- 03 May, 2021
- Topic of the Month

1. Introduction & Definition
‘Ransomware is unique among cybercrime because in order for the attack to be successful, it requires the victim to become a willing accomplice after the fact.’ - James Scott, Sr. Fellow, Institute for Critical Infrastructure Technology.
1.1. What is Ransomware?
Ransomware is a type of malware (malicious software) that encrypts the files on a victim’s device or a network’s storage devices. Yes, this malware can infect not only desktop computers but also mobile devices, smartphones, and tablets as well.
Ransomware mainly makes the lives of companies and public institutions bitter - most of the major attacks have initially been linked to, for example, health care facilities or some other public body. Not coincidentally, outdated machinery and software offer the opportunity to scammers. But ransomware does not distinguish among victims: a private person can become a victim just like a huge corporation.
Ransomware often threatens the victim with permanent data destruction unless a ransom is paid to the cybercriminal. The ransom usually has a time limit on it: if the victim cannot meet the deadline, the files on the infected machine become inaccessible forever. The payment usually should be made through a tough-to-trace electronic payment method such as Bitcoin.
The ‘popularity’ of extortion viruses is also due to the fact that, by searching the right place on the net, you can buy ‘kits’ that can be used to make your own version of it without minimal technical knowledge. The ransom can also be requested in cryptocurrency, so the chances of falling are pretty minimal.
Although it lags in its prevalence and frequency far behind phishing attacks, its significance is that our files may remain inaccessible to us forever. Data can be very valuable: let it be a company’s confidential financial plan or drug research data from a research institute or old family or childhood images which loss is invaluable.
2. The Evolution of Ransomware Attacks
‘Your computer system should look like an ancient castle surrounded by various walls: the treasure is kept in the center and attackers have to fight past the walls, one by one, to reach their goal.’ - Andra Zaharia
2.1. An AIDS conference, a Harvard-educated biologist, and the first ransomware…
The earliest variants of ransomware were developed in the late 1980s: the first ransomware virus predates e-mail and was distributed on floppy disks by the postal service, and payment was required via snail mail.
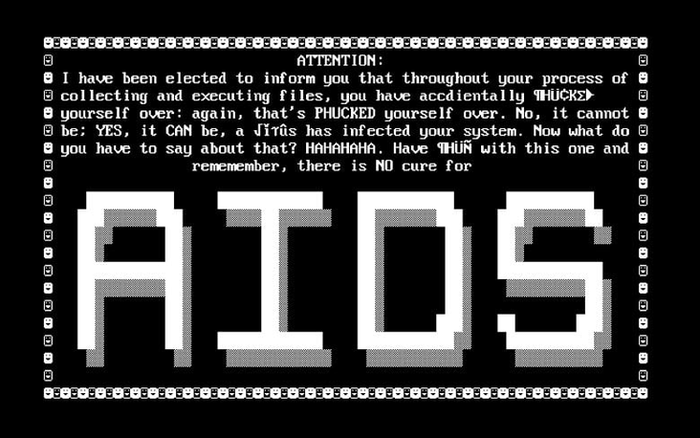
The AIDS Trojan, also known as the PC Cyborg virus, was the first-ever ransomware virus documented. This ransomware was built by a person you would least expect: Dr. Joseph L. Popp, a Harvard-educated evolutionary biologist. He attended the World Health Organization’s AIDS conference in December 1989 and distributed his infected floppy disks to unsuspecting victims.
The disks were labelled as ‘AIDS Information - Introductory Diskettes’. The message the floppy disk recipients received if they inserted the disk was as follows:
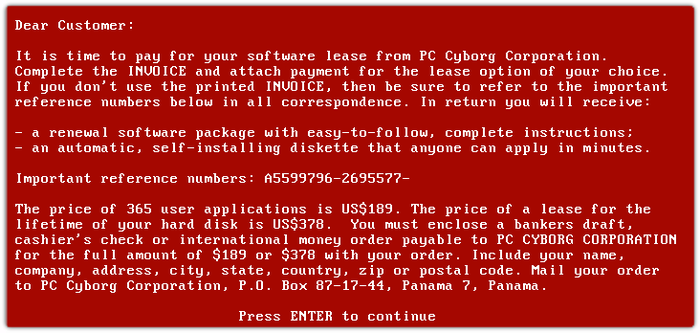
Besides the infected floppy disk, there was also an information sheet stating that a license to use the software had to be purchased. If the recipient inserted the floppy into a computer, the program counted the number of computer startups, and when it reached 90, hid the directories and encrypted or locked the file names on drive C. The affected users no longer had access to their data, and to regain access, they would have to send $189 to a fictitious PC Cyborg Corporation at a PO box in Panama:
Once the user paid, he would then receive another disk with a program that released his data. Dr Popp distributed about 20,000 floppy disks infecting about 1000 computers in 90 countries (about 5% of his disks were successful).
Joseph Popp was arrested in January 1990 at Schiphol Airport in Amsterdam. He allegedly had a plan to send another two million floppy disks containing ransomware. He was then extradited to Great Britain, but due to his unstable mental health, the trial was dropped against him, and he was released from prison.
In the same month, Jim Bates published his study in the Virus Bulletin and described the Aidsout program with which the files could be saved without paying.
