- 01 Jul, 2021
- Topic of the Month

1. Introduction & Definition
“Social Engineering uses influence and persuasion to deceive people by convincing them that the social engineer is someone he is not, or by manipulation. As a result, the social engineer is able to take advantage of people to obtain information with or without the use of technology.” - Kevin D. Mitnick – The Art of Deception
1.1. What is social engineering?
Nowadays, due to the development of information and communication technologies, the methods of carrying out cyberattacks are constantly changing and evolving. One type of attack to obtain various inside and confidential information is social engineering, which builds on the influence, manipulation, and exploitable properties of the human factor.
In a broader sense, social engineering is a con or scan technique, basically the art of gaining access to buildings, systems or data by exploiting human psychology, rather than breaking in or using technical hacking techniques. Yes, social engineering is the art of manipulating people to give up confidential information. Thus, social engineers are “people hackers”. If you have ever seen spy movies like the legendary James Bond series or Ethan Hunt in Mission Impossible, you have already seen many examples.
From a cybersecurity standpoint, social engineering is a form of attack based on the exploitable properties of the human factor, human credulity, a set of techniques and methods that allow the acquisition of confidential information based on influencing and manipulating people.
- 98% of cyber attacks rely on social engineering
- New employees are the most susceptible to socially engineered attacks
- 21% of current or former employees use social engineering to gain a financial advantage
- The number one type of social engineering attack is phishing
- 30% of phishing messages get opened by targeted users
- 45% of employees click emails they consider to be suspicious “just in case it’s important”
- 50% of phishing sites now using HTTPS
- 66% of malware is installed via malicious email attachments
- Over 18 million websites are infected with malware at a given time each week
- 43% of cyber attacks target small business
- 67% of financial institutions reported an increase in cyber attacks over the past year
- 70 – 90 % of breaches are caused by social engineering
Source: PurpleSec
Source: Security Boulevard
Back“The aim of the attack is to make a person do something that they would not normally do; the attacker’s motivation is to obtain information that they cannot normally access. In an increasingly digitalised world, this very often (but not always) comes down to obtaining authentication information.” – CASES: Social Engineering.
In social engineering attacks, the question may arise, why do attackers target the human factor instead of exploiting technological vulnerabilities to gain access to confidential information?
The human factor can be considered a favourable target. Its use extends to various hardware and software devices; it has access to multiple databases, systems or, for example, customer data. In addition, employees relate to each other, share information with each other, and have a variety of inside and confidential information that can be considered valuable to attackers.
It is worth distinguishing between inside and confidential information, as inside information may not always be confidential. People can be considered an ideal target because of their exploitable properties. These are qualities found in everyone, but not on the same level, but characteristic of the human factor. Examples of such attributes are helpfulness, naivety, curiosity, openness, influence, interest, fatigue or overload. There are also predictable characteristics that are significantly related to the victim’s workplace, depending on their development.
Dissatisfaction, bribery or, extortion can also be considered as such a trait because if the employee is not satisfied with his job (possibly his work environment, his esteem or his salary, for example), then the attacker can either pay or influence the victim to release confidential and insider information.
There are cases where an attacker exploits the user’s unprofessionalism, use of passwords, lack of security awareness, or negligence, or the resulting omissions. For these reasons, a significant part of social engineer attacks can only be successful if users are not security conscious and do not know the appropriate security procedures, requirements, and techniques.
Social engineering attacks build on exploitable human qualities such as naivety and also affectability.
2. The human factor as the weakest chain of security
“The chain is only as strong as its weakest link, for if that fails, the chain fails and the object that it has been holding up falls to the ground.” - Thomas Reid, Essays on The Intellectual Powers of Man
The human factor can be considered a security risk in several respects. The ignorance and unskilledness of users and the resulting human omissions have a worrying effect on IT security. Still, we must not forget the usefulness of human help, influence and naivety. It is also important to mention that most security incidents are committed by the company’s internal staff, or at least the support and involvement of internal employees are necessary to carry out a successful attack.
But why is the human factor the most favourable target? Because employees have direct access to most of the values to be protected: employees manage hardware devices, run the software, and work with data collected by the organisation — and most importantly, they have exploitable human qualities (such as curiosity, helpfulness, credulity). This allows the user, as the weakest link in the security chain, to become an attractive target in the eyes of an attacker, and the easiest way is for the attacker to try to circumvent security systems to gain access to or harm confidential or inside information.
