- 01 Apr, 2021
- Topic of the Month

1. Introduction & Definition
‘Nuclear scientists lost their innocence when we used the atom bomb for the very first time. So, we could argue computer scientists lost their innocence in 2009 when we started using malware as an offensive attack weapon.’ — Mikko Hypponen
Malware is the abbreviation for ‘Malicious Software.’ Malware is any software that is intended to cause harm to your system or network. It is an umbrella term that describes any malicious program or code that is harmful to systems.
Malware can spread itself in the network, remain undetectable, and cause changes or damage to the infected system or network. Although malware cannot damage the physical hardware of systems or network equipment, it can steal, encrypt, or delete your data, alter or hijack core computer functions, and spy on your computer activity without your knowledge or permission.
The first computer viruses appeared in the late ’80s. At first, they infected computers via floppy disks during the replacement of programs. However, the spread of networks and the development of the Internet fundamentally changed the way they spread.
Initially, only trained programmers wrote viruses, but the privilege of the few soon became that of many. The entry of the less educated into the market began with the appearance of the first virus-making kits, and then with the advent of macro viruses, the number of malware has multiplied.
But what was initially created as a good joke, to annoy others, or as a strange way of self-realisation, is now liberated, spreading unstoppably, and causing unpredictable, immeasurable damage.
Nowadays, thanks to the explosive development of information technologies, more and more advanced, effective and efficient attack alternatives are emerging. The attack techniques are multifaceted, and one of their forms is an attack method called social engineering that exploits the weaknesses and vulnerabilities of the human factor. This technique makes it possible to obtain inside and confidential information by deceiving, exploiting, and manipulating a person or even infecting a device with malware.
Malicious programs often require human intervention to activate their malicious code or snippet of code. Therefore, it is imperative that you become aware of this phenomenon and its dangers and learn how to protect your devices effectively. Individuals and companies need to pay close attention to protecting their computers from computer viruses and other malicious software, as the risk is high.
This article briefly describes the birth, history, major types of malware and shows how to detect infection and protect your computer or system. Frightening data at the end of the study call attention to the severity of the phenomenon.
You have already taken the first step, and hopefully, this article will help you understand malware and provide some helpful tips for adequate protection.
2. The history of malware
‘I was addicted to hacking, more for the intellectual challenge, the curiosity, the seduction of adventure; not for stealing, or causing damage or writing computer viruses.’ — Kevin Mitnick
Malware attacks can be traced back to the time, even before the Internet became widespread. Below are some of the malware attacks in history:
The idea of a computer virus extends back to 1949 when John von Neumann, in his paper ‘Theory and Organization of Complicated Automata’, played with the thought that computer viruses might be able to reproduce themselves. Still, it took two decades for the earliest documented viruses to appear in the early 1970s. It is thought that the first self-replicating program (Creeper Worm) was created by Robert H. Thomas around 1970. This worm was able to copy itself to remote computers, where it displayed the message: ‘I’m the creeper, catch me if you can!’
However, the term ‘virus’ was not used until the 1980s. In his 1986 PhD thesis, Fred Cohen defined a computer virus in a single sentence as: ‘A program that can infect other programs by modifying them to include a, possibly evolved, version of itself.’
Perhaps even he did not think at the time that what was in the stage of theoretical proposition and experimentation would have a considerable impact on our lives in a few decades. The history of malware can be broken down into the following eras:
2.1. The early years
Malware was very rudimentary at first, spreading primarily through human-mediated floppy disks. However, with the development and spread of the Internet, they spread more easily and rapidly.
1971 Creeper: It was designed as a test to demonstrate that a computer program can move between computers.
1974 Wabbit: It is a quickly self-replicating program (got its name from ‘rabbit’) that slows down or even crash computers.
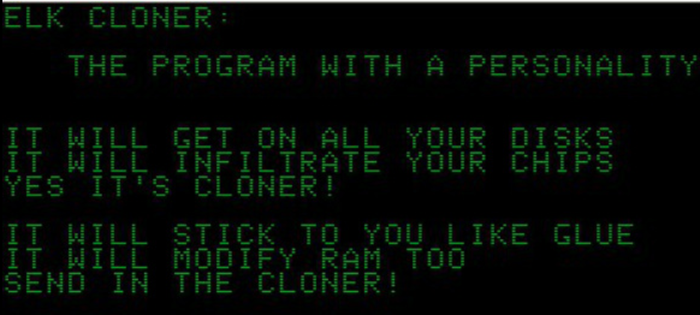
1982 Elk Cloner: Rich Skrenta, a 15-year-old boy, wrote it.
Initially, he made it as a joke, and he would give floppy disks to his friends. The code was attached to a game, and it was set to launch once the game was started up 50 times. Then the screen would go blank and display the poem below:
1986 Brain Boot Sector Virus: It is regarded as the first virus to infect MS-DOS computers.
1986 PC-Write Trojan: Once on a computer, it would erase all of a user’s files.
1988 Morris Worm: Nothing proves its significance better than the fact that the first CERT was created because of the Morris Worm.
‘On the evening of November 2nd 1988, Robert Tappan Morris, a 23-year-old Harvard graduate and student at Cornell University, released his “Christmas Tree Worm” (better known as the “Morris Worm”) from a hacked computer of the MIT. It was the first major network Worm, which caused over 6000 computers to crash and millions in estimated damages.’
As a consequence, he was the first malware author who was convicted for his crimes.
1999 Melissa Virus: It is the first mass-emailed virus, which used Outlook address books from infected machines to spread.
2.2. Second phase – between 2000 and 2010
Between this period, malware grew significantly, both in number and in how fast infections spread. Besides, we could see a dramatic increase in malware toolkits (like the Sony rootkit), and the number of compromised websites escalated correspondingly. As a new phenomenon, SQL injection attacks became a leading threat.
After 2000, malware is no longer a student prank or a joke, but a thing that can cause massive damage, which can force giant companies or government agencies to their knees.
2000 ILOVEYOU Worm: This worm infected an estimated 50 million computers via e-mail and cost more than $5.5 billion in damages.
2001 Anna Kournikova Virus: This virus was created by a 20-year-old Dutch student Jan de Wit. It spread via e-mails and was designed to trick e-mail users into clicking to open an e-mail attachment supposedly containing an image of the professional tennis player Anna Kournikova.
2003 SQL Slammer Worm: It is one of the fastest-spreading worms of all time: it infected nearly 75,000 computers in ten minutes. It also had a significant global effect, slowing Internet traffic worldwide via a denial of service.
2004 Cabir Virus: It is noteworthy because it is the first mobile phone virus.
2005 Koobface Virus: It is the first malware to infect PCs over social networking sites (if you rearrange its name, you may get ‘Facebook’).
