- 01 Oct, 2021
- Topic of the Month

1. Introduction
“We still need encryption, and with the challenges we face on cybersecurity, encryption remains even more essential to protecting safety and commerce online.” - Alan Davidson
1.1. The origins
The origins of cryptography go back to the Egyptians. About 4000 years ago, they used hieroglyphs to communicate. The first ciphers were built to swap or replace letters in the original text. The Greeks used the comb method, where the messages were written in two lines, and the letters of the bottom and top lines were alternated. The two lines were eventually spelt together so that the letters were mixed up.
The letter substitution method was named after Caesar, who replaced the letters of the alphabet with other letters. The idea of letter substitution continued to live until the 19th century.
One of the secrets to the success of World War II decoders was the advent of the first (partly) electronic computers (Colossus) to crack Enigma codes in hours instead of weeks, making plenty of convoy journeys safer. In the first decades of the 20th century, methods primarily based on the science of mathematics were perfected.

Source: Origin of Cryptography
The purpose of cryptography in earlier ages was to convey a particular message to another person so that only that person could understand it. The message often contained military secrets. Nowadays, this area of use has diminished, and the goal of encryption has become data security. In our daily lives, we often encounter tasks related to the electronic storage, transmission, and processing of information, some of which is not public. Several codes in computing and communications are not used for encryption but for the secure storage or transmission of data.
The use of cryptography ensures the confidentiality, protection, or authenticity of messages or stored information.
1.2. Nowadays
With the development and highly dynamic growth of services available on the World Wide Web, the number of security risks and the extent of their impact are also increasing. Nowadays, it is natural for many of us to provide personal information, even on public websites, which we previously shared only with our close acquaintances. With millions of users and the worldwide popularity of some services, the extent of damage to a software bug, virus, or malware can increase by orders of magnitude.
Today, we live in an era where information can be precious. Such valuable information should be protected at all costs, and there are many solutions in I.T. to protect our stored data and communications. We can use firewalls, physical separation, encryption, data hiding, and many more. Of these solutions, this article discusses encryption.
The primary purpose of encryption is to transmit confidential data from the sender to the recipient through an insecure channel. Another purpose of encryption is to allow only certain people to access stored data.

Photo by Markus Spiske on Unsplash
While this may seem very simple and easy to do at first, delivering a message from one party to another is quite a challenge (to be sure that only the target person received and read our message or digital attachment) in today’s world.
The Internet is a global, giant, shared and mostly free cyberspace where billions of people communicate. Our belief in the Internet is based on the assumption that we want to believe that when we send a message to someone, the content of the message can only be read by the target person, and for unauthorised persons, our message is not readable.
Without encryption, the Internet would be like a city without fences, gates, street signs, front doors, and personal addresses: anyone would be free to go anywhere, sneak in anyone’s home or garden, and personal privacy would not exist.
2. What is encryption?
“Now, more than ever, strong security and end-user controls are critical to protect personal information …” - Terrell McSweeny, Commissioner, Federal Trade Commission
2.1. Encoding information
Encryption is the process of encoding information. The encryption process converts the original representation of the information (called’ plain text’) into an alternative form of encrypted text (called’ ciphertext’). That is, ‘ciphertext’ or’ cyphertext’ is the result of encryption performed on plaintext using an algorithm called a cipher. The formulas used to encrypt and decrypt messages are called encryption algorithms or ciphers.