2.1. Ignorance, incompetence
The biggest problem is the ignorance and inadequate training of the users, as most human omissions can be traced back to some incomplete knowledge. As a result, hardware may be left unattended, malware may be installed, confidential information may be leaked, data storage may be lost, and so on.
However, not only the lack of information security knowledge is the problem. For example, many people do not read an error message without reading it or enter their password without thinking, not even assuming that the dialog box that may appear may not even draw attention to a real anomaly.
2.2. Inattention / inattentiveness
Attempts based on the exploitation of inattention usually target employees who do monotonous work and perform their tasks on a routine basis - typically receptionists, customer service and help desk staff.
Calendar entries, contracts, invoices, organisation charts, business cards, etc., on the employees’ desk can help a social engineer for identity theft or prepare for a personalisation attack.
2.3. Human negligence, carelessness
Even if they are aware of specific security rules, users often neglect the regulations that should otherwise be followed, such as not using easy-to-guess passwords or leaving their computer unlocked. However, it is a much bigger problem to draw up and, above all, comply with the safety regulations for portable devices.
If we store confidential data on the hard drive of a laptop, it is imperative to encrypt it properly, to secure the login to the machine, to use appropriate passwords, or it is advisable to choose a model that also has a fingerprint reader.
Particular care should also be taken when disposing of IT equipment. For example, when disposed of, all confidential information must be appropriately destroyed on the hard drive, as certain procedures can be used to recover data even from erased or formatted disks, which can pose a serious privacy risk.
2.4. Loyalty, naivety
The attribute of credulity is also very closely related to helpfulness. Staff help an attacker because they naively believe they are really in trouble. Still, with a calm heart, they provide confidential information to unauthorised people who may only know the jargon used in the area.
2.5. Helpfulness
Helpfulness is one of the most basic human qualities that social engineers can take advantage of in countless ways.
2.6. Influenceability
It is also characteristic of most people that they are quite easy to influence. There can be several means of doing this, including persuasion, bribery, or even intimidation. For example, an employee who works in an awkward work atmosphere or is dissatisfied with his or her salary can be bribed more easily. If the attacker wants to use intimidation to force the victim to cooperate, it is often enough to refer to their supervisor or a relationship with some other senior executive.
3. Human-based social engineering techniques
“The key to social engineering is influencing a person to do something that allows the hacker to gain access to information or your network.” - Kevin Mitnick
Social engineering attacks can be divided into two groups. We distinguish between human-based and IT-based, that is, attacks performed using IT tools and those type of attacks which do not use computers. At the heart of both types of attacks is the influence of the human factor, whether or not the prospective victim uses some means of info-communication.
Human-based social engineering techniques include methods that do not require the usage of a computer to deceive or influence the victim. This type of trick is challenging to defend against because while computer-based attacks have security solutions (anti-virus, anti-spam, etc.) that can prevent the user from being deceived and the attack attempt failing, in that case, it is up to the victim alone to fall for the scam or to recognise the trick applied by the social engineer.
The execution of human-based attacks does not require IT expertise, it can be carried out by anyone, but it requires prior observation and preparation. The attacker in human-based attacks have a more difficult task, as these attacks in most cases have to be carried out face-to-face, and the risk of falling due to personal contact is also higher.
Human-based social engineering is usually built on the personification of someone. Depending on the situation, the person to be personalised can be a customer, an employee, an external agent (e.g., a mechanic, a maintenance worker, etc.) or even a cleaning lady:
It is especially difficult to defend against these attacks, as the attacker exploits human qualities such as compassion and guilt or even intimidation.
The social engineer can take advantage of human credulity when a company has multiple locations (e.g., chain stores, local branches, bank branches, etc.). An example of impersonation is when an employee working at one site — who is, of course, in contact with employees at the other site — is away from work for leave or other reasons, so someone else is performing their duties. At this point, the attacker, with the right information, can easily take on the role of “deputy,” as they will most likely not know or verify that the deputy is indeed an employee of that department or just an impersonator.
Deceptive attacks can target new employees, as they can be easy prey for a social engineer: newbies are not so aware of things at work at the beginning of their job, they do not know their colleagues so much.
The most typical human-based attack methods are as follows:
3.1. Asking for help - pretexting
One of the most common social engineering techniques is asking for help, during which the attacker does not need serious preparation. It is simply enough to ask the target person for the desired information or ask for help.
In many cases, attackers target helpdesk, customer service, or reception workers, hoping that they are the people who see the same type of tasks on a day-to-day basis, so they are the ones who have a more challenging time filtering out suspicious inquiries and may not notice that they are facing an attack in addition to their daily routine work.