2.3. Third phase – more sophisticated and profitable
Since 2010, we have seen a significant evolution in the sophistication of malware. Virus attacks are no longer isolated cases, masterminded by lone wolves, sole and savvy IT professionals to gain fame and enter their name in history.
Instead, a state-sponsored, well-funded development team often created virus attacks when facing a new way of organised crime. It also follows that attacks are much more elaborate, insidious, inconspicuous, and cause more significant and longer-term damage.
Nowadays, malware attacks outperform many traditional anti-malware systems and are directed against individuals, companies, military systems, government agencies, or hospitals.
2011 Zeus Trojan: This Trojan has become one of the most successful botnet software in the world, impacting millions of machines.
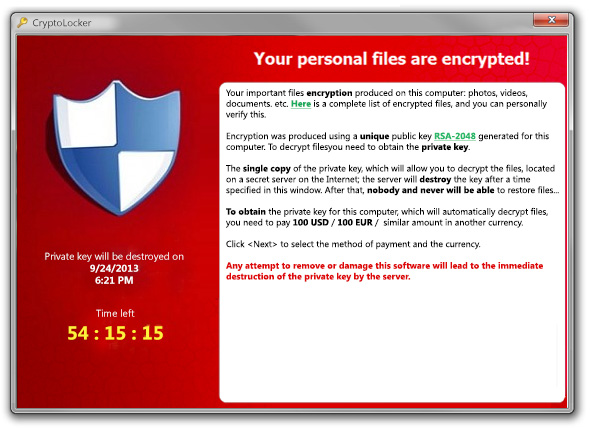
2013 Cryptolocker: It is ransomware that had a significant impact globally by infecting about 250,000 PCs. When activated, the malware encrypted certain types of files on Windows machines using RSA public-key cryptography, with the private key stored only on the malware’s control servers.
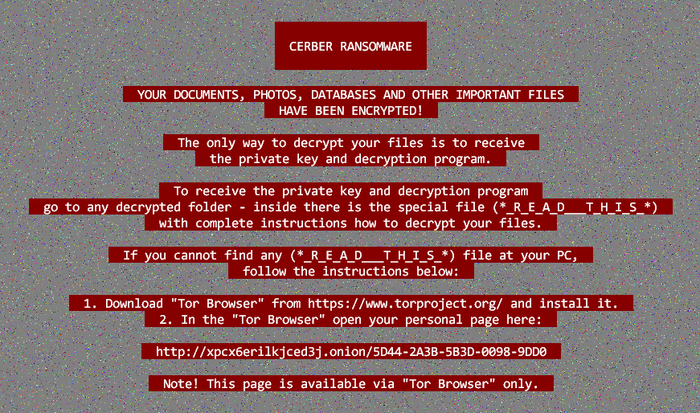
2016 Cerber: It is an evolved ransomware, a ransomware-as-a-service (RaaS). It means that the attacker licences this ransomware over the Internet and splits the ransom with the developer. This way, the attacker and developer can send more attacks with less work.
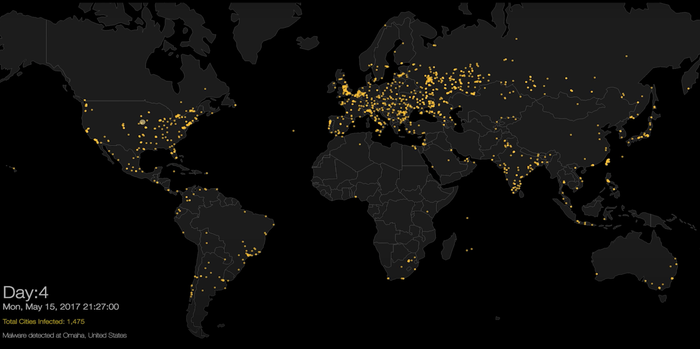
2017 WannaCry Ransomware: It is a crypto-ransomware, which caused the most significant ransomware attack in the Internet’s history.
The virus appeared in hospitals in the UK and soon spread over more than 230,000 computers and 150 countries in one day. The attack primarily affected computers in organisations that did not have the April 2017 security update for Microsoft. WannaCry attacked computers and systems through a vulnerability in the Windows operating system called EternalBlue. WannaCry was one of the first and most well-known malware to use this exploit to spread.
In the video below, you can see how many cities were infected in the first five days:
Users who no longer have Microsoft Windows systems running on their computers, such as Windows XP or Microsoft Server 2003, were at particular risk of vulnerability, as no official update has been released to their systems since 2014.
This attack also highlighted the importance and necessity of updating computers…
3. Types of malware
‘People’s computers are not getting more secure. They’re getting more infected with viruses. They’re getting more under the control of malware.’ - Avi Rubin
After a historical overview, let’s take a look at what types of malware we know. The expression ‘malware’ (short for malicious software) is an umbrella term for all kinds of software designed to damage or gain access to a computer without the owner’s knowledge or consent.
There are many forms of malware. They all contain malicious, unwanted code and thus cause a change in our devices that we did not want.
The figure below shows the main types
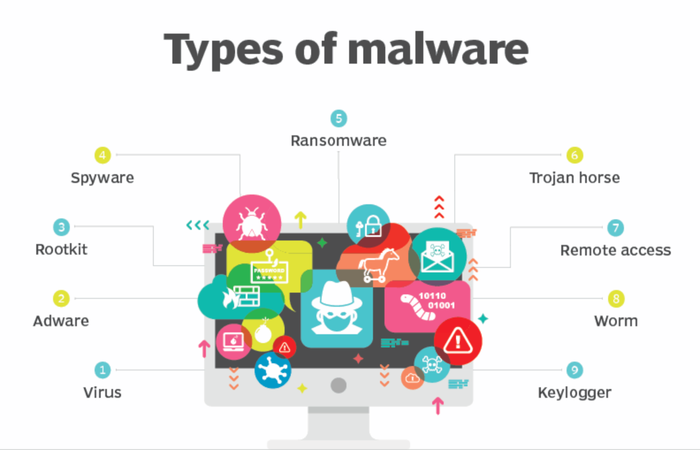
3.1. Viruses
A virus is the most common type of malware that can execute itself and spread by infecting other programs or files. It requires human intervention to run and propagate. There are many types of viruses possible (file viruses, macro viruses, master boot record viruses, stealth viruses, and polymorphic viruses). A virus is generally activated as soon as a person opens the file (attached to an e-mail or located on a removable medium) or runs the software hosting the virus.
3.2. Adware
Adware is unwanted software designed to display advertisements on your screen, most often within a web browser. They do not only disturb and distract but, of course, are resource-intensive, and thus slowing down your machine
3.3. Rootkits
A rootkit is created to obtain administrator-level access to the victim’s system. They are hard to detect and impossible to remove without formatting the system.
3.4. Spyware
Spyware is a program designed to collect personal data on users without authorisation and sending them to its designer, or a third party, via the Internet or any other computer network. The primary objective of spyware is to spy on the Internet user’s behaviour and transmit the information collected to the attackers.