Photo by Mauro Sbicego on Unsplash
In a simplified way, encryption is the process of converting human-readable plaintext into unintelligible text, also known as ciphertext.
2.1. When do we use encryption?
Encryption is used to protect data stored in computer systems and transmitted over computer networks. Financial transactions, online shopping, or even private messaging often use encryption to increase security.
When using messaging applications, we expect the messages to be private. Messaging applications use encryption to maintain the confidentiality and security of users’ communications.
Browsers and websites use the encrypted HTTPS protocol that ensures secure communication by preventing our data from being read by unauthorised third parties during transmission.
Encryption is essential when we need to determine if data has been manipulated (data integrity), to increase people’s confidence in communicating with those they think they are communicating with (authentication), and to make sure that messages are sent and received (non-repudiation).
2.2. End-to-end encryption
Encryption is more important than ever, as cybercrime is one of the fastest-growing security threats. The question arises as to how data can be encrypted when two people are communicating over the Internet, and only the sender and the recipient of the message know the content of the message. The solution is called end-to-end encryption (E2EE), a form of encryption in which only the sender and recipient can read the message: no third party, not even the party providing the communication service (Internet Service Provider, or ISP), knows the encryption key.
In E2EE, data is encrypted on the sender’s system or device and can only be decrypted by the recipient. The cryptographic keys encode and decode messages and are stored in the endpoints since E2EE uses public key (asymmetric) encryption. Because of this, end-to-end encryption is the most secure form of encryption you can use.
End-to-end encryption is necessary when data security is of utmost importance in the financial, healthcare or communications sectors, public administration, and the military. End-to-end encryption can also help companies comply with privacy and security regulations and laws.
3. What is Cryptography?
„Cryptography is the science of secrets. In the distant past, it was simply about scrambling messages so adversaries couldn’t read them. In the modern computing era, cryptography has become a keystone of computer security, encompassing all the ways we hide data, verify identities, communicate privately, and prevent message tampering.” - Matthew MacDonald
In our daily communication, we use different signal systems to transmit information. A signal system is a set of signals whose use and structure are bound by rules. We are talking about cryptography if a signal system is known and used by only a few in their communication and is not understood by outsiders.
A public message transmitted during a communication process is encrypted if the sender sends it in a form that can be read or received by more than one person but understood only by a targeted group of recipients.
The cryptographic process consists of several steps. It starts with the encryption of the original text, then continues with the transformation of the text into characters (this part is called coding). In the process of encryption, the information is translated using a cryptographic method. To encrypt, we need to choose among cryptographic methods or invent a new one. Coding always requires a code table in which we record the essence and rules of a given method. The video below briefly summarises the essence and significance of cryptography:
Source: What is Cryptography?
Cryptography should always be transparent. The rules must be designed so that the original message can only be translated into the secret language in the same way. Restoring the encoded text is called decoding. To decrypt, we need to know the code table that contains the rules of the method.
The essence of cryptography is that the information hidden in encrypted messages or translated into a secret language only reaches the target person who knows the method of decryption. It is crucial that the original message can only be translated into the secret language in one way and restored in the same way.
Cryptography is the science of encrypting and decrypting information. It is about creating and analysing protocols that prevent third parties or the public from reading private messages. Companies are increasingly relying on different encryption methods to protect their sensitive data from reputational damage in a data breach.
4. The primary aims of cryptography
“Without strong encryption, you will be spied on systematically by lots of people.” - Whitfield Diffie
We often encounter tasks related to the electronic storage, transmission, and processing of information in our daily lives. The information stored or transmitted is often sensitive in the sense that its unauthorised disclosure or fraudulent modification gives rise to material and moral damage. Therefore, security has become an essential criterion for the applicability of information and communication technologies.
The basic goals of cryptography are as follows:
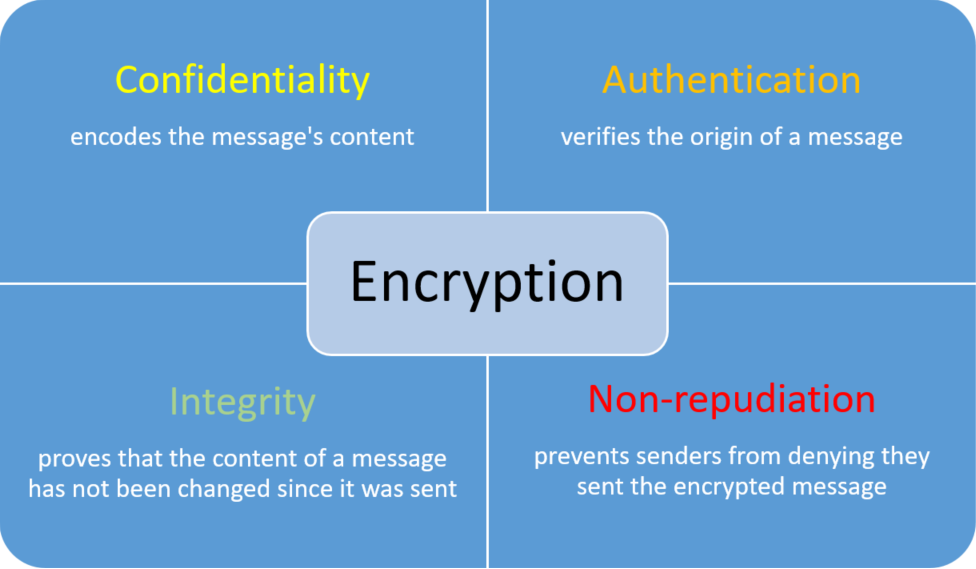
- Privacy/Confidentiality: Basically, the primary function of encryption is to ensure that no one can read the message except the intended recipient. It is achieved by ensuring that the eavesdropping attacker does not understand the content of the messages.
- Integrity protection: Its purpose is to ensure that the recipient of a message can reliably determine from the received message whether its content has changed during transmission.
- Authentication: It is the process of proving one’s identity. The purpose is to detect message fabrication and impersonation. During the authentication process, the authentication participant verifies the sender’s identity in a dialogue.
- Denial protection: It ensures that the sender of a message cannot deny the fact of sending the message, or in other words, the recipient of the message can prove who the sender of the message is. It is called non-repudiation.
- Key exchange: It is the method of sharing encryption keys between the sender and the recipient.
The above objectives can be achieved by using different cryptographic mechanisms (algorithms and protocols).
5. The importance of encryption
“The new rules should also clearly allow users to use end-to-end encryption (without ‘backdoors’) to protect their electronic communications… Decryption, reverse engineering or monitoring of communications protected by encryption should be prohibited. In addition, the use of end-to-end encryption should also be encouraged and when necessary, mandated, in accordance with the principle of data protection by design…” - Giovanni Buttarelli, European Data Protection Supervisor
The worst data breaches of 2021 (Jan-June)
- January – Serasa – 220 million
- January – MeetMindful – 2.28 million
- January – Sociallarks – 200 million
- January – Pixlr - 1.9 million
- February – AFTS – 38 million
- March – Microsoft – 30000 organisations
- April – Facebook – 533 million
- June – LinkedIn – 700 million
It is evident to everyone that encryption is critical in IT, but why is that so? To answer this question, we need to go back a bit to the definition of encryption.
Encryption is the process of decoding data to make it incomprehensible to those who do not have permission to access the data. That is, if encryption is effective, you protect your data from unauthorised access.
And that’s why encryption is so vital to everyone: even if we don’t care or don’t know with which method and how encryption is done, it’s apparent that we don’t want our documents, images to be seen or read by others, or accessed in any way (unless we intend to share them explicitly).
Just as in the physical world, we lock our apartment before we leave home, chain our bikes if we leave it outside in front of the store, or put a padlock on the garden shed, we rely on encryption in cyberspace to protect our data from unauthorised people.