The AIDS Trojan used symmetric encryption and encrypted file names on the hard drive, but this encryption did not affect the files; it just made them unusable. Because of the symmetric encryption technique, the virus could be easily removed by decryption; however, many victims wiped their hard drives and lost several years of work in the process. This type of ransomware attack was not particularly successful at collecting ransom since the victims were expected to mail a check to a P.O. box.
In the 90s, ransomware still relied only on symmetric encryptions, which were often weak enough to try to decrypt them. The limitations of attacks have also been recognised by criminals who perfected their assaults. In 1996, researchers began to take the science of cryptovirology more seriously.
In the first period, extortion viruses that did not encrypt the contents of the hard drive were common and locked the machine themselves. In this case, the virus that locked the device did not leave permanent damage after it was removed. However, even if the malware that encrypts the data is removed from the machine, the data will remain encrypted.
2.2. More advanced ransomware
For a long time after PC Cyborg, there was no major ransomware attack. The first viruses to encrypt computer data appeared later, around 2005, under the names PGPCoder or Archiveus in 2006.
Attackers began to create and embed a public key in the ransomware. Once the ransomware was on a device, it encrypted the files with a randomly generated key, which was also encrypted. RSA keys are difficult to crack because the RSA algorithm generates both keys.
The first attack to use RSA was the Archiveus ransomware attack that began in 2006. Once on the device, the malware would copy files, delete the original, lock the copies in an encrypted folder and then leave behind a file named ‘How to get your files back.txt.’ Though it was unsuccessful for a long time, Archiveus made it clear: reverse engineering encrypted files to find the key was a thing of the past.
In 2007, a new type of ransomware appeared that excluded people from their desktops instead of encrypting files. WinLock took over the victim’s screen, displayed pornographic images, and then demanded payment in a paid SMS to remove them.
2.3. Where is your encryption key?
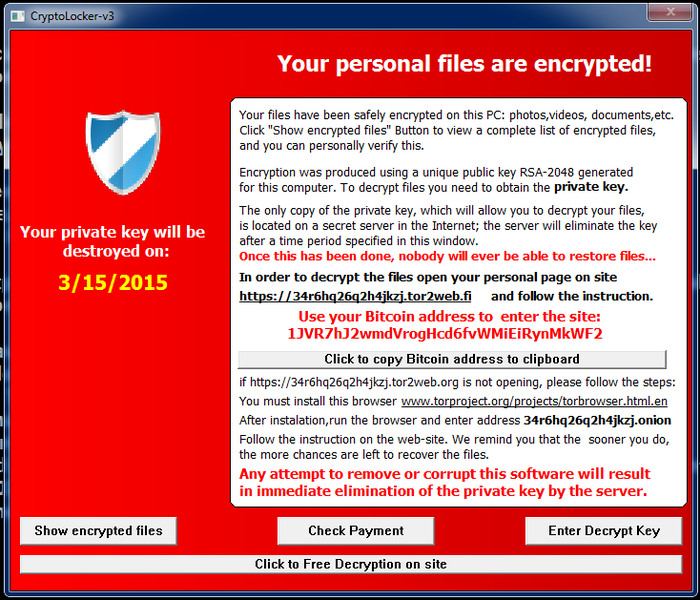
The current era of extortion viruses began in 2013 with the advent of the Cryptolocker family. New pests have in common that they encrypt the victim’s data and send the encryption key to the attacker. The data is returned to the victim when he or she pays in exchange for receiving the encryption key.
The other extortion viruses – Locky, WannaCry or Spora – differ in implementation, but the central idea remained the same. Today, an entire industry is built on extortion viruses, with some attackers maintaining an underlying website, customer service for a few people, and several payment options.
However, newer versions no longer (or not only) try to recover ransom with the ability to recover data: extortion viruses upload some data to an ‘own’ server before encryption, threatening that in case the ransom is not paid, the data is made public. This can be a ‘good tactic’ for fraudsters, especially for companies. This trick is also used by Sodinokibi (AKA, Sodin and REvil), one of the most harmful blackmail viruses ever made.
3. Types of Ransomware
‘Ransomware is not only about weaponising encryption; it’s more about bridging the fractures in the mind with a weaponised message that demands a response from the victim.’ - James Scott, Senior Fellow, Institute for Critical Infrastructure Technology
3.1. Scareware
Scareware may look scary, but it is basically harmless: it can be a rogue security software or a tech support scam. In the case of scareware, you see a pop-up message claiming that malware was discovered on your machine, and the only way to get rid of it is to pay a ransom. The danger is not real since legitimate cybersecurity software would never send you a message like this.
The opposite is also true: if you do not have this type of security software on your computer, it would never monitor you for ransomware infection. With scareware, your files are still safe, and you can still access them.
3.2. Screen lockers
The next level of attack is a screen locker. As its name applies, you are locked out of your computer entirely in case of a screen locker infection. You are ‘greeted’ with a full-size window that usually seems legitimate, contains an official logo. Next to the logo, the text informs you that your computer was scanned and detected that your IP address was being used to visit illegal websites. Of course, we also get information about what to do if we want to get our machine back, pay so much and so much in Bitcoin and then they unlock the screen.
Stay calm. Have you visited such websites? Have you committed any of the mentioned absurd charges? Certainly not. Do not pay the ransom.
3.3. Encrypting ransomware
The most detrimental form of ransomware is malicious encryption malware. Unlike the previous types of ransomware, here the statements are unfortunately factual: our files are encrypted and inaccessible to us unless we pay a ransom. In most cases, if you do not have a backup, your data will not be recoverable.