An attack can also happen by attacking someone in the skin of a new co-worker, for example, affecting the target person’s helpfulness, as people are usually more willing to help when a needy person needs help, so when a new co-worker asks for help, the victim can easily imagine the situation, as he was once a beginner.
This method does not require serious preparation; however, the attacker must master the technical terms used in the given organisation to build trust in the victim. The attacker can build trust by knowing the jargon or having certain information within the company that he shares and thus presents himself as an insider.
Perhaps the most common case is when the attacker is extradited to a co-worker himself, knowing the details of the victim and calls the colleague for help. He urges a ‘colleague’ as there is some urgent futures job that can only be delivered if the colleague helps the attacker. The urgency-based technique can also be seen, for example, in the case of phishing mail, where the victim is put under time pressure and asked to share his or her password or other valuable information.
3.2. Providing help – reverse social engineering
The reverse of the previous cases can also happen when the social engineer asks the target person for help but somehow manages to get the targeted victim to ask for his or her assistance. One possible way of doing this is for the attacker to generate some kind of bug. Then, by anticipating the responsible parties, the solution appears to be the role of the solution specialist.
Assistance can be provided in person or by telephone, or the attacker may join the target person in the form of remote assistance.
3.3. Calling over a telephone
The target person can be deceived in several ways, the most common being by telephone, apparently because it poses the least risk to the attacker, and the risk of exposure on this line is the least threatening.
In the video below, you can watch two scary examples of hacking. The first one is a vishing scam (phishing over the phone) that happened at the DEFCON conference.
The second example is even more frightening and thought-provoking when the hacker says that “If my evilness had worked correctly, …I could have made you homeless and penniless…”
Whichever case we look at, both are very instructive…
3.4. Pretending to be a new employee
Another typical case is when the attacker impersonates a new employee who still needs the support of co-workers. The new colleague may forget his/her password but need to do an urgent task on his/her computer. It is important to note that the goal may be to obtain a password or access and, for example, some corporate knowledge (what can be accessed on the network) that could serve as a basis for a subsequent attack.
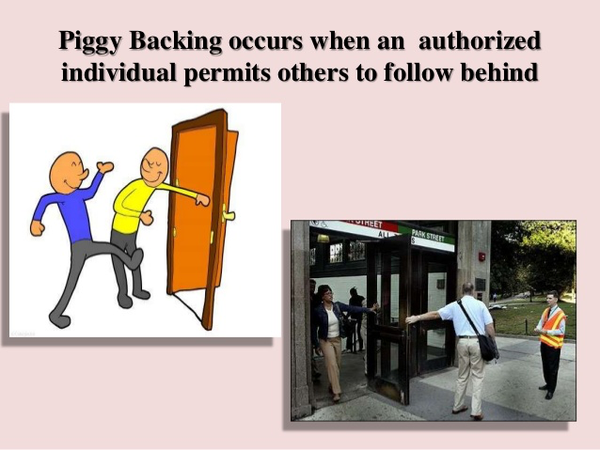
3.5. Piggy packing – The usage of someone else’s privileges
This is the method when the attackers use someone else’s privileges to achieve their goal, for example, pretending to be a co-worker (or at least someone with access), pretending to have forgotten their access card or key at home, and asking someone to let them in.
This method can also be used to gain access to the building. In this case, the attacker tries to persuade the target to let him into the building with his authority, such as pulling down his access card twice. This can usually happen by the attacker pretending to be a new employee or playing by leaving his or her access card at home.
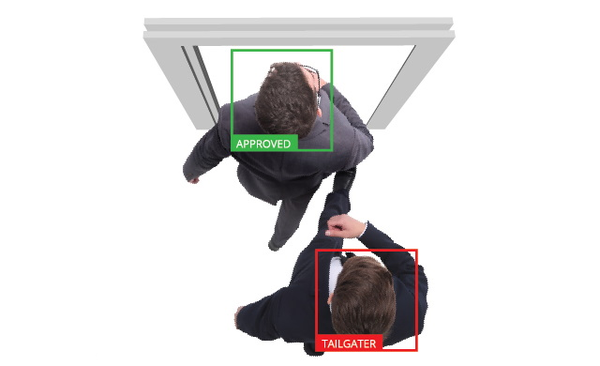
3.6. Tailgating - joining a guest group
In this method, the attacker pretends to be a member of a group of guests or workers, then simply sneaks into the building and is free to walk around looking for information.
The attacker examines in advance the order of arrival of guests, whether they receive an entrance card, how they enter the guests, whether they enter them at all, or just open the entrance gates for them.