Photo by Markus Winkler on Unsplash
We can no longer stick our heads in the sand and cannot neglect the existence of cyberspace because it is so intertwined with the physical world around us. Digital security is becoming crucially important to protect us as we live our everyday life: as we shop or bank online or simply keep in touch with our friends or relatives on one of the social media sites.
And behind our cybersecurity, encryption lurks unnoticed in cyberspace in the background. And just like health in physical life, encryption is often only noticed if it doesn’t work correctly, if it stops working or when it is too late.
6. Types of cryptographic algorithms
„By 2025, 80 percent of the functions doctors do will be done much better and much more cheaply by machines and machine-learned algorithms.” - Vinod Khosla
There are several ways to classify cryptographic algorithms. Three types can be distinguished based on the number of keys used for encryption and decryption and their usage.
- Symmetric encryption or Secret Key Cryptography (SKC)
- Asymmetric encryption or Public Key Cryptography (PKC)
- Hash functions

Photo by Everyday basics on Unsplash
7. Symmetric Encryption
“Somebody will be able to overcome any encryption technique you use!” - Noam Chomsky
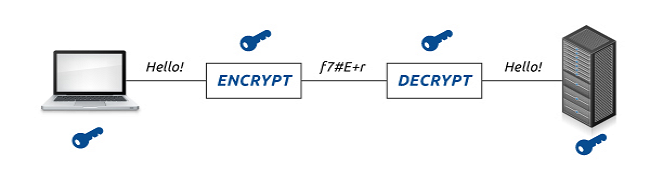
Symmetric encryption uses a single key to both encrypt and decrypt data. It means that both the sender and the receiver need the same key to communicate. This type of encryption is also called pre-shared key encryption.
The sender uses a key to encrypt the plaintext and sends the ciphertext to the receiver. The receiver applies the same key to decrypt the message and recover the plaintext. Because a single key is used for both functions, secret key cryptography is also called symmetric encryption.

SKC is primarily used for privacy and confidentiality. Symmetric key sizes are usually 128 or 256 bits - the larger the key size, the harder it is to crack the key. To illustrate the strength of a 128-bit key, consider the following example:
A 128-bit key has 340,282,366,920,938,463,463,374,607,431,768,211,456 encryption code possibilities. It is easy to see that a brute force attack (when an attacker tries every possible key until he finds the right one) takes quite a bit of time to crack it.
After that, let’s see in a schematic diagram what the process is of symmetric encryption. As can be seen in the diagram, the encryption and decryption are performed with the same key. The key can be a password or a key file, or a combination of these.
Source: Digicert - Behind the Scenes of SSL Cryptography
Suppose a message sender A wants to forward his message to B on a communication channel that can be assumed to be insecure in the sense that an attacker “listening” on the channel can monitor the bits passing through the channel. The sender of the message wants to prevent the attacker from unauthorizedly decrypting the message, that is, the sender wants to encrypt the message.
Without a very complicated technical hocus pocus, the video below shows the dangers of symmetric cryptography in an infinitely simplified way:
Source: How does symmetric encryption work?
Scott (on the left) tries to send a message to Wilson Yan (on the right). To do so, Yan should send a secret code to Scott….but Shelley (representing the hacker on the network) is between them.
The advantage of symmetric encryption is that it is much faster than asymmetric encryption. Obviously, the key must be known to both the sender and the recipient. The nature of this is the secret itself, and the greatest weakness of this method lies in how the sender and receiver can secretly share the content of the key with each other.
If any third party becomes aware of the content of the key, the communication is no longer secret. The downside of this method is that both the sender and recipient need to know the key. Sending the key from the sender to the recipient is only recommended through a secure channel; otherwise, anyone can read the message by obtaining the key.
Secret key cryptography can be categorised as either stream ciphers or block ciphers.
Secret key cryptography algorithms include:
- Data Encryption Standard (DES): One of the best known and best studied SKC schemes designed by IBM in the 1970s.
- Advanced Encryption Standard (AES): became the official successor to DES in December 2001.
- Rivest Ciphers (RC1, RC2, RC3, RC4, RC5, RC6): also known as Ron’s Code from Ron Rivest.
- International Data Encryption Algorithm (IDEA):
- Blowfish: it is unpatented and license-free and created as a substitute for IDEA.
There are many more (Twofish, Threefish, Anubis, ARIA, Camellia, etc.) ciphers to use. For further reading, please navigate to the site An Overview of Cryptography by Gary C. Kessler.
8. Asymmetric encryption
“Without strong encryption, you will be spied on systematically by lots of people.” - Whitfield Diffie
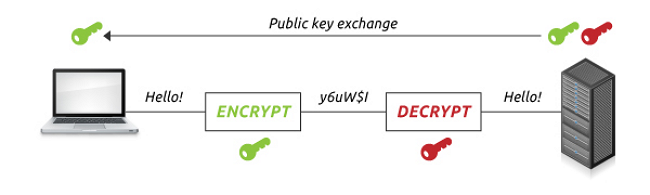
Asymmetric encryption (or public-key cryptography) uses a separate key for encryption and decryption.