4. How Does Ransomware Spread?
‘Ransomware still uses social engineering as its main infection vector.’ - Stu Sjouwerman
There is nothing new under the sun: this malware is most typically distributed through spam e-mail attacks: 91% of cyberattacks begin with spear-phishing email.
The spam e-mail usually has an attachment disguised as a legitimate file or includes a URL link in the body of the e-mail. Cybercriminals use social engineering techniques to trick people into opening attachments or clicking on links that look legitimate.
As soon as the receiver of the e-mail downloads the attachment, the malicious code gets activated and starts to encrypt files on the device. If the attack vector is a link, and the user clicks on it, the victim is taken to a web page where the ransomware is delivered to the device without the user’s knowledge.
Once the encryption is finished, your computer is blocked. You receive a message telling you that your device has been encrypted and provides further information on how much you have to pay to receive a decryption key to recover your data.
Another way of infection is ‘malvertising’ or malicious advertising, using online advertising to distribute malware with little user interaction.
5. Protect and Prevent: How Can I Reduce the Risk of Ransomware?
‘Every new cyberattack is a reminder of why patching is important, as well as the risk of not applying security patches.’
1. Cybersecurity Hygiene: Educate People
‘Vaccinate’ your employees against a ransomware attack by educating the weakest link in your cyber defence system: the user. The majority of ransomware attacks require someone to activate the malicious code. Therefore, the most effective and cheapest way to fight against malware infections is to educate users about recognising and defending against cyberattacks. The infectious vectors are mails and social engineering techniques to trick the employee into downloading malware.
2. Patch, Patch, Patch… Patch and finally, Patch!
Always keep your devices up to date by using the latest patches: failing to implement a rigorous approach to patching known security vulnerabilities is like waving a red flag in the ocean of cyberworld and shouting, ‘Rob me!’ or putting a flyer on the main square of your town with the text ‘I will not be at home in the following two weeks, and my address is as follows…’
No one would you do that, right? Well, most of us still vividly remember the WannaCry ransomware attack, and none of us would like to ‘cry again.’ Still, even months after the EternalBlue vulnerability was exploited for the WannaCry and NotPetya ransomware attacks, an estimated 38 million PCs remained unpatched.
3. Back Up Your Data Frequently
Now, you reached the most important message of this article. If you do not remember anything but the following sentence, it was worth reading it: If you do not have a working backup, your data is most likely lost.
You can train yourself, use the fanciest devices with the newest and trendiest software installations: if you do not have a backup, no one on Earth would be able to restore your data. You are infinitely defenceless and can only ‘trust’ the benevolence of the person who caused you the trouble for the first place. Do you think that person will pity you and will restore your data, your family photos, the video about the first steps of your son or daughter…? Think again!
In the world of business, company formation contracts, trade secrets, patents, employment contracts, etc., can be mentioned because they cannot be replaced in the case of data loss – if you do not have a backup.
To prevent the above to happen, is not it easier to make a backup?
Ransomware can also encrypt backups stored on network servers. Companies should review their approach to backups: are employees backing up important files to a network drive? If so, how often? Are the backups from the employees’ devices and the file servers then backed up to a cloud backup service? Can the backup from the cloud be restored easily and quickly? Have you tested all the above scenarios? Do you have a risk management plan? Depending on the amount of data produced and the importance of data, you should apply an adequate method for backing up your data.
4. Use Multiple Layers of Defence
Have multiple layers of defence: make it harder for the bad guys to cause you harm, steal, encrypt or abuse your data. Utilising multiple security layers means that if one layer does not block an attack, you have additional layers that can mitigate the threat. So, what layers of security do you have in place? What are the tools you use to secure your Internet traffic? Do you store data in the cloud or on your local drive? What are the tools you use to keep your data intact?
6. Global Ransomware Landscape
‘Ransomware is expected to attack a business every 11 seconds by the end of 2021.’ – Steve Morgan, Editor-in-Chief, Cybercrime Magazine
- The annual cost of ransomware to organisations worldwide will hit with an estimated $20 billion in 2021
- Cybercrime damages will cost the world $6 trillion annually by 2021, up from $3 trillion in 2015.
- Global spending on cybersecurity will exceed $1 trillion cumulatively over the next five years.
- Ransomware has reached epidemic proportions and is the fastest-growing cybercrime.
The number of reported or discovered cases is just the ‘tip of the iceberg’. It is a big myth that ransomware damages equal the costs of ransom payouts. Firstly, it is vital to understand that even when the ransom is paid, there is no guarantee that the decryption key would ever be provided. Secondly, do not forget about the ‘accessory’ costs: damage and destruction (or loss!) of data, lost productivity and revenue during downtime, forensic investigation, restoration of available data and storage. The majority of companies do not count with reputational harm either, although it can be very significant.
Ten years ago, these attacks were more sporadic, rather opportunistic, and much less targeted and sophisticated. As of today, they have become highly targeted, extremely damaging, and corporate-level extensive massive attacks causing even weeks of downtime for whole corporations.
The attacks are not only becoming more severe, targeted, and more noxious, but also their frequency is dramatically and constantly growing:

Cyberattacks do not know borders or geographical boundaries, yet countries are still unwilling to share information or act together fighting against such threats. The different legal regulations among countries make it also hard to react or warn other countries or even investigate the same case when an affected company has offices in different countries.