There are different types of spyware:
Commercial spyware collects data and interacts visibly with its users by managing the display of targeted advertising banners, triggering the appearance of pop-ups, or even modifying the content of the websites visited to add commercial links, for example. These are the most common spyware. Their existence is generally mentioned in the licence to use the software concerned, but often in an ambiguous manner or in a foreign language, which means that the user is not clearly informed.
Cookies also collect data about their users but do so with the utmost discretion. The monitoring and possible reuse of the data collected are done without the users’ knowledge, generally, to collect statistics, marketing information, debugging or technical maintenance, or even cyber-surveillance. The existence of these cookies is deliberately hidden from users.
Integrated (or internal) spyware is an executable program included in the source code of the software. Its function is to give it the possibility of collecting and transmitting information over the Internet. This spyware can be downloaded separately or offered for installation simultaneously as other free programs, usually spyware, thanks to agreements between software publishers.
Outsourced spyware is a standalone application that dialogues with the main software associated with it. Its sole function is to take care of the ‘customer relationship’: collection and transmission of information, display of advertising banners, etc. Advertising agencies or specialised companies design this spyware.
3.5. Ransomware
Ransomware is a type of malware that encrypts the files on a victim’s device or a network’s storage devices. It encrypts the system entirely and asks the user for a ransom to decrypt the data. There is no surety whether the system will be decrypted even after the ransom has been paid.
3.6. Trojan Horses
A Trojan horse is spyware installed on a machine to open a back door to the attacker. Unlike a virus or a worm, a Trojan horse is not intended to reproduce or spread. But like viruses, Trojans hide in harmless files and often exploit human vulnerabilities to get launched. In general, the Trojan is used to create and maintain permanent unauthorised access to a machine when the latter is connected to the Internet.
- Data Sending Trojans: Steals data saved on your system and transmits it over to the attacker.
- Destructive Trojans: Destroys other files and services.
- Security software disabler Trojans: Disabled system firewall and antivirus so that other malicious files can be downloaded and run without getting detected.
3.7. Remote access
- Remote Access Trojans (RAT): They are also called ‘backdoor viruses’ because they secretly create a backdoor into the infected computer and enable the attackers to remotely access the computer without alerting the user or the system’s security programs.
3.8. Worms
Unlike the virus, a worm does not need human intervention to infect a machine, run and propagate in the network. It has an ‘engine’ (automation) that initially allows it to deliver and execute its malicious code automatically. The Morris Worm, named after its creator (Robert Morris), was one of the first worms (1988) to spread quickly on the Internet and infect many machines.
3.9. Keyloggers
They are also called system monitors. They record all the keystrokes for the keyboard, which might be helpful for password stealing by hackers.
4. Protect and Prevent: How to protect against malware?
‘A minimum precaution: keep your anti-malware protection up to date, and install security updates for all your software as soon as they arrive.’ — Barton Gellman
- Constantly update your operating system (turn on auto-updates)
- Automatically update and only use trusted antivirus and malware software
- Only buy apps from trusted sources
- Rely only on secure networks (encrypted)
- Install and use a firewall
- Backup data regularly
- Use browser with common sense
- Do not click on suspicious links or download attachments from unknown sources
- Stay up-to-date on the latest attacks
The first step is to keep all software you use up to date, including the operating system and all applications. Not only to install new features and enhancements, fix bugs, but also to fix vulnerabilities that cybercriminals and their malicious code can exploit.
Always stay alert, use common sense, be aware of the latest or ‘trendy’ threats and vulnerabilities. Do not open attachments from an unknown recipient. You can also use a website reputation rating tool, which comes in the form of a browser plugin, to warn you if you try to go to potentially dangerous websites.
Do not forget that the weakest link to the most effective infections is the user himself, even today. Well-designed e-mails with malicious attachments are proven to be effective yet inexpensive ways to cause harm and damage. The impact of infection can be multiple, such as the loss of confidentiality, integrity or availability of an entity’s assets. A malicious code infection is not always noticeable, and sometimes it is even challenging to detect.
Organisations may implement a ‘malware response plan,’ similar to the one below:
5. How do I get malware?
‘Viruses don’t just happen; people write them deliberately.’— Peter H. Gregory
Anytime you are online, you may get infected: while you surf hacked websites, view a legitimate site showing malicious ads, download or install applications or files from an unfamiliar or not trusted source.
Malware is usually delivered via e-mail ‘phishing’ or fraudulent links. Also, malicious apps and infected USB sticks can easily compromise smartphones and computers.
And of course, we should not forget the malicious e-mail attachments, which are also very common intermediaries. The best practice is to stick to trusted sources and only install reputable applications and download them from the vendor’s official website. Even in this case, pay attention to permission requests and check whether you are downloading something extra (a potentially unwanted program or PUP), which is often presented as a necessary component, but it usually isn’t.
Bundled Free Software Programs
Free software companies often partner with other companies to bundle additional software within the download. They usually do so to sell their software for free and earn revenue from their partners, whose products are often invisibly downloaded along with the original free software. Most of these PUP programs are toolbar add-ons, but they can often include other programs, such as spyware and sometimes browser hijackers. Most of the time, these programs only slow down your machine, but they can even steal sensitive data if you install spyware or keyloggers with them.
Scareware
Scareware, also known as rogueware, is malware that masquerades as Internet security software. Users are presented with a pop-up, notifying them that their computer is infected, which is not. The program offers to clean our machine from malware by clicking on a link, but we click on the link to arm the malware.
Removable Media
USB drives offer a convenient method to store and move files between computers that are not digitally connected. If you are using USB drives to transfer files across several devices, it makes you vulnerable to malware. But it is not only the data stored by a USB stick that can transmit malware infection: the firmware can also be an agent. Firmware is software embedded in the device’s hardware and used for the USB stick’s basic functioning. Since the malware is hidden in the firmware and not the stick’s storage area, it is tough to detect. In addition to USB, external hard drives, CDs, and DVDs can contain malware if connected to an infected computer.
File Sharing, BitTorrent, and other Peer-to-peer File Sharing Services
Using the BitTorrent client, users can download media with peer-to-peer file sharing. These files usually travel on multiple computers, not all of which may have Internet security software so that they can be easily infected with malware. In addition, hackers may create fake files on these networks, which many people can then download.
Not using an Internet security software program
It needs no explanation how much danger we put ourselves in if we do not use antivirus software … or if we use one but do not turn on the automatic update.