In asymmetric encryption, we use two keys: a public key is used for encryption, whereas a secret key is used for decryption. Anyone can use the encryption key (public key) to encrypt messages; however, the decryption keys (private keys) are secret. This is the most significant difference compared to symmetric encryption: since the private key is ‘private’, only the intended receiver can decrypt the message.
When using asymmetric encryption, the encoding and decoding process is slower than when using symmetric methods. For this reason, this method is reluctant to be used to encrypt large amounts of data.
Asymmetric keys usually are 1024 or 2048 bits. However, keys smaller than 2048 bits can no longer be considered secure. Larger keys than 2048 bits can also be created, but they are very rarely used (it would take an average computer more than 14 billion years to crack a 2048-bit certificate).
Source: Digicert - Behind the Scenes of SSL Cryptography
In practice, its operation looks like the participants in the communication have their own public and secret keys. The public key can be used to encrypt the data, which can then only be decrypted using the associated secret key, which is held exclusively by the recipient. Be aware that the public key cannot be used to generate the secret key, and the public key cannot be used to decrypt the message.
The process between the sender and the recipient is therefore as follows:
- the recipient shares his public key
- the sender encrypts the message based on the public key received
- the sender sends the encrypted message to the recipient
- the recipient only decrypts the message using the secret key they have
Let Wilson Yan (on the right) explain the above step by step in the easy-to-understand video below. In this scenario, Yan sends the public key to Scott (on the left) first, who can encrypt the message by using the public key. Shelley (representing the hacker on the network) cannot read the message as the private key has not been shared.
Source: How Does Public Key Encryption Work?
The difference between asymmetric and symmetric key encryption is that the encryption key and the decryption key are different. Also, calculating the decryption key from the encryption key is a “difficult” task.
The advantage of asymmetric key encryption is that the implementation of secret communication does not require the prior creation (exchange) of a shared secret key between the sender and the receiver. It is sufficient to encrypt the message with the receiver’s public encryption key.
Note, however, that the sender must verify that the public key to be used is indeed the recipient’s public key and not a third, presumably malicious party. Public key cryptography thus simplifies the key exchange problem by requiring an authentic channel between the receiver and the sender instead of a secret channel through which the receiver can deliver its public key to the sender.
Because asymmetric keys are larger than symmetric keys, asymmetrically encrypted data is more difficult to crack than symmetrically encrypted data. The computational load on the asymmetric keys is more significant, however. Symmetric keys are smaller than asymmetric, so they require less computational burden. The most significant disadvantage of the symmetric keys is that the sender should share it somehow with the recipient. If sharing is not possible securely, then we can start worrying about data security.
In the case of asymmetric encryption, you do not need to worry about it. As long as you keep your private key secret, no one can decrypt your messages. You can distribute your public key with anyone without having to worry about your data being hacked: anyone with the public key can encrypt your data, but only the person with the private key can decrypt it.
Public-Key Encryption Algorithms
The most important public key Encryption algorithms are RSA (which gets its name from its three creators: Rivest, Shamir, and Adleman) and ECC (Elliptic Curve Cryptography). Besides the above, algorithms like Diffie-Hellman, DSA (Digital Signature Algorithm), IBE (Identity-Based Encryption) and PKCS (Public Key Cryptography Standards) are also in use.
9. Hash Functions
“Basically, hashing is a way to ensure that any data you send reaches your recipient in the same condition that it left you, completely intact and unaltered.” – Casey Crane
9.1. What are hash functions
These algorithms became necessary in the late 1980s with the advent of electronic signatures. Hash functions are methods used in computer science to map data of any length to a given length. The finite data thus obtained is called a hash value. This mathematical function converts a numeric input value to another compressed numeric value. The input of the abstract function is of any length, but the output (hash value) is always of fixed length.
The hash value is usually much smaller than the input data, so hash functions are sometimes called compression functions. Hence one of the most significant benefits of using them from a computational point of view is that extraction functions are much faster than symmetric encryption.
9.2. Popular hash functions
Some popular hash functions are as follows:
- Message Digest (MD)
- Secure Hash Function (SHA)
- RACE Integrity Primitives Evaluation Message Digest (RIPEMD)
- Whirlpool
9.3. Applications of hash functions
One of the purposes of the hash function in cryptography is to take simple text input and generate an extract value of a specific size in a way that cannot be reversed. This sounds like a theoretical and technical definition of a hash function, but what is it suitable for, and why is it so common? There are two applications of a hash function based on its cryptographic properties.
Data integrity check
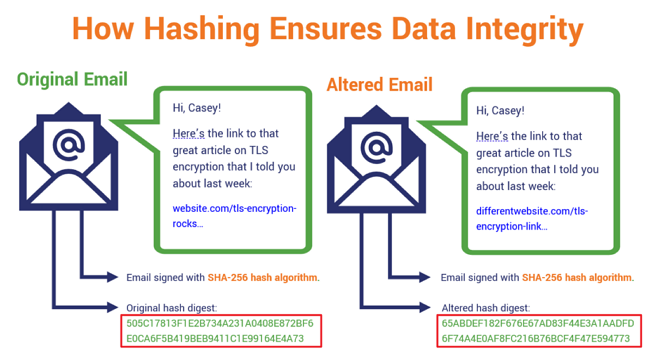
Hash functions ensure data integrity in public key encryption. The data integrity check is the most common application of the hash functions. They serve as a way to identify whether the data has been modified since it was signed. It also serves as a means of verifying identity.
The example below refers to a digitally signed email manipulated during transmission by a man-in-the-middle (MitM) attack. As shown in the red circled section at the bottom of the screenshot, the hash digest changed entirely because the content of the email was modified after it had been digitally signed. The modified hash digest proves that the content of the letter has been changed: it is not the same as the original, and so its content can no longer be trusted.
Source: What Is a Hash Function in Cryptography? A Beginner’s Guide
Password storage
By using the hash function, you may store passwords in a database securely. You may store your passwords on many websites, so you do not have to remember them every time you sign in. Instead of storing the passwords as plaintext, websites usually hash passwords and store hash values.
It is important to note that different hash functions serve different purposes depending on their hash speeds and design. You may want to use a fast hashing algorithm to establish a secure connection to websites, while for storing passwords, you need to choose a slow hashing algorithm. Hashing is also used for verifying data blocks in blockchain technologies.
10. PGP method
“Blockchain technology, or distributed ledger technology, is just a way of using the modern sciences of encryption to enable entities to share a common infrastructure for database retention.” - Blythe Masters
The use of the PGP method combines the speed of symmetric encryption with the security of asymmetric encryption. The point is that the data is encrypted with symmetric encryption, and the sender sends the corresponding key encrypted with asymmetric encryption. The key used for symmetric encryption is generated by a random number generator and is typically used only once. This key is also called a session key. Due to the small size of the session key, it can be encrypted relatively quickly.
The process between the sender and the recipient is as follows:
- produce the symmetric key
- this symmetric key is used to encrypt the data
- the symmetric key is encrypted using the recipient’s public key
- the encrypted data and encrypted symmetric key are sent to the recipient
- the recipient uses his own secret key to decrypt the symmetric key
- decrypts the data using the symmetric key