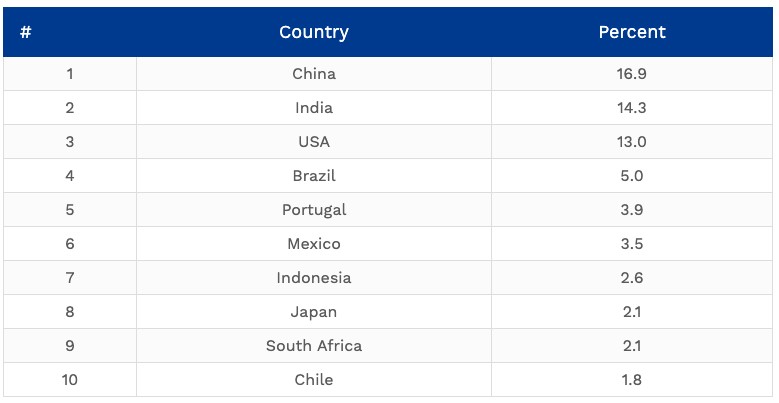
The table below shows the percentage distribution of ransomware attacks by country in 2020 as per Symantec:
Ransomware Statistics in 2020: From Random Barrages to Targeted Hits
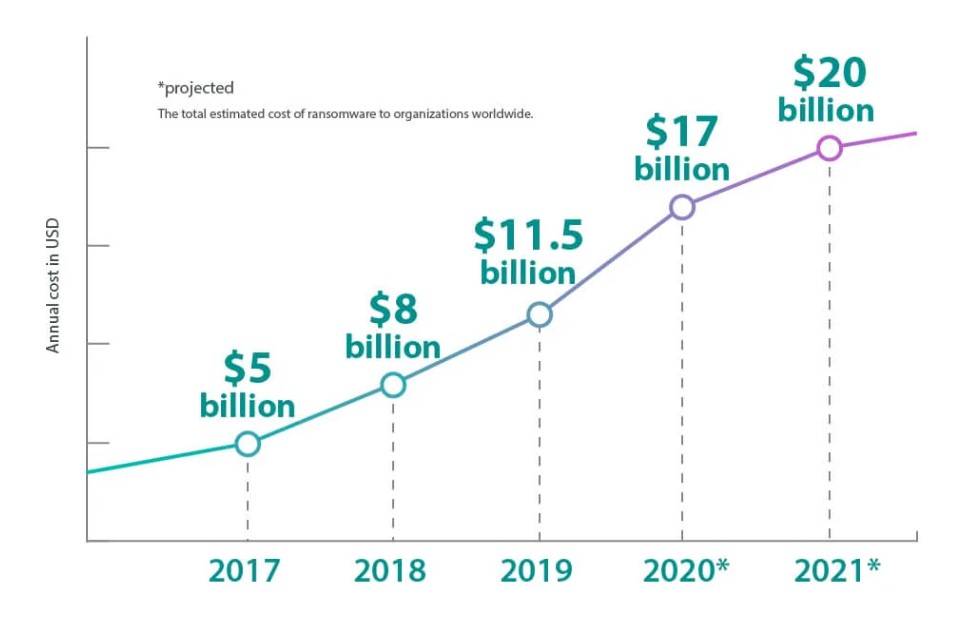
The annual cost of ransomware to organisations worldwide is rising steeply (and will hit with an estimated $20 billion in 2021):
Safety Detectives: Ransomware Facts, Trends & Statistics for 2020
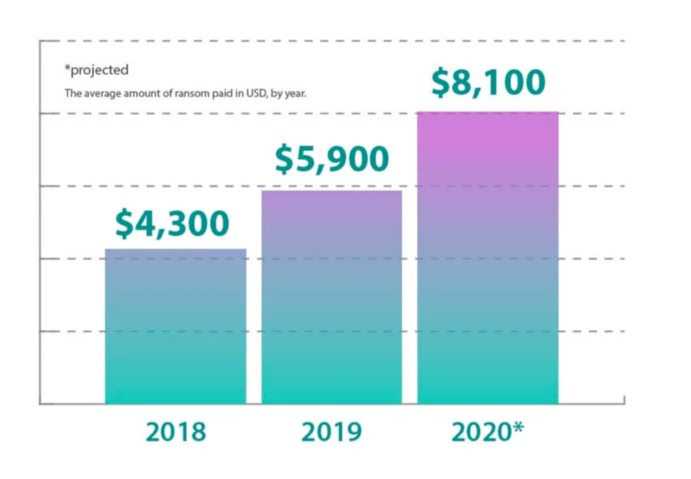
Not only the number of incidents is on the rise, but the average amount of ransom paid per incident as well:
Safety Detectives: Ransomware Facts, Trends & Statistics for 2020
For a detailed, international report, please read the ‘State of Ransomware 2020’ full report created by Sophos. It is an independent survey of 5000 IT managers across 26 countries.
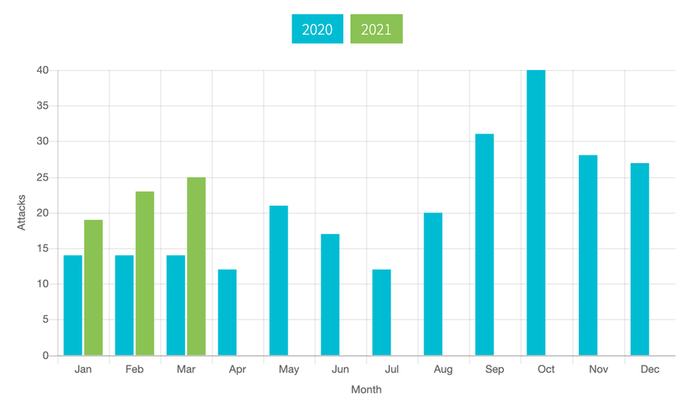
Blackfog tracks ransomware attacks released in 2021 and publishes each on a monthly basis. The trend can be read perfectly from the figure below. Compared to last year, the number of ransomware cases increased significantly every month:
It does not matter what source we are looking at; the forecasts and statistics are very depressing.