6. Detect and React: How to detect malware?
‘I think computer viruses should count as life. I think it says something about human nature that the only form of life we have created so far is purely destructive. We’ve created life in our own image.’ — Stephen Hawking
6.1. The signs to watch out for
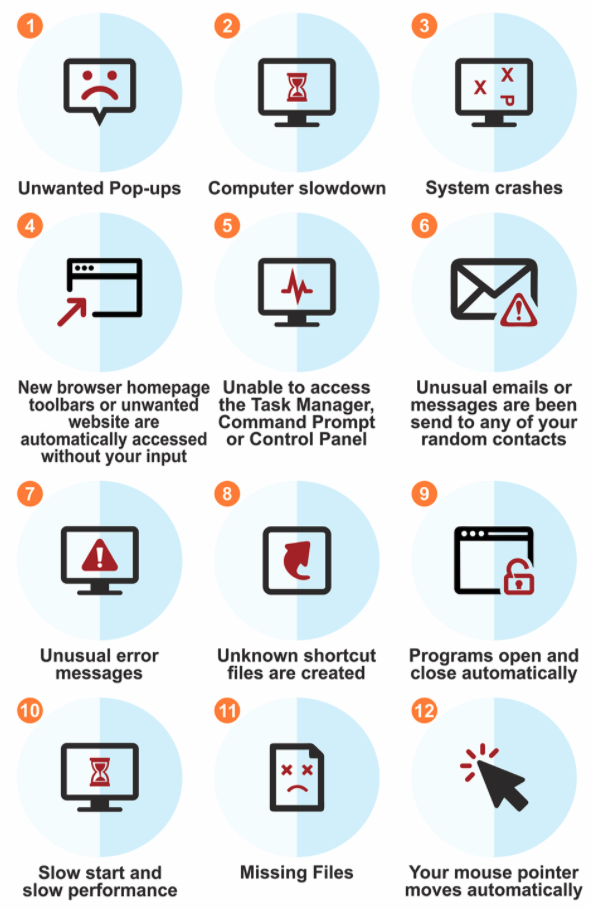
There are many reasons or behaviour of your computer which might show that it is infected. In fact, any behaviour that is unusual or not normal may give rise to suspicion. Keep in mind, though, that by the time you start seeing signs of a malware attack, your system is probably already infected. The best defence is prevention, but it is always worth staying alert and paying attention to the following warning signs:
1. Unwanted pop-ups
Unexpected and recurring ads and pop-ups on your computer are signs of a spyware infection. Some pop-ups may contain malicious code: they may distribute adware, spyware and more destructive malware types. Clicking on one of these pop-ups could install a keystroke logger with the ability to access any confidential data from passwords and bank account details to tax information.
2. Your computer becomes extremely slow and unresponsive
The most common signs are that your computer is slowing down, warming up, and your computer’s fan is running loud and at full speed. It can be a suspicious sign that your computer is a member of a botnet, someone is running a DDOS attack on it, or maybe mining cryptocurrency. Unnecessary services or programs may also run, which are using the CPU’s processing power.
3. Your system crashes
Your machine can freeze, or the Blue Screen of Death (BSOD) appears on your screen after a fatal error on Windows systems. Also, your computer shuts down or reboots when you did not initiate the process.
4. Your browser settings change
Just like your browser settings, other default settings might change: maybe your default search engine changed without any notification and your initiation. Your homepage may have changed, new toolbars, extensions, plugins installed, or any random website gets opened automatically. All the above indicate that you may have downloaded some unwanted software.
5. Unable to access Task Manager, Command Prompt or Control panel
All of these signs suggest that your computer is infected, and control of the computer may already be in someone else’s hand.
6. Unusual e-mail traffic/unwanted e-mail sending to random contacts
It can be a sign of malware infection if your contacts start receiving e-mails or instant messages by your name from any of your social media platforms asking them to visit a site, click on a link, join a group, like a comment, or download and install an application. It can happen if your account has been infected with a virus that is in the process to spread to different computers through your account.
7. Unusual error messages
Unexpected or unusual dialogue boxes, fake virus warnings, error messages can be a sign of malware infection. Also, error messages showing missing or corrupt file folders suggest that your PC has been compromised and its performance is affected.
8. Unknown shortcut files are created
A shortcut file virus is a kind of worm or Trojan that hides all your documents, files and folders and replace them with all shortcuts which look the same. When you open these shortcuts, the virus runs and infects your PC.
You may also begin to suspect a malware infection if you find random folders or shortcuts inside folders or cannot delete certain types of files.
9. Programs open and close automatically
Some malware may shut down or restart your computer to complete their installation process or to block antivirus scans: some ransomware is well known for shutting down computers when the user tries to remove them. Random restarts are more common than complete shutdowns, though: malicious software sometimes needs to refresh or update just like any other program.
10. Slow start and slow performance
This is probably the most common symptom when your computer is malware-infected. Malware can consume a substantial amount of your computer’s memory, leaving limited resources for other legitimate programs to use. Malware can lead to the highly sluggish performance of vital programs, like your Internet browser or operating system and a slow PC overall.
11. Missing files
If you see an unusual error message stating that you have missing or corrupt files on your computer, it could be a warning sign that your machine is infected with malware.
12. Your mouse pointer moves automatically
Your mouse cursor may keep moving on its own in case your machine is malware-infected.
There can be further signs of malware infection, of which the following are worth mentioning:
Unjustified, weird, and unnecessary traffic patterns
There is a spike in your Internet activity: if you check your browsing history, you find destinations you never targeted. Once certain malware (like Trojans, botnets, spyware) is landed on your computer, it reaches out to the attacker’s command and control server (C&C) to download a secondary infection, often ransomware. This action may explain the otherwise unjustified traffic that occurred against our knowledge or will.
Your antivirus software stopped working
Your antivirus stops working, and you cannot turn it back on.
6.2. Tools to react
CIRCL is one of the departments of SECURITYMADEIN.LU, and also the member of CERT.LU.
CIRCL gathers, reviews, reports, and responds to computer security threats and incidents. Its team members fight in the front line of cyberattacks and provide first aid following a cyberattack: CIRCL is the CERT (Computer Emergency Response Team/Computer Security Incident Response Team) for the private sector, communes, and non-governmental entities in Luxembourg.
- Passive DNS is a tool from CIRCL, a database storing historical DNS records from various resources, including malware analysis or partners.
- MISP is a platform where members from public and private sectors can exchange indicators of compromise to detect, prevent or respond to a security incident.
- The AIL framework has been extended recently with Yara Rules to support its functionalities to mine sensitive, suspicious or malicious information.
- CIRClean is an independent hardware solution from CIRCL to clean documents from untrusted (obtained) USB sticks.
Passive DNS
Passive DNS is a tool from CIRCL, a database storing historical DNS records from various resources, including malware analysis or partners. Access to this service is required from CIRCL. Once got the access, you may query Passive DNS servers, parse the results and process them in other applications.
MISP - Open Source Threat Intelligence and Sharing Platform
Another vital and valuable tool against malware is MISP Open Source Threat Intelligence and Sharing Platform (formerly known as Malware Information Sharing Platform). It is developed as an open-source software by a group of developers from CIRCL and many other contributors.