During the preparations, the attacker must assess which group to join, as he will have to bring various equipment with him to get in. For example, the attacker can join a cleaning brigade or construction workers; the list and options are endless. The primary aim of the attacker is discreet access to the building.
Access can be done by using a fake access card, which, like the previous one, also requires serious preparation. If there is an access system in the given organisation, only the cards can be forged using a special technique. In the absence of an access control system, the attacker would have to inspect or copy the card in advance, hoping that the security guard would not even look closely at the access cards of all employees in the organisation.
It is important to note that when an attacker enters an organisation’s building, it may not only gain access to confidential and inside information but may, for example, damage devices, delete or destroy data files, and compromise inside and confidential information.
The latter is considered dangerous because, for example, it is we store a lot of personal information on our desk, be it a photo of our family, a private entry in our calendar about our activities, a document containing confidential information or even a recorded password. That is why it is vital to keep documents containing valuable confidential information in a secure place.
3.7. Shoulder surfing
Another human-based method is shoulder surfing. In this case, an attacker obtains, for example, the target person’s ID, password, or a PIN when the victim is withdrawing money by simply looking over his shoulder while the victim types it. The advantage of the technique is that the attacker does not have to get into the victim’s trust, yet he has to get close enough physically to the victim to be able to spot the typing of the ID or password easily.
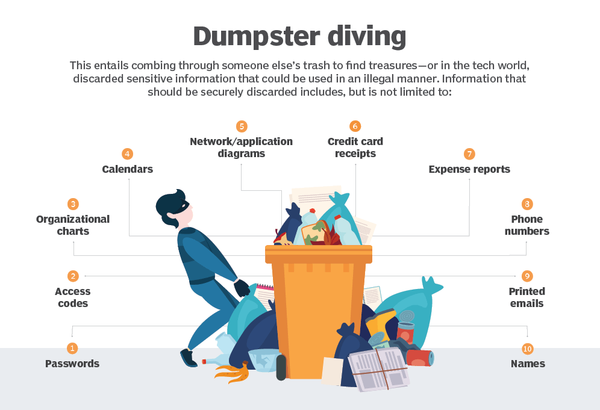
3.8. Dumpster diving
Another human-based social engineering technique is “dumpster diving”, in which the attacker enters the building using one of the techniques described earlier and then scans our trash. Trash can contain a lot of valuable information, such as personal information, printed work correspondence, a password slip, or a number of internal and confidential notes. By using this technique, the social engineer can gain such information that can help the attacker blackmail or impersonate the owner of the trash.
It is important to mention the management of the belongings of dismissed/leaving staff. The use of a shredder is always recommended, as you never know what seemingly insignificant information an attacker may be exploited.
3.9. Social media
Nowadays social media has become the primary tool of social engineer attacks, making it much easier to carry out the attacks. This is because it has an information-gathering role. The attacker can learn many valuable things about the target person, their contact and personal information, interests, and often where the prospective victim is, with whom, and what they are doing.

This is why it is important to increase security awareness among users, including the proper application of the privacy settings of various social networking sites in order to reduce the amount of information that attackers may obtain significantly.
3.10. Invention of passwords
The invention of passwords can also be classified as a group of human-based methods. In this case, the attacker can guess the passwords due to the inattention and negligence of the users. For example, the target person did not change the default password, provided a password referring to his own identity, or recorded somewhere what the attacker found before the attack.
Passwords referring to ourselves make it easy for an attacker to invent because if we enter such a password — be it the name of our pet, hobby, child, or date of birth — they can be easily revealed with a bit of trace, such as looking at our social site.
Another group of passwords are the ones that are too complicated. A user can choose a password by using multiple characters and punctuation, which, however, due to the difficulty of the password, is usually recorded somewhere that an attacker can easily find.
The group of human-based techniques includes “identity theft,” a method of impersonation in which an attacker hides in the skin of another person. This person can be a fictional or real person; the point is that the attacker chooses that particular role to fit him best, thus making his role credible. For example, an attacker could impersonate service personnel, a cleaner or maintainer, which is beneficial because it is unlikely that we know every cleaner or maintainer in the organisation.
An attacker could also surrender to a new employee or an employee working in another department within the organisation, which also has the advantage of not knowing that all employees are known. The larger an organisation is, the less likely it is that we know everyone.
Another benefit of personalising an employee within an organisation is that it creates a sense of trust in the victim that the attacker is a member of the organisation, thereby not necessarily questioning his or her authenticity, so he or she can provide insight into various inside and confidential information without any suspicion.