Without claiming completeness, some thought-provoking findings quoted from the Cybercrime Magazine:
- Cybersecurity Ventures predicts cybercrime damages will cost the world $6 trillion annually by 2021, up from $3 trillion in 2015.
- Cybercrime represents the greatest transfer of economic wealth in history, risks the incentives for innovation and investment, and will be more profitable than the global trade of all major illegal drugs combined.
- Cybercriminal activity is one of the biggest challenges that humanity will face in the next two decades.
- The Yahoo hack was recently recalculated to have affected 3 billion user accounts, and the Equifax breach in 2017 – with 145.5 million customers affected – exceeds the largest publicly disclosed hacks ever reported.
- The World Wide Web was invented in 1989. The first-ever website went live in 1991. Today there are more than 1.2 billion websites.
- There are 111 billion lines of new software code being produced each year, which introduces many vulnerabilities that can be exploited.
- Some estimates put the size of the Deep Web (which is not indexed or accessible by search engines) at as much as 5,000 times larger than the surface web.
- Global spending on cybersecurity will exceed $1 trillion cumulatively over the next five years.
- The U.S. Department of Justice (DOJ) recently described ransomware as a new business model for cybercrime and a global phenomenon.
- Ransomware has reached epidemic proportions and is the fastest-growing cybercrime.
- Cybersecurity Ventures predicts there will 3.5 million unfilled cybersecurity jobs by 2021, up from 1 million openings in 2014.
7. The Biggest Ransomware Attack in the History
‘Being too busy to worry about backup is like being too busy driving a car to put on the seatbelt.’ – T. E. Ronneberg
7.1. It is so quick; it must be a worm!
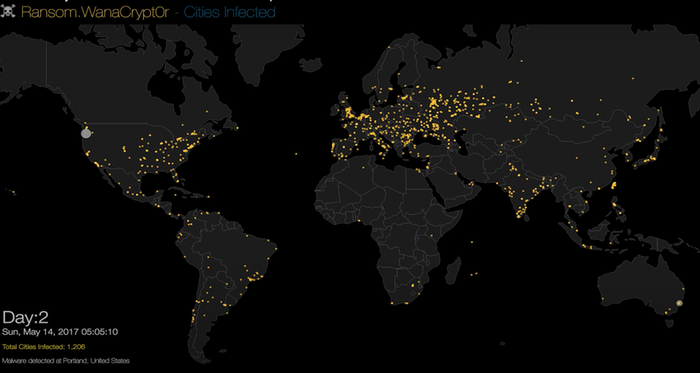
On 12 May 2017, an extortion virus (cryptoworm) called WannaCryptor (aka WannaCry or WCrypt) appeared in all parts of the world and wreaked havoc computer systems to an unprecedented extent.
Its initial point of injection believed to be in North Korea, and it quickly spread to over 230,000 computers in 150 countries within the day. On the first day of the attack, WannaCry appeared in 74 countries. Most of the attacks took place in Russia, but Ukraine, India and Taiwan also suffered significant damage from WannaCry.
The lightning-fast spread of the worm is best illustrated by a video made by Malwarebyte showing the WannaCry Ransomware Infection Heat Map:
WannaCry used both AES and RSA keys, and it was a worm, meaning it could spread exponentially and infect the entire network of an infected device. The attack primarily affected computers in organisations that did not have the April 2017 security update for Microsoft. Users who no longer have Microsoft Windows systems running on their computers, such as Windows XP or Microsoft Server 2003, were at particular risk of vulnerability, as no official update has been released to their systems since 2014.
One of the first companies attacked in Europe was the Spanish mobile company Telefónica. Within hours, thousands of NHS hospitals and surgeries across the UK were affected too. The damage to the NHS is estimated at £92 million after 19,000 appointments were cancelled due to the attack. The WannaCry ransomware attack hit around 230,000 computers across 150 countries and caused $4 billion in losses worldwide.
7.2. How could it happen?
The whole WannaCryptor crisis was fuelled by a vulnerability called EternalBlue. The cybercriminals took advantage of a weakness in the Microsoft Windows operating system using a hack (EternalBlue) that was allegedly developed by the United States National Security Agency.
Microsoft released a security patch that protected user’s systems against this exploit almost two months before the WannaCry ransomware attack began. But many individuals and organisations did not update their operating systems and so were left exposed to the attack: the vulnerability exploited by EternalBlue left them open to attack.
In retrospect, we can safely say that the outbreak could have been avoided if users worldwide had taken the necessary steps and run the fixes on time.