Information sharing on cybersecurity threats has become highly critical, and reinforcing the need for more cooperation across borders, individuals, and organisations is vital in adequate protection against cyberattacks.
MISP was developed to improve automated detection and responsiveness to target and cybersecurity attacks in Luxembourg and outside. It is a platform where members from public and private sectors can exchange indicators of compromise to detect, prevent or respond to a security incident.
More than 6000 organisations are using MISP worldwide in the framework called MISP Project.
Yara Rules
Yara Rules is an open-source tool used mainly but not exclusively to identify and classify malware based on a string or binary pattern matching. Victor Alvarez of Virustotal originally developed it to describe patterns that identify particular strains or entire malware families. Since it is an open-source project written in raw C and provided freely via GitHub, you can create descriptions of malware families based on textual or binary patterns.
AIL - Analysis Information Leak
The AIL framework has been extended recently with Yara Rules to support its functionalities to mine sensitive, suspicious or malicious information.
CIRCLean
Malware regularly uses USB sticks to infect victims, and the abuse of USB sticks is a common vector of infection. CIRCLean is an independent hardware solution from CIRCL to clean documents from untrusted (obtained) USB sticks. The device automatically converts untrusted documents into a readable but disarmed format and stores these clean files on a trusted (user owned) USB stick. CIRCLean is also free software provided by CIRCL.
7. Statistics on malware
‘In 2010, McAfee thought it impressive that it was discovering a new specimen of malware every fifteen minutes. In 2013, it was discovering one every single second!’ — P.W. Singer
7.1. Global malware statistics
The majority of statistics come from the US. The general findings below on a global level come from PurpleSec’s 2021 Trend Report.
The Threat Cloud World Cyber Threat Map tracks how and where cyberattacks are taking place worldwide in real-time.
A similar tool is the D4 Attack Map, created by CIRCL from SECURITYMADEIN.LU, which is a visual representation of real-time SSH brute force attacks. The D4 Project is a large-scale distributed sensor network project to monitor DDoS and other malicious activities by CIRCL and co-funded by the Innovation and Networks Executive Agency (INEA).
This open-source, distributed and collaborative security monitoring platform collects and analyses DDoS information from multiple types of Internet-based networks, then disseminates it real-time to CSIRTs platforms using MISP (Open Source Threat Intelligence Platform). The aim of the D4 Project is to make the creation and maintenance of such a network efficient and straightforward.
7.2. The top four malware
If we check the top malware families (a group of applications with similar attack techniques), we can find similarities between the global and the EMEA figures:
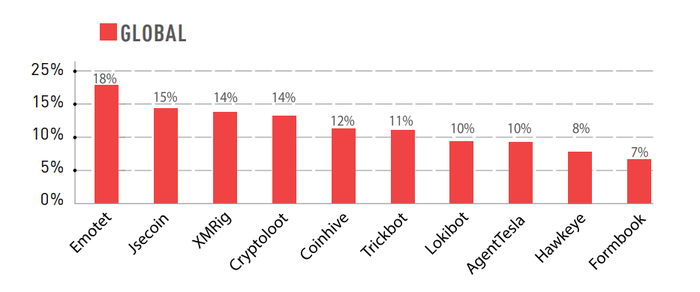
Emotet, Jsecoin, XMRig and Cryptoloot are the four most prominent malware.
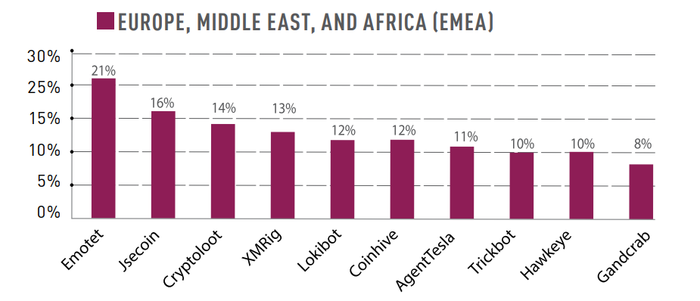
Emotet: Advanced, self-propagate and modular malware, created initially as a banking Trojan. It has been used recently as a distributor to other malware or malicious campaigns. It uses several methods to maintain persistence and evasion techniques to avoid detection. It can be spread through phishing e-mails containing malicious attachments or links.
Jsecoin: It is a JavaScript miner that can be embedded in websites.
XMRig: It is an open-source CPU mining software used for the mining process of the Monero cryptocurrency.
Cryptoloot: It is also a Crypto-Miner: it uses the victim’s CPU or GPU power and existing crypto mining resources.
7.3. Mobile malware
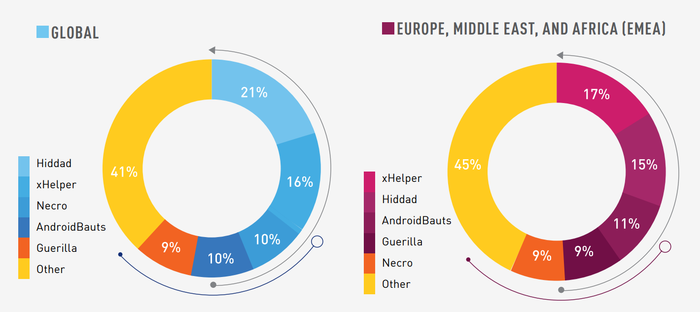
Malicious programs have become more widespread in recent times as smartphones have gained ground. Malware targeting smartphones, specifically Android, has increased by more than 76% in recent months. Hiddad, xHelper are the two most prevalent malware on smartphones:
7.4. Alarming malware statistics
It is not easy to provide comprehensive and accurate statistics, as the name malware itself is an umbrella term used for several things altogether.
- 92% of malware is delivered by e-mail (while cybercrime went up by 600% due to COVID-19 Pandemic)
- 99.9% of discovered mobile malware is hosted in third-party app stores
- 98% of mobile malware target Android devices
- 51.45% of all malware are Trojans
- Malware and web-based attacks are the two most costly attack types
- Over 18 million websites are infected with malware at a given time each week
- 34% of businesses hit with malware took a week or more to regain access to their data
According to Check Point experts, the increase in the number of unknown malware remains exponential and continuous. While companies face more malware than ever before, employees download another piece of malware every four seconds. Smartphones and tablets account for 60 percent of the time spent ‘consuming’ digital content. In the vast majority of cases, employees do not want to cause damage to corporate networks, yet one in five does so by installing unwanted programs or misusing Wi-Fi.
In 75 percent of the incidents investigated, malicious e-mails are the primary weapon of attackers. What’s thought-provoking is that 85 percent of threats are only revealed after malware has entered corporate systems.
Below you can read some snatched and exciting data from which trends and the sad reality can be drawn.