An attacker could also impersonate a guest who arrives in the organisation. The problem with this attack method is that in many cases, the attackers who conducted the interview are not escorted after the given interview, so without supervision. While in the building, the attacker may gain possession of several inside and confidential information. In addition, the attacker, once inside the building, can easily hide in the skin of another person, which can also help them obtain a lot of confidential or inside information or even get even closer to the target person.
3.11. Open Source Intelligence - OSINT
Attackers can also obtain information through Open Source Intelligence (OSINT), which provides an attacker with access to the information they need from publicly available sources. The following can be considered as open-source: traditional media (electronic and printed), library materials, studies, public conference presentations, radio and television broadcasts, photographs, advertising material and the Internet. Attacking information from OSINT and social media is also good for attackers, as they can be used to obtain large amounts of data at a low cost.
3.12. Reverse social engineering
The method is more complicated than a “simple” social engineering attack since the attacker has to convince the victim that s/he needs help and to do so, he is the initiating party. The characteristics of reverse social engineering:
- The attacker does not initiate contact with the victim.
- Instead, the victim is tricked into contacting the attacker.
- As a result, a high degree of trust is established between the victim and the attacker since the victim is the person who first wants to establish contact and relationship.

4. Computer-based social engineering techniques
“There is no technology today that cannot be defeated by social engineering.” - Frank Abagnale
The other group of social engineering methods tries to trick the user through the computer. This type of hack is particularly beneficial for attackers, as it minimises the risk of detection.
4.1. Fake websites
An attacker can easily and quickly create a page where he offers free content for registration or draws a prize. The victim should register with an e-mail address and a password. With this method, on the one hand, the attacker can collect a lot of e-mail addresses for other types of attacks, and on the other hand, a lot of passwords. This is because most users use the exact string or something very similar in several places.
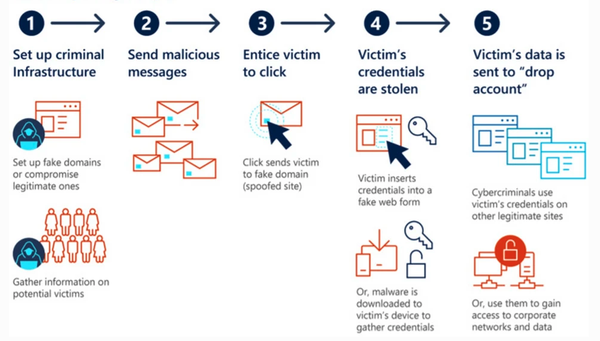
4.2. Phishing
Phishing is also a type of computer-based social engineering. Phishers invite their victims to a fake website in an e-mail message to ask them to provide their password or other confidential information. Fake e-mails and websites are the oldest phishing attack methods. This technique primarily threatens the clients of companies operating in the financial sector.
The essence of an attack is usually to trick customers into using a fake e-mail or website to enter their username and password in various ways, such as by referring to a data update or an anomaly. The number of phishing sites is increasing day by day.
Often, fraudsters ask bank customers to log in to their user account for security reasons; otherwise, they will be forced to lock their accounts. To prevent successful attacks, more and more banks are informing their customers about the dangers and methods of phishing; for example, we can read information and security tips on the institutions’ websites.
In addition to phishing, we can also find vishing and smishing methods. More detailed information on the subject of phishing can be read in the article Phishing: The most common cyberthreat and the everlasting fight against it.
Phishing is by far the most common form of social engineering attack. In the image below, you can see the illustration of a credential phishing example:
4.3. Whaling
Whaling is also a form of phishing attack that is usually targeted at business leaders. Letters specifically designed for top managers are generally received on behalf of business partners or government agencies. The attacker takes advantage of the fact that these letters are usually handled by the secretariat, who usually forwards them immediately to the competent authority.
4.4. Pharming
Pharming, or hijacking, is often referred to as next-generation phishing or the successor to phishing. Each of the methods presented above is based on deceiving or neglecting users, i.e., it requires the victim’s cooperation to some degree. In contrast, pharming uses a different technique, and no matter how careful and attentive the user is, they have no chance of noticing that they are actually visiting a fake website. The essence of the method is that attackers do not exploit the user but the vulnerabilities of the DNS servers and the unpatched security vulnerabilities of the browsers with one of the following methods.