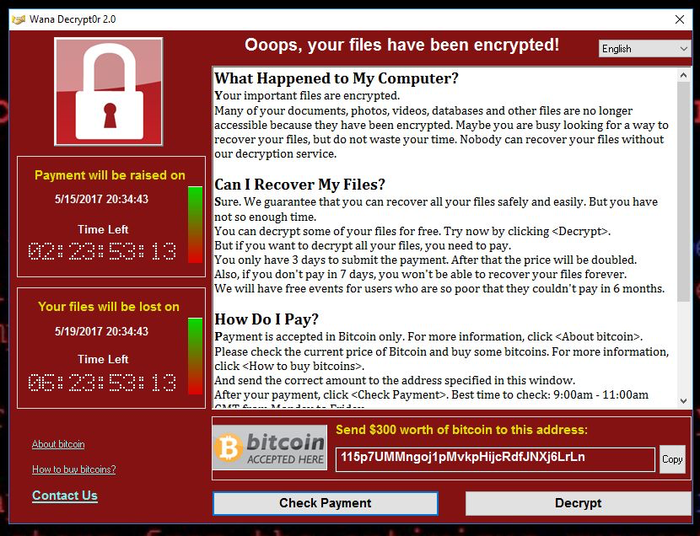
7.3. How WannaCry appears on screen?
In the case of WannaCry, two countdown clocks were visible on the screen of the infected machines. The ransom amount started at $300, and when the other counter reached zero, the virus destroyed files on the challenged device. For the average private user, this was a more significant blow since the scope of regular backups and the order to run bug fixes immediately was better regulated in a corporate environment.
The attackers did not keep their promises to decrypt the encrypted files, even though many of the victims paid the ransom. Actually, they did not even have a technical solution to determine who paid or who did not, so they could not give the blackmail users the codes needed to decrypt it, so they were falsely promising and lying here.
7.4. Why was WannaCry short-lived?
The solution was a then 23-year-old hacker, Marcus Hutchins. As a teenager, he was already very receptive to computers and used his knowledge many times to install and play game programs bypassing the school computer system. He was also an active member of an online forum that facilitated malware development to show off his genius.
How did he figure out in hours how to curb the largest-scale cyber-attack of all time, how he became a celebrated hero, and why the FBI arrested him? The incredible story is told in the video below:
This story highlights that there is often only a hair’s breadth between good and evil. It also proves that it is not the machines themselves, the malicious codes, the danger, but the person who creates them and uses them for the wrong purpose.
7.5. Has anything changed since then?
Four years have passed, but enhanced versions of WannaCryptor have since become leading players in a ransomware area. Attacks using the infamous exploit have not entirely ceased; EternalBlue remains a relevant threat, as we are talking about hundreds of thousands of attempted attacks on unprotected systems every day.
Despite being short-lived, WannaCry created extensive financial damages and set the precedent of using cryptocurrency for ransom payments. The use of bitcoin, or other cryptocurrencies, makes tracing the origin of ransomware even more complicated and also protects attackers.
8. What is the Situation in Luxembourg?
‘Hardware is easy to protect: lock it in a room, chain it to a desk, or buy a spare. Information poses more of a problem. It can exist in more than one place; be transported halfway across the planet in seconds, and be stolen without your knowledge.’ – Bruce Schneier
The situation is none better in Luxembourg, and we need to stay vigilant and take all the precautions not to become a victim. Though we do not have aggregated statistics, let me include a couple of examples to demonstrate how serious the situation is.
8.1. A wave of crypto ransomware in 2015
In 2015, the Computer Incident Response Center Luxembourg (CIRCL) reported a wave of crypto-ransomware attacks targeting Luxembourg. It also released a technical document to warn and give proactive and incident response tips for Crypto-ransomware attacks.
Ever since such attacks are with us, and in the last six years, about 200 cases have been reported to CIRCL. The highest reported ransom demand was €1,500,000. Regarding the question as to ‘How well prepared are Luxembourg organisations for ransomware attacks?’, CIRCL reported that ‘Many private people don’t have backups at all or no offline-backups. They would lose everything accessible on their computer in case of a successful attack. In professional environments, we have seen good and bad preparedness, regardless of the size of the company/structure. It should be advised to review regularly the state of the backup system, configuration, and strategy as well as perform a regular test.’
8.2. Ransomware is the big winner of 2020
On 17 January 2020, a large Luxembourgish construction firm was hit by a major ransomware attack. The hackers encrypted the company’s files and asked for €450,000 as ransom. The company was paralysed since about 150 employees could not work for some time and were forced to stay home. The company had a backup, yet it had to replace all its IT devices with the cost of €300,000, which took 6 weeks.
In May 2020, three Cactus stores (Windhof, Bonnevoie and Merl) were forced to close for several days due to a ransomware attack.
Because of the Covid-19 lock-down measures, many people are working from home, creating a much more vulnerable environment and becoming a victim of a cyberattack.
‘… there has been a significant increase in cyberattacks in the wake of Covid-19, as hackers seek to exploit coronavirus-related panic, along with vulnerabilities created by an increase in remote working.’
As the NTT report (NTT Luxembourg PSF) narrated: ‘Hospitals, in particular, have experienced a wave of threats, at the exact time that their resources are focused on saving lives and handling an overflow of patients. Ransomware, encrypting applications and files until a ransom is paid, has been the main threat, along with attempts to steal financial information and patient medical records.’
However, it is worth noting that, as Alexandre Dulaunoy mentioned to Wort:
‘…until now, the technique has mainly consisted of encrypting data and making it inaccessible before demanding a ransom, attackers are now opting for a strategy intended to put pressure on the targets by leaking part of the recovered data.’