Photo by iMattSmart on Unsplash
11. Digital signature
“I’m a strong believer in strong encryption.” – Barack Obama
A digital signature is an encryption method used in electronic communications. The use of an electronic signature is made possible by public key encryption. The purpose of a digital signature is to allow the recipient to verify that the message was sent from the sender. To create a digital signature, the sender uses his private key, and the recipient verifies its authenticity with the sender’s public key. The digital signature contains a characteristic extract of the document, and it can only be forged if someone obtains the secret key. Internationally recognised organisations issue digital signatures.
The message authentication code allows the detection of changes (random and intentional) in the messages transmitted on the channel and the authentication of the sender of the messages. However, it provides these services only to the customer. The receiver can no longer convince an external third party that a received message is intact and originates from the sender, as the value of the message authentication code depends on a key that the receiver also knows.
Thus, the third party cannot determine with certainty whether the sender or the receiver generated the particular message authentication code. This means that the sender can deny that he has sent a message to the receiver, and the receiver cannot prove that the sender is lying. In other words, message authentication codes do not provide (origin) non-repudiation service.

Photo by Hope House Press – on Unsplash
Implementing the non-repudiation service requires an asymmetric mechanism that allows only the sender of the message to produce proof of the origin of the message (so it cannot be forged).
However, any participant in the system (including the receiver) can verify it. This mechanism is called a digital signature because its properties are very similar to those of a traditional signature. An essential difference between a digital and a traditional signature is that the digital signature is not tied to the material medium of the message (such as paper) but to the message itself.
The digital signature guarantees the origin of the message and allows you to detect changes in the content of the message after the signature has been generated. In summary, a digital signature is a mechanism that ensures the integrity and authenticity of messages and the undeniable origin of messages.
- TechTarget – Everything you need to know about cryptography
- DigiCert – Behind the Scenes of SSL Cryptography
- CASES - Cryptography
- ENISA - Post-Quantum Cryptography
- CIRCL - AIL Framework
- QuantumXchange – Quantum Cryptography, Explained
For practical reasons, the size of the digital signature should not depend on the size of the signed message. This can be achieved not by signing the message itself but by a so-called fixed-length message. To do this, we use a cryptographic function, also known as a hash function.
Electronic signatures (including timestamps) are widely used. They can be used to authenticate, for example, accounting documents after they have been issued electronically. Digital signatures can also authenticate paper-based documents after their digitisation. Thus, electronic invoicing can save significant paper, postage and typing costs on invoice transactions.
Their usage in judicial and administrative proceedings is also inevitable. The legal effect of an electronic signature cannot be denied because it exists exclusively in electronic form. Lawyers can countersign using an electronic signature. This can also happen when the client and the lawyer are far apart, making administration more manageable and faster. The lawyer prepares the electronic document, and the client signs it. Then the lawyer checks that the content of the document is unchanged.
12. Digital certificate
„In some ways, you can think of end-to-end encryption as honoring what the past looked like.” - Jan Koum
Digital certificates enable secure data exchange and electronic communication between people, systems and devices online. A digital certificate is used to authenticate a web service issued to an applicant by an authorised authority. By viewing, the user can verify that the service provider is indeed who they say they are. The certificate contains the details of the issuer and its public code key, which can be used to identify the signature.
Certificates help you verify the authenticity of people or places. A certificate is a statement that guarantees the identity of a person or the security of a website. With site authentication, a server certificate certifies that the site is secure and genuine. This certificate guarantees that no other site can misuse the I.D.s of the original site.
Digital certificates are also used by authorities in electronic form, in e-commerce and specific messaging applications. Its purpose is to avoid authentication and phishing.
12.1. The functions of digital certificates
Digital certificates are issued by certification authorities and have two main functions:
- They verify the identity of the sender/recipient of the electronic message
- Provide tools for encrypting/decrypting messages between sender and recipient
12.2. Types of digital certificates
There are three types of digital certificates
Individual digital certificates
This type of certificate is used to identify a person and include personal information. It can be used to sign electronic documents and emails and establish access control mechanisms for sensitive information. Personal authentication certifies that we are who we say we are. This type of information is needed when we send personal information over the Internet to a website that requires a certificate to prove our identity. Such personal certification can be issued by an independent certification authority (for example, Verisign).
Server certificates
These certificates identify a server and are used for SSL to ensure secure communication over the Internet.
Encryption certificates
Encryption certificates are used to code the message using the recipient’s public key to ensure data confidentiality during transmission.
13. Qualification of cryptographic mechanisms
“A cryptographic system should be secure even if everything about the system, except the key, is public knowledge.” - Auguste Kerckhoffs
13.1. How safe is our cryptographic algorithm?
The protection of a cryptographic algorithm against an attacker’s unlimited computing resource is called perfect or unconditional security (exists in theory). In contrast, security with limited resources is called algorithmic (practical) security or conditional security. Only one algorithm is known to be unconditionally secure: the one-time pad (OTP) encryption. However, we also know that the cost of absolute security is high: the length of the encryption key is at least as large as the size of the compressed open message. Therefore, the OTP encryptor in most applications is impractical, and we are forced to settle for conditional security algorithms.