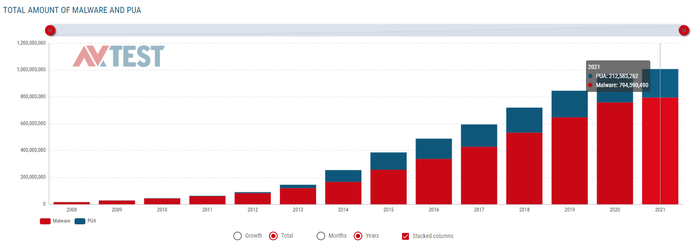
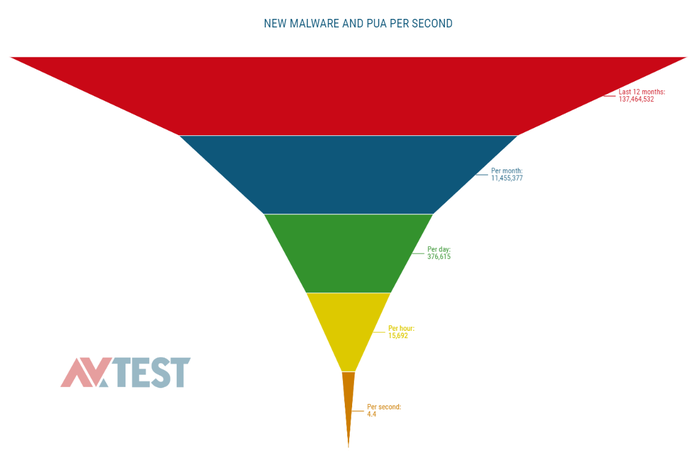
The graph below shows the total number of malware and PUA (potentially unwanted application) detected by the AV-Test Institute since 2008:
The number of known malware is enormous (more than 791 million), and it is hard to comprehend what it means. Perhaps we can better sense the uphill battle we are waging against them if we look at how many new malware variants are being born over time. The AV-TEST Institute registers over 350,000 new malicious programs (malware) and potentially unwanted applications (PUA) every day.
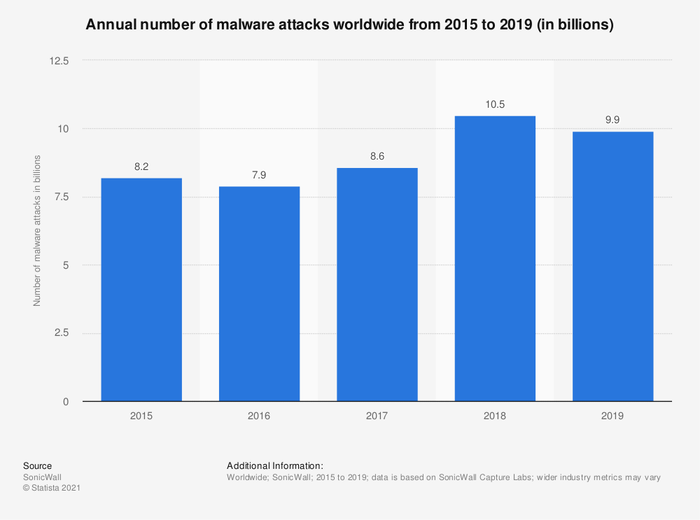
As per Statista.com, 9.9 billion malware attacks were carried out worldwide in 2019, which is still less than the 10.5 billion figure measured in 2108.
These vast numbers are challenging to imagine or interpret. Perhaps it is more tangible to understand how much malware there are and to what extent their numbers increase if we look at the changes over time. The graph below shows the newly discovered malware and PUA samples per second, hour, day, month and year. The figure below shows that the AV-TEST Institute registers 4.4 new malware per second, 15,692 per hour, 376,615 per day, 11.455.377 per month and reported 137.464.532 in the last 12 months.
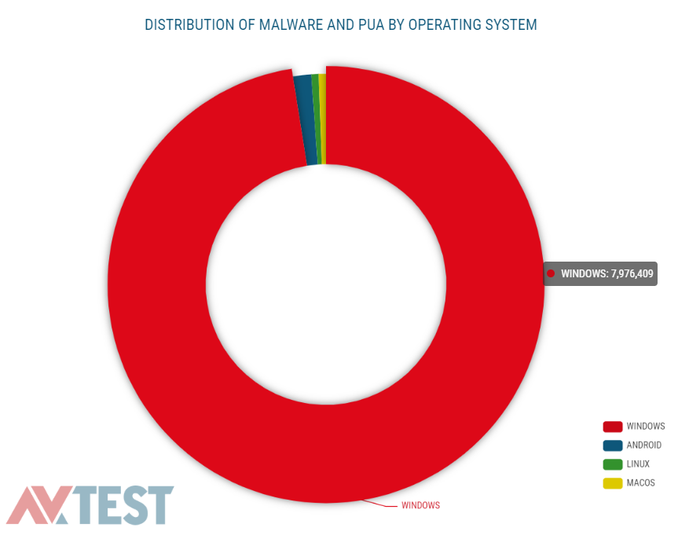
The following graph shows the total stock of malware and PUA collected by AV-TEST, subdivided according to their frequency of occurrence per operating system. It is clear that malware affects the Windows operating system the most:
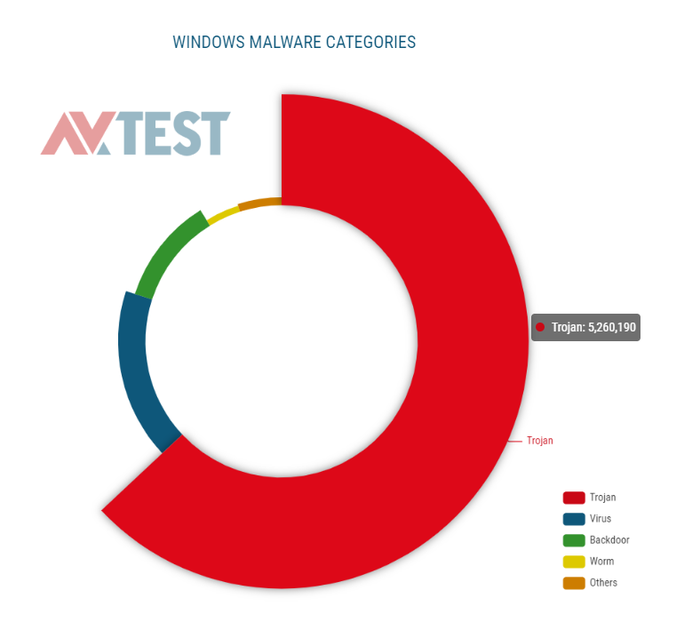
If we look at the types of malware that attack through the Windows operating system, we can see that Trojans can be held responsible for most of the cases:
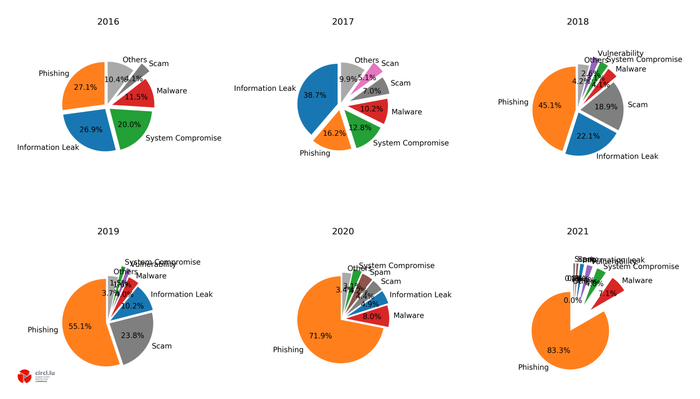
7.5. Malware in Luxembourg
The department belonging to SECURITYMADEIN.LU, CIRCL, also compiles statistics on threats reported to them in Luxembourg. The figure below shows data from 2016. Although the majority of cases received were phishing, it is clear that malware and system compromises have been ubiquitous for the past six years. Malware running on mobile phones has also been regularly reported since December 2016.
