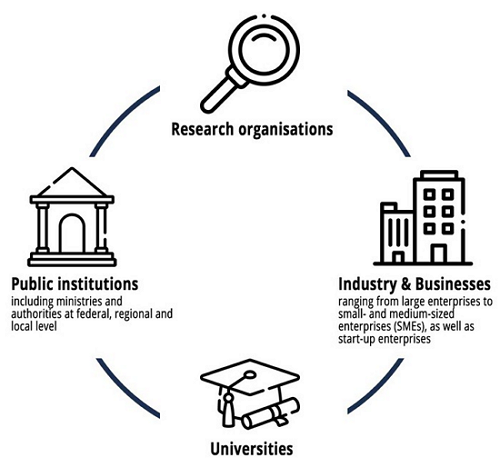
Target groups of the NCC-LU
15. Conclusions
“Let’s face it: the future is now. We are already living in a cyber society, so we need to stop ignoring it or pretending that it is not affecting us.” - Marco Ciapelli
Cybersecurity must be strengthened in all areas of society, be it social, economic, governmental, judicial or educational.
Developing countries face challenges in all areas of CCB: human resource development, institutional reforms, organizational adaptation, IT infrastructure and network development, legal harmonization, etc. In addition, developing countries have limited access to the Internet and cyberspace and the benefits of their use.
There are challenges concerning both the donor and developing countries, which must be resolved in order to implement a successful CCB project. For instance, no country faces the same challenge. This factor must be considered to implement a successful CCB project, not only in the case of developing countries but also in the case of donor countries.
Transparent and honest communication among CCB partners makes possible a firmer, more targeted and successful approach to CCB as both the receiving and donor countries know what stage the developing country is in and thus what needs to be improved.
- Global Cyber Security Capacity Centre (GCSCC)
- European Cyber Security Competence Centre (ECCC)
- National Cybersecurity Coordination Centre Luxembourg (NCC-LU)
- Digital Europe Programme
- Horizon Europe
- SPARTA
- Cybil: The Knowledge Portal for Cyber Capacity Building
- ACRC
- LuxWays
- ASEAN (Association of Southeast Asian Nations)
Successful CCB projects can only be implemented if the legal framework includes laws against cybersecurity and cybercrime. However, developing countries must make their legal framework feasible and broad enough to ensure sufficient legislative scope.
Awareness-raising, education, and training are essential factors in a successful CCB project. These factors also play a vital role in reaching good cyber hygiene and sustainable cyber capacity.
No CCB project can be successful without a suitable partner. However, finding partners is not easy but a very time-consuming process, in which only clear communication and building on trust can lead to success.
Given the current speed of technological progress, finding the right partner is also complicated because capacity building is a dynamic process where the needs of interested parties can constantly change and evolve.
Although donor countries contribute to creating a safe and stable cyber space by promoting the development of cyber capacities, it is important to understand that cyber capacity building is more than that. Implementing a successful CCB project can help ensure more comprehensive stability and achieve socio-economic growth.
Ultimately, therefore, the support of developing countries has a positive effect on the donor countries as well: the spread of economic balance, the possibility of global socio-economic growth, and a more predictable and calm atmosphere in physical and cyberspace all work in the direction of global growth.

Photo by Thirdman on Pexels