8.3. We will not get away with 2021 without ransomware…
CIRCL has recently reported that ‘Several critical vulnerabilities in Microsoft Exchange have been discovered.’ Why is that important? Because cybercriminals are using new zero-day ProxyLogon vulnerability to install the DearCry ransomware. Therefore, all Exchange Servers should be updated. On servers where the infection has already occurred, patching will not help. CIRCL has already found exploited servers in Luxembourg. Due to the severity of the attacks, Microsoft recommends that administrators ‘install these updates immediately’ to protect Exchange servers from these attacks.
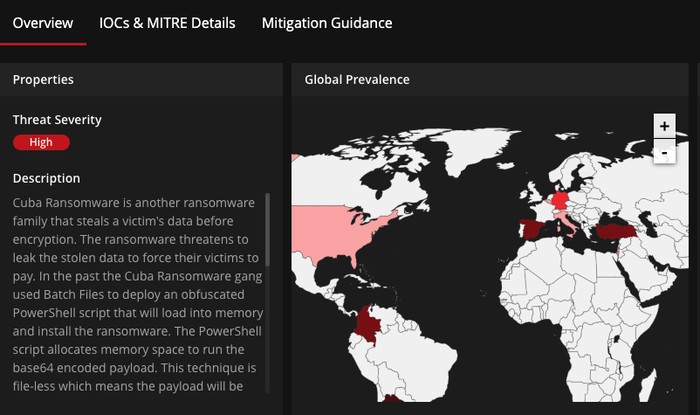
Another high threat severity ransomware is the so-called Cuba ransomware. From McAfee’s threat center, you may read further information on it and even check the global prevalence preview of the Cuba ransomware heatmap:
9. Detect and React to Ransomware
‘The general advice is not to pay the ransom. By sending your money to cybercriminals you’ll only confirm that ransomware works, and there’s no guarantee you’ll get the decryption key you need in return.’ – Anonymous – No More Ransom
9.1. CIRCL
CIRCL (Computer Incident Response Center Luxembourg) is one of the departments of SECURITYMADEIN.LU, and also the member of CERT.LU.
Once the trouble has occurred, the most important thing is to notice it as soon as possible and respond appropriately. This is when CIRCL, the CERT for the private sector, communes and non-governmental entities in Luxembourg, comes into the picture as firefighters fighting in the front line.
CIRCL uses some state-of-the-art free tools like URL Abuse and LookyLoo to detect threats. Lookyloo is a web forensic tool that captures a webpage then displays a tree of the domains that call each other. By using Lookyloo, you can understand the threats you are exposed to when you visit a particular website, and you can check whether there are links to suspicious, phishing or other malicious sites.
Such tools can be used against – for example – phishing and ransomware in such a way that these attacks can be detected with these tools, and countermeasures can be taken against them as soon as possible.
CIRCL also provides a leak monitoring service based on its open-source tool called the AIL framework. The AIL framework has been extended recently with Yara Rules to support its functionalities to mine sensitive, suspicious or malicious information. These devices function as an extra layer of security to gain some time to fight against cyberattacks.
In addition to detection, another vital pillar of CIRCL’s tasks is the extensive exchange of up-to-date information on possible or actual cyber-attacks. Therefore, CIRCL is also the hub and hosting organisation for various information-sharing community operating with MISP.
Information sharing on cybersecurity threats has become highly critical, and reinforcing the need for more cooperation across borders, individuals, and organisations is vital in adequate protection against cyberattacks.
MISP was developed to improve automated detection and responsiveness to target and cybersecurity attacks in Luxembourg and outside. It is a platform where members from public and private sectors can exchange indicators of compromise to detect, prevent or respond to a security incident. More than 6000 organisations are using MISP worldwide in the framework called MISP Project.
9.2. Detected Ransomware in Luxembourg
CIRCL reported that the most severe (with a significant impact on business continuity) incidents in Luxembourg for 2020 were the ransomware cases.
The origin of such ransomware cases is often unprotected VPN or other devices that are in the organisation’s external perimeters. Adequate monitoring of such devices, including a patching management strategy, is critical to limit many opportunistic attacks such as ransomware.
Many VPN products were targeted in 2020 by different threat actors. During the lock-down phases, a significant number of outdated and unpatched systems were connected to the Internet. For example, the Pulse Secure VPN (CVE-2019-11510) was still actively exposed worldwide, and major users of Pulse VPN did not patch their devices. Threat actors, such as the REvil (Sodinokibi) ransomware, were actively abusing the vulnerability to compromise infrastructures further.
Another critical factor regarding ransomware is the availability of an incident response procedure within the organisation. Since recent ransomware attacks no longer threaten to make data inaccessible or destroy them, rather disclose specific data, it is imperative to develop a proper PR strategy for a company in advance in the event of ransomware extortion.
Some cases in Luxembourg were discovered by active monitoring, and the victims took complementary actions to be better prepared in case of the leaks. Threat actors actively move their business model towards a mixed-model, where encryption of information and leaks are performed together.
9.3. No More Ransom
‘The general advice is not to pay the ransom. By sending your money to cybercriminals you’ll only confirm that ransomware works, and there’s no guarantee you’ll get the decryption key you need in return.’ – Anonymous – No More Ransom
Great efforts have been made to control the situation and reduce damage regarding ransomware. The No More Ransom website was launched in July 2016 by the Dutch National Police, Europol, Intel Security and Kaspersky Lab. Since then, nearly 1.6 million people from more than 180 countries have accessed the website to find a solution for their ransomware-related problems.