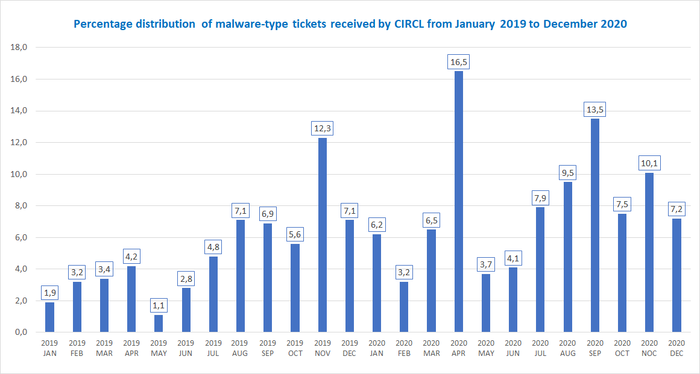
The graph below shows the percentage of malware-related incidents at CIRCL on a monthly basis from January 2019 to December 2020.
8. You are not alone!
‘I think malware is a significant threat because the mitigation, like antivirus software, hasn’t evolved to a point to mitigate the risk to a reasonable degree.’ — Kevin Mitnick
This chapter briefly lists and presents the companies that are part of the Luxembourg Ecosystem and provide antivirus or anti-malware solutions.
8.1. G-SYS
Besides providing support regarding consulting and audit, data security, cloud services, storage, IT infrastructure and product sourcing, G-SYS has substantial IT security experience (Antivirus, Anti-Spam, Firewall). G-Sys SA is a sole reseller and integrator of its ‘MAAS’ (Malwarebytes as a Service) service in Luxembourg.
8.2. Dartalis
Dartalis was founded in 2001 to provide smart security solutions for companies in the fields of Industry, transportation, System integrators, Finance, Healthcare and Service Providers. Dartalis is a regional leader and an independent company focused on information security.
8.3. Rcarré
Founded in 2001 in Luxembourg, Rcarré established itself in Belgium to provide its IT skills and services to small and medium enterprises. Rcarré provides data encryption solutions, authentication, Data Loss Prevention (DLP), prevention of external attacks (antivirus, ransomware, malware).
8.4. MGK Technologies
Created in 2001, MGK Technologies is an independent business specialised in the distribution and support of IT security software. Throughout an extensive network of resellers, MGK Technologies is an exclusive distributor of ESET in Belgium and Luxemburg. They provide anti-malware protection for individuals as well as businesses.
8.5. EASI
EASI provides Wi-Fi protection, endpoint security and security audits. Their product, Next-Gen Endpoint Protection, uses technologies like Behavioral Analysis, Exploit Mitigation, Deep Learning and Traffic Detection to offer better protection.
Next-Gen Endpoint solutions help control the damages, provide remediation capabilities and provide forensics insights to have complete information about what happened to be able to take the necessary actions.
8.6. ION
Serving Luxembourg’s IT needs since 2002, ION Group has focused its activities on three pillars: ION Home (IT services for home users), ION Pro (IT services for small and medium businesses) and ION Development (website design, development, app development).
Network setup and configuration, computer repair and maintenance, e-mail and hosting services and network security are among its portfolio.
8.7. itrust consulting
Itrust is an acronym for ‘Information Techniques and Research for Ubiquitous Security and Trust.’ Since its foundation in 2007, this Luxembourg-based company has become a recognised actor in the field of Information Security in Luxembourg and Europe.
Itrust Consulting is specialised in Information Security Systems. Itrust helps its customers to protect their information against divulgation, manipulation, or unavailability. Its services are related to building, implementing, and auditing Information Security Management Systems, assessing and treating risks with its TRICK Service tool, and deploying security experts whenever needed (SECaaS, or Security as a Service).
8.8. Malware.lu
Malware.lu CERT is the first private CERT/CSIRT (Computer Emergency Response Team/Computer Security Incident Response Team) in Luxembourg. Malware.lu CERT is part of itrust consulting. It is currently operated with the support of the H2020 project ATENA financed by the EU.
Malware.lu provides malware analysis, reverse engineering, incident response, and forensic investigations. They also offer two training courses (on malware analysis and reverse engineering).
8.9. STIDIA
STIDIA provides a full range of IT security services from vulnerability audits, penetration tests, source code audits, secure managed hosting, network engineering, and sensitive apps programming.
From the beginning, STIDIA has focused on increasing and improving IT security for the public. STIDIA quickly gained recognition from leading companies in various fields in Luxembourg and established its reputation as a security expert by partnering with world-renowned companies in areas such as banking, space, public services and much more.
8.10. ABAKUS IT-SOLUTIONS
ABAKUS is active in Luxemburg, Belgium and Europe (EU, NATO) and works in the industrial and financial sectors. There are firewall, VPN and mail router services, and networking monitoring services in their portfolio. ABAKUS IT-Solutions is an expert in installing FORTINET Firewalls and mail routers.
8.11. Netlux
Netlux proposes services from Netlor and the RAS group, benefitting from about 20 years of technical knowledge and expertise in engineering, IT support, storage and cybersecurity. One of their products is the Kub Cleaner (KUB stands for Kiosk for Universal Blocking). Knowing that 30% of network infections in business come from contaminated USB storage media, the significant advantage of using KUB is that it disinfects USB devices to protect your network from infections caused by USB storage media.