Photo by FLY:D on Unsplash
But how can we be sure that our cryptographic algorithm is secure? In the traditional (unproven security) approach, by trying to find an attack. If we succeed, we can say that our algorithm is not secure. If it turns out that our algorithm is not secure, then - depending on the strength and nature of the attack - we either permanently reject the construct or try to confirm it according to the nature of the attack (i.e. patching).
There is also a more well-established method of qualification, and this is called proven safety theory. In this approach, we first define a security concept: we say what we mean by security (definition). The safety of our algorithm is then indirectly demonstrated.
13.2. Applications of cryptographic mechanisms
Many applications of the cryptographic mechanisms presented above can be found in everyday life, even if the average user is not aware of them most of the time. For example, cryptographic methods are used to authenticate the caller in the GSM system or to protect the data stored on the magnetic stripe of bank cards against unauthorised modifications.
The SSL protocol
The SSL protocol allows authenticated and secret communication between the browser and the web server. When the user clicks on a link beginning with https: // in the browser, the browser and the web server named in the link start running the SSL protocol. This is usually indicated by a small key or a locked padlock that appears at the bottom of the browser window.
At the beginning of the SSL protocol, the browser and server first perform a key exchange, using asymmetric key cryptographic methods (namely, RSA or the Diffie-Hellman algorithm) to create a shared secret key, which is called master secrets in SSL terminology. From the master secrets, the browser and the server generate symmetric connection keys to be used during the connection.
All data (requests and web pages) sent to each other are then protected with these connection keys, where protection involves message authentication code and symmetric key encryption. An attacker cannot see the data transmitted between the browser and the server when the SSL protocol is used. Therefore, this type of protocol is often used to provide confidential information (such as a password or credit card number) to a user to access a particular website or service.
14. Quantum cryptography
„Unlike mathematical encryption, quantum cryptography uses the principles of quantum mechanics to encrypt data and making it virtually unhackable.” – Quantum_Exchnage
The above quote clearly describes the difference between the encryption methods based on the usual mathematical basis and quantum cryptography, which uses light.
The time required for hacking is estimated based on the current performance of the I.T. tools. If the performance of existing (algorithm-based) computers increases by leaps and bounds, the security of encryption procedures decreases accordingly.
As already mentioned, cryptography is the method and process for encrypting data: the sending parties encrypt their message somehow and ensure that the message is only accessible to the receiving party. How the message is encrypted to make it clear only for the sender and recipient can be completely different: this can be done in the form of smoke signals, using a mirror and sunlight, but of course, most often by using mathematical algorithms.