This website is valuable and unique in many ways. On the one hand, it contains a great deal of beneficial information about ransomware, prevention options, decoding tools, and you can also report yourself as a victim of an extortion virus.
The goal of the site is to help victims of ransomware retrieve their encrypted data without having to pay the criminals. There are now 52 free decryption tools on this portal, which can decrypt 84 ransomware families. More than 35,000 people have managed to retrieve their files for free, which has prevented criminals from profiting from more than EUR 10 million.
Both the private sector and law enforcement agencies are stepping up their efforts to fight these cybercriminals, who use ransomware to deprive their victims of large sums of money. However, awareness remains key to preventing ransomware from succeeding. Since it is much easier to avoid a threat than to fight it when the system is affected, the project aims to familiarise users with how ransomware works and what countermeasures can be taken to prevent infection effectively.
There are 30 active ransomware groups worldwide, often working together, which can sometimes lack operational security, allowing organisations like CIRCL to apprehend attacks better.
10. How can SECURITYMADEIN.LU help?
‘My message for companies that think they haven’t been attacked is: You’re not looking hard enough.’ – James Snook
URLabuse: CIRCL developed this free tool to check the maliciousness of links.
Lookyloo: is a tool also developed by CIRCL that gives you a quick overview of a website by scraping it and displaying a tree of domains calling each other.
MISP: another free tool from CIRCL. It is a platform for sharing threat indicators, threat intelligence within private and public sectors.
No More Ransom website contains a great deal of beneficial information about ransomware, prevention options and decoding tools.
Back10.1. CERT.LU
CERT.LU (Cyber Emergency Response Community Luxembourg) is a community that brings together key cybersecurity actors and their expertise to provide a rapid and targeted response to a possible cyberattack and minimise damage and accelerate recovery.
10.2. CASES
CASES (Cybersecurity Awareness and Security Enhancement Services) is also part of SECURITYMADEIN.LU. It has multiple services available to the public to raise awareness: Fit4Cybersecurity, CASES Diagnostic, MONARC, TACOS, etc. Besides the above tools, the CASES website contains a large number of valuable articles on cybersecurity.
10.3. C3
The flagship product of C3 (Cybersecurity Competence Center) is Room#42. It is an innovative and unique concept in Europe, through which ‘participants’ are in a cyberattack and have to react to it. During such a cyberattack simulation game, participants can try out how they would respond to cyberattacks.
10.4. Cybersecurity Breakfast
During the 41st edition of the monthly Cybersecurity Breakfast organised by SECURITYMADEIN.LU, Security Researcher at CIRCL, Alexandre Dulaunoy, talked about the more common ‘Data Breaches: The dirty business behind the scenes. When your leak becomes the product.’
Should I pay or not?
Always avoid paying a ransom as there is no guarantee that your data will be returned. Every payment will enforce the business model of the criminals, making future attacks more likely.
11. Conclusion
‘The knock-on effect of a data breach can be devastating for a company. When customers start taking their business – and their money – elsewhere, that can be a real body blow.’ – Christopher Graham
Since 1989, ransomware has become the number one security risk to businesses and users. The trend is that companies and individual users face more and more ransomware attacks. Still, with the development of smart devices, security risks will also be present in intimate areas of our privacy.
Due to the arrival of the pandemic, companies switched to telecommuting en masse overnight. As a result, the world has begun to rely more on technological solutions than ever before. Teleworking has brought many benefits to employees, but at the same time has made companies’ networks more vulnerable to attacks and caused many sleepless nights for cybersecurity professionals in companies.
Cyberattacks pose a constant threat to organisations, so businesses need to build specialised security teams and systems to avoid or reduce the financial and reputational consequences of such attacks effectively.
Data leakage and extortion are not new techniques, but they are on the rise. Failed attacks or careful backup and recovery processes are no longer always sufficient to prevent such cyberattacks.
The essence of ransomware is to ‘host’ organisations’ files and return them only for a ransom - although there is no guarantee of that. However, if we have backups on a system that was not accessed by the virus, we have a case to win because we do not need the help of cybercriminals to get our files back. The ransom is usually a heavy item in itself, and the outage caused by the virus imposes additional severe sums for the company.
Ransomware attacks are evolving rapidly, and it is expected that in 2021, these methods will be used even more frequently in increasingly complex and powerful attacks. There is a growing practice among criminals to sell malware to other attackers who try to extort payments from targeted businesses through blackmail.
Ransomware attacks often exploit known software vulnerabilities. As soon as such vulnerabilities are discovered, software vendors will immediately prepare and make available fixes for them. However, companies may not install them immediately in all cases because IT professionals are overwhelmed, and updates would have to be installed on too many devices at once, so the process would take too long to shut down IT systems.
Smart devices connected to the Internet usually present huge data protection and security challenges. Their use poses serious cyberattack risks to obtaining and blackmailing intimate data are just a few of the many examples.
We need to develop tools and technologies that prevent a ransomware attack from compromising our computer systems and improve our early detection and rapid response capabilities.
Creating cybersecurity is teamwork: from raising awareness to sharing information and tips on the latest vulnerabilities. During a post-disaster recovery, you also need to think about collaboration for recovery and mitigation.
While prevention is the best defence against cyberattacks in general, we need to remain vigilant and persistent, as tomorrow can always hold surprises.
‘The weakest link in the security chain is the human element.’ – Kevin Mitnick