9. Test and Improve: How can SECURITYMADEIN.LU help?
‘It’s time to wake up and smell the Mutating Hash! Signature Based Malware Detection is Dead. Machine learning based Artificial Intelligence is the most potent defence the next-gen adversary and the mutating hash.’ — James Scott, Senior Fellow, Institute for Critical Infrastructure Technology
9.1 CERT.LU
CERT.LU (Cyber Emergency Response Community Luxembourg) is a community that brings together key cybersecurity actors and their expertise to provide a rapid and targeted response to a possible cyberattack and minimise damage and accelerate recovery. CERT.LU has three principles, as follows:
1. Improve the security posture of Luxembourg
2. Share for advanced cybersecurity actions
3. Help citizens and organisations to raise their security defences
9.2 CASES - Cybersecurity Awareness and Security Enhancement Services
CASES (Cybersecurity Awareness and Security Enhancement Services) is also part of SECURITYMADEIN.LU. This department was created in 2003 because of the ‘I love you’ virus.
It has multiple services available to the public to raise awareness. The goal is to give every organisation the necessary tools and information to define their risk maturity and improve it. CASES offers the following tools:
Fit4Cybersecurity: a self-assessment tool to help business owners implement a better cybersecurity strategy. This free online survey aims to assess the maturity of an organisation in terms of applicable good practices in the field of information security.
CASES Diagnostic: a CASES expert visits your organisation (in Luxembourg) and presents a 2-hour-long interview. The expert will identify vulnerabilities, evaluate the level of maturity concerning your information’s security, and issue recommendations.
Monarc (Optimised Risk Analysis Method): a tool and method allowing optimised, precise, and repeatable risk assessment.
TACOS (TrustApp CASES for Obvious Security): a cybersecurity awareness application.
It is a mobile app to educate users about cybersecurity risks with short articles, videos, tips, & tricks.
Besides the above tools, the CASES website contains a large number of valuable articles on cybersecurity. These are the most useful in terms of malware
- Malicious Software: Best Practices Against It
- SOS – I Think my Computer is Infected
- Security Measures for Small and Medium-Sized Enterprises – Threats to Software
9.3. C3 - Cybersecurity Competence Center
On October 12th, 2017, the C3 (Cybersecurity Competence Center), a national center for cybersecurity skills, was inaugurated.
Addressing all public and private sector actors, including start-ups, C3 brings together under one roof three fundamental pillars of digital security:
- an observatory for current threats and vulnerabilities
- a training center and simulation platform
- a laboratory to test new products and digital solutions
The Center’s flagship product is Room#42, which is a cyberattack simulation game. If you do not only want to read about threats but also experience a cyberattack, Room#42 is an unmissable and lifelong experience.
10. ENISA Threat Landscape 2020
‘We worried for decades about WMDs – Weapons of Mass Destruction. Now it is time to worry about a new kind of WMDs – Weapons of Mass Disruption.’ — John Mariotti
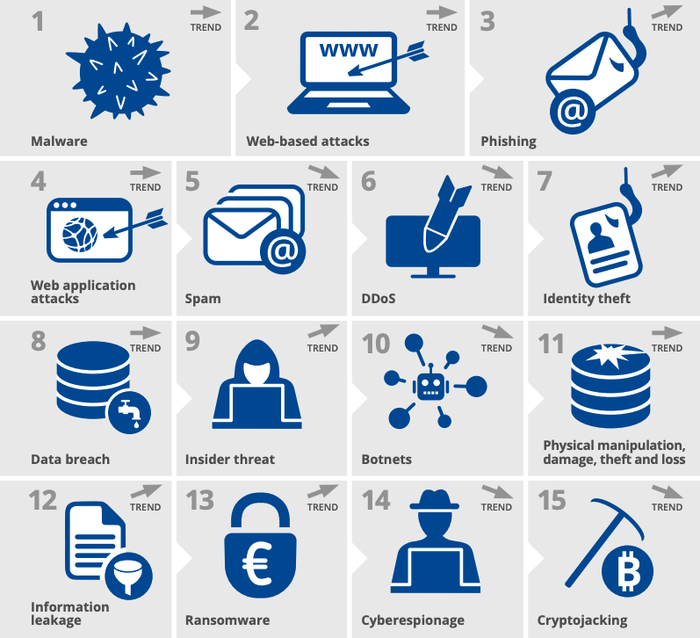
The European Union Agency for Cybersecurity (ENISA) has recently published its Threat Landscape Report for 2020, identifying and evaluating the top 15 cyber threats for January 2019-April 2020. According to the report, malware is the most significant cyber threat in the EU:
The report warns that the changes in work and infrastructure caused by the COVID-19 epidemic have weakened existing cybersecurity measures. Simultaneously, there has been a surge in personalised cyberattacks by cybercriminals using increasingly sophisticated methods and techniques.
So, we have become more vulnerable due to the pandemic, while the methods of attack are becoming more sophisticated, more and more difficult to defend and detect.
11. Conclusions
‘Today there is big money for those who can stealthily invade computer networks, or construct a secure botnet, and no modern military arsenal is complete without state-of-the-art malware.’ — Mark Bowden, Worm: The First Digital World War
As technology evolves, attackers constantly find new ways to breach defences and wreak havoc in cyberspace. About 15 years ago, you would have never heard of breaches and IT security issues, but it has become pretty common nowadays.
Rules of engagement have changed over time, and data is now more valuable than ever. The attackers now leverage ‘defensive’ tools such as encryption to remain undetected and gather as much information they can to resell it or earn profit in other ways. An excellent example of a diverted use for offensive’s purpose is encryption in malware and ransomware.
The Internet of Insecure Things
As the Internet of things becomes more widespread, more systems will become vulnerable to manipulation and compromise.
Poorly protected IoT devices can be easily transformed into malware hotbeds using them as botnets by hackers. These botnets pose a significant threat: these are made up of a plethora of infected devices and are designed to perform tasks (overload attacks, DDoS) that require heavy computing capacity.
Automated malware creation on a massive scale
One concern is the automation of development for new malware variants. Using machine learning techniques to detect and disassemble malware, attackers can collect thousands of functionally different malicious codes patterns every day.
No longer are minor changes designed to fool intrusion detection and prevention systems; these variants may change purpose and design, overwhelming defenders.
Increased use of encryption
Attackers find newer and newer ways to encrypt their malicious codes, so defenders find it challenging to analyse, prevent or neutralise these threats. Coupled with the threat of massive automated malware creation (mentioned above), improvement in obfuscation techniques significantly reduce the percentage of samples that information security companies can analyse.
Attackers might outpace defenders
Advanced machine learning techniques can allow malware authors to produce hundreds of thousands of new versions of their code every day. Each new variant can come with a different design and functionality flooding the defenders.
The benefits of machine learning are also used in defence to detect new malware, but the question is who can anticipate and neutralise the other party’s step in this killer race?
Humans will remain the weak link.
As cybercriminals develop newer and newer methods, people need to stay alert and follow the malware market’s changes and trends. People need to recognise that threats are not only threatening their laptops or PCs, but smartphones and smart devices and other mobile devices are increasingly exposed to cyberattacks and malware.