Photo by Anton Maksimov Juvnsky on Unsplash
14.1. What is quantum cryptography?
In the case of quantum cryptography, we use the principles of quantum mechanics to encrypt and transmit data in such a way that unauthorised persons will not be able to crack the data. More precisely, in quantum cryptography, or quantum key distribution (QKD), we use light particles (a series of photons) to transmit data from one location to another over a fiber optic cable.
In classical mechanics, objects exist in a given place at a given time. In quantum mechanics, however, objects exist in a certain percentage of probability; they have a certain chance of being at point A, another chance of being at point B, etc.
14.2. How does quantum cryptography work?
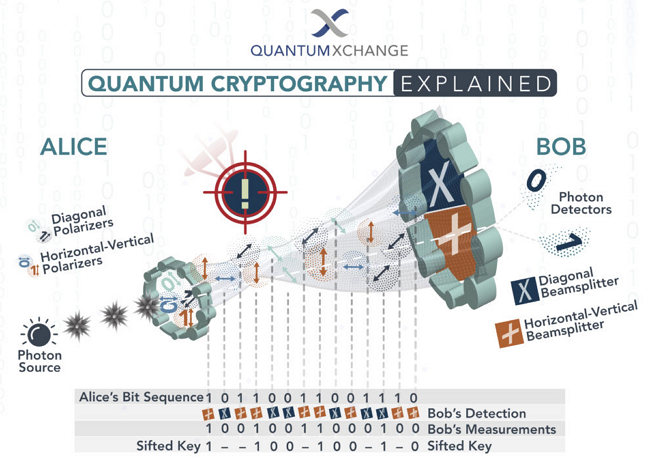
The schematic diagram below illustrates the operation of quantum cryptography. When using quantum cryptography, we send light particles from point A to B through an optical fiber: in this case, Alice sends a message to Bob.
But why a particular message is indecipherable in the case of quantum cryptography? Let’s think about exchanging messages with the help of the mirror and the sun already mentioned above. If we cannot see the other party’s mirror, so to speak, and the sender cannot send the message to us because someone is in the way of the light, we cannot interpret the message or perceive that something or someone is interfering with the transmission.
If someone tries to listen in on the conversation, he has to read all photons in the beam to read the secret. Then the eavesdropper must pass those photons to Bob. The listener changes the photons’ quantum state by reading the photons, introducing errors into the quantum key.
This change warns Alice and Bob that someone is listening and the key has been compromised, so they throw away the key. Alice has to send a new key to Bob that isn’t compromised, and then Bob can use that key to read the secret.
Source: Quantum Cryptography, Explained
For further details of quantum cryptography, please read the article: Quantum Cryptography, Explained.
14.3. Limitations of quantum cryptography
The cybersecurity industry expects quantum cryptography and quantum key distribution to solve cryptographic problems in the long run. Quantum cryptography requires very specialised and expensive tools, as quantum computers are needed (among others) to implement the technology. And while quantum computing dramatically increases the ability to analyse data in size and speed, it also creates new security threats, including the risk of hacking and espionage.
Still, a fundamental question arises: can unbreakable communication be realised by using quantum cryptography? Maybe, but mainly in theory. Hackers don’t get information by breaking encryption; they have much simpler tools for doing so. For example, they can access messages before they are encrypted or decrypted. In addition, it requires the use of QKD relays. Unless the sender and receiver establish a direct connection between the two endpoints and the distance is small enough to prevent compromised messages, this is up to 100 kilometres. There is also a need for routers and hubs that hackers can try as well.
When it comes to cybersecurity, it is imperative to think in systems. If only part of a given system is encrypted using quantum cryptology methods, input and output data can be intercepted and accessed in other parts of the system.
14.4. When will it spread?
How much longer do we have to wait for quantum cryptography to reach the general public? When will quantum computers become commonplace? This question is harder to answer than we might think.
Many people are worried about whether the data now encrypted will remain safe in the future. The use of quantum cryptography in critical communications and data protection becomes increasingly unavoidable in the future, and quantum-based computing is now expected to become more widespread.
14.5. European Quantum Communication Infrastructure
The European Quantum Communication Infrastructure (EuroQCI) initiative aims to build a secure quantum communication infrastructure across the EU. The member states are working with the Commission and the European Space Agency (ESA) to develop and establish the EuroQCI.
EuroQCI safeguards sensitive data and critical infrastructures by integrating quantum-based systems into existing communication infrastructures, providing an additional security layer based on quantum physics.
The SES consortium is developing a satellite and terrestrial network for the Quantum Communications Infrastructure (LuxQCI) project in Luxembourg, coordinated by the Luxembourg government.
15. The connection between data protection and encryption
“The Implementation of GDPR into law is a sensible and proactive approach to help protect data, systems and remove neglect and possible misuse or data breach of data.” - Alistair Dickinson
The purpose of the GDPR is to protect the personal data of EU citizens. It regulates the way data is collected, processed, stored, deleted, transmitted and used. The GDPR is, in fact, a good data management practice, but putting the regulation into practice is a serious challenge as it is a complex process.
Since the GDPR focuses on the protection of personal data and encryption plays an indispensable role in its technical implementation, the two are often inextricably linked.
The GDPR (General Data Protection Regulation) has been in force since 25 May 2016 and has become enforceable since 25 May 2018. GDPR does not provide technological solutions or guidelines to meet the expectations it defines but lays down very strict rules to protect data. The GDPR only deals with personal data that allows the data owner to be clearly identified (e.g. by name, email address, etc.).
Under the GDPR, the data controller ensures the fundamental right to protect the data subject’s personal data. The GDPR encourages us to weigh data management risks and determine the range of data requested and the need to store it.
In order to maintain security and prevent data processing in breach of the GDPR, the controller or processor must assess the risks arising from the nature of the processing and take measures to reduce such risks, such as using strong encryption. Therefore, when developing applications and designing database records, these regulations must be considered in advance.
Data protection is the totality of legal regulations related to the handling and protection of personal data, so it is not an information technology procedure. At the same time, encryption is an information technology (target) procedure in which we make data incomprehensible to persons who are not authorised to access personal data. Thus, personal data encrypted at the appropriate level is incomprehensible to a person who does not have access to it without a decryption key.

Photo by Privecstasy on Unsplash
There are several ways to encrypt data, but the question may also arise as to exactly what data should be stored in this way and in what situation we want to make it impossible, or at least difficult, to make unauthorised access to the data. Should only the database containing personal data, or the images, videos, sound files be stored encrypted?
16. You are not alone!
“Encryption is a sensitive issue for many actors, including governments, while most citizens are reassured by the fact that their conversations remain private. Our motivation to create Encryption Europe is to explain this technology in a simple way, based on the real-life experience of the companies who operate it on a daily basis.” - Jean-Christophe Le Toquin, coordinator of Encryption Europe
16.1. Encryption Europe
Encryption technologies are essential elements of digital trust. Whether in a personal or professional environment, private or public sectors, encryption ensures that the exchange of information is accessible only to authorised persons.
Encryption Europe is an association and industry alliance of European SMEs committed to making encryption simple, valuable and reliable for everyone. It aims to promote default encryption of communications, share best practices and organise European stakeholders around a shared vision.
Alliance members are working to promote strong and sustainable encryption techniques with a simple, understandable approach: any weakening of encryption, whether by creating backdoors or handing over keys to third parties, threatens trust in the digital system world.
“Luxembourg has a long tradition of protecting personal data. With this in mind, the Grand Duchy’s policy is to encourage innovative companies to develop encryption solutions in a stable regulatory environment.” - Pascal Steichen, CEO, SECURITYMADEIN.LU
16.2. Encryption Europe Members in Luxembourg
16.2.1. OnePrivacy SA
OnePrivacy is a company based in Luxembourg. Its product is called ‘Keexle’, a fully end-to-end encrypted communication and collaboration tool. Keexle is a feature-rich product that provides privacy while using file share, chat or the cloud.
16.2.2. SeeZam
SeeZam uses the latest data protection technologies and offers an online virtual safe service for individuals and businesses. It is a highly secure virtual storage space in the digital world, protected by robust authentication and encryption, offering the highest level of data security for its customers’ data.
16.2.3. Solutions.lu
SOLUTIONS SA is also based in Luxembourg, focusing on encryption. By using tetraguard® software technology, its clients can ensure that their sensitive data are in good hands.
16.3. CYBERSECURITY Luxembourg portal
Take a look at this portal and see how many companies in Luxembourg are involved at some level in the field of encryption. Go to the CYBERSECURITY Luxembourg portal, click on the ’Ecosystem – View on the community’ link, and choose ’Private sector – Solution and service providers’ from the drop-down menu. By clicking on the ‘Classification’ filter, a drop-down menu appears representing the ECSO classification options. This filter enables you to filter among the private sector entities according to the ECSO classification options.

Use the Classification filter, and choose the ’PROTECT – Encryption’ drop-down menu. You will be surprised and can be sure that you are not alone, as surprisingly many companies deal with this area and provide some help or service to protect your data.
17. How can SECURITYMADEIN.LU help?
“If you think cryptography will solve your problem, either you don’t understand cryptography, or you don’t understand your problem.” - Peter G. Neumann
17.1 SECURITYMADEIN.LU
SECURITYMADEIN.LU is the cybersecurity agency for the Luxembourg economy and municipalities. It provides extensive cybersecurity expertise and solutions to SMEs and companies of all sizes and municipalities through its three departments: CIRCL, CASES and C3, in close collaboration with the CYBERSECURITY Luxembourg ecosystem’s players.
17.2. CASES
CASES (Cyberworld Awareness Security Enhancement Services) has multiple services available to the public to raise awareness concerning cybersecurity. On its website, you may read several articles on data-related topics, like the confidentiality and integrity of data, data backups, data loss and proper data destruction.
In addition to professional CASES training sessions, you may also get valuable information on the SECURITYMADEIN.LU portal, where you can read articles, register for the Cybersecurity Breakfast series, watch the Lëtz Talk About Cyber series or read cybersecurity-related news, besides other things.
17.3. CIRCL
The Computer Incident Response Center Luxembourg (CIRCL) is also part of SECURITYMADEIN.LU, with the initiative to gather, review, report and respond to computer security threats and incidents. CIRCL is the CERT (Computer Emergency Response Team/Computer Security Incident Response Team) for Luxembourg’s private sector, communes, and non-governmental entities.
One of CIRCL’s services is information leak analysis (AIL framework), a powerful tool to analyse potential information leaks from unstructured data sources. It can be extended to support other functionalities to mine sensitive information.
Besides tools you may use, you can also find valuable advice on the CIRCL website about What to do when you can’t trust your communications channels or How to create strong passwords.
17.4. C3
By addressing all public and private sector actors, including start-ups, C3 (Cybersecurity Competence Center) brings together under one roof three fundamental pillars of digital security
- an observatory for current threats and vulnerabilities
- a training centre and simulation platform
- a laboratory to test new products and digital solutions
18. Conclusions
“Encryption is foundational to the future. So spending time arguing about ’encryption is bad and we ought to do away with it’— that is a waste of time to me. Encryption is foundational to the future.” - Admiral Michael S. Rogers, Commander of U.S. Cyber Command and Director of the National Security Agency
Securing data must be at the heart of our modern society and economy. We may say that encryption is a basis of data confidentiality, integrity and availability. In order to maintain the security of data, the active participation and responsible behaviour of all IT actors are necessary: the involvement of individuals, private- and public companies is needed.
Encryption is among the essential tools for managing the risk of a data breach. It is a critical tool for protecting sensitive data, including personally identifiable information (consider the link with GDPR), that can be used for identity theft. With identity theft, financial data can be used for fraud and other financial crimes. Weakening encryption increases the risk of data breaches, endangering individuals, critical infrastructure, the economy, and ultimately national security as a whole. The cybersecurity of critical infrastructure is heavily dependent on strong encryption.
Besides the above, there are many processes where encrypted communication is essential: online banking solutions or e-commerce are unthinkable without encrypted communication.
Our daily lives are so intertwined with cyberspace that the legitimacy and necessity of encryption have long been unquestioned. In digital space, encryption accompanies us step by step as an unseen law enforcement force to maintain order in cyberspace because, without it, there would only be chaos and anarchy.

Photo by FLY:D on Unsplash