4.5. DNS Cache Poisoning
Attackers most often take advantage of the fact that the IP addresses of pages frequently visited by users are saved in the computer’s DNS cache to speed up time-consuming translations. Thus, when a user types in the URL of a frequent page, the machine first caches it and its associated network address before the actual network query. However, this convenient and fast solution gives the possibility of abuse. An attacker could use a Trojan to modify the cache contents, and by rewriting the IP address of a website we visited, the victim can be redirected to a fake website. The victim then provides the attacker with all necessary confidential information by logging on.
4.6. Cross-Site Scripting (XSS) - execute foreign commands
In this case, an attacker tries to break into the code of a webpage and insert malicious code into the URL or form field.
5. The structure of the attack
“Social engineering is using manipulation, influence and deception to get a person, a trusted insider within an organisation, to comply with a request, and the request is usually to release information or to perform some sort of action item that benefits that attacker.” - Kevin Mitnick
Social engineering attacks are always to prepare for some actual more serious attack or large-scale fraud. The essence of this method is simply to acquire the right knowledge to carry out the intended damage and gather information to carry out the scam. Initially, the information is needed to build some sort of relationship with the target so that later, with more information, the attack can be refined and well-timed.
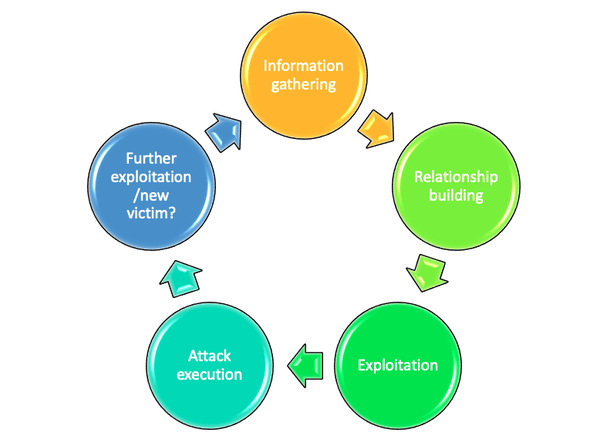
5.1. Information gathering
The first and most crucial step in a social engineering attack is to gather the appropriate information needed to build the relationship later. As this phase requires extensive work, it is particularly time-consuming and can take up to several weeks depending on the method used. The information may be collected over the Internet, by telephone or in person, by mail, or possibly by scanning the company’s garbage.
Internet
The Internet is a vast gold mine of information that can be used for very evil purposes with bad intentions.
The collection of information first begins with getting to know the selected company and its employees chosen as victims. The most obvious way to do this is to visit the company’s website, where information about employees, their positions, and the organisation’s structure is often posted.
From the data on the website, the attacker can easily select the target people who may have vital information and the employees who will be impersonated by the attacker if necessary.
Telephone
When making a telephone inquiry, the purpose of an attacker is usually to find out about a particular colleague (name, position, contact information, authority, etc.). But a phone call can also be used to ask a colleague for help, find out confidential information, or influence or manipulate someone in any way.
No one needs to be introduced to this technique. It is the cheapest form of attack that reaches most people and is very often used by attackers, of which there are many possible variants.
Personal visit
A personal visit is the most effective yet the riskiest method. By getting close to the target, the attacker can learn a lot of important information: organisation charts, schedules, holidays, invoices, other important documents or even passwords glued to monitors. An attacker can impersonate a wide variety of people: a customer, a co-worker, an outside colleague, a courier, a maintainer, an official, and so on. The role the attacker appears in is determined mainly by the goal to be achieved.
5.2. Relationship building
Finding the right person is vital to build a good relationship. The ideal victim can be an individual who can be easily influenced in some way, such as doing his job very conscientiously and easily being guilty of making a small mistake. Still, he can also be a dissatisfied co-worker who can only help the attacker to do harm.
However, the attacker has to play the role of a trusted co-worker or acquaintance who is helpful and understanding in all circumstances. A good social engineer is a person who can adapt himself/herself quickly to changing situations, someone with above-average empathic abilities: a real secret agent.
Before requesting a favour from the target person, the attacker usually first does some kind of favour to the victim himself, such as solving a problem, giving a little attention, and sharing confidential information. All this aims to build a stable relationship and trust, dispel any suspicions, and prepare for exploitation.
5.3. Taking advantage of the connection (exploitation)
After building trust, the time may come when the attacker asks for help or a simple favour. In this step, the attacker could even achieve his goal but, in any case, got closer to performing the actual damage. This is when the attacker uses the ‘something for something’ or the so-called ‘quid pro quo’ technique.
5.4. Carrying out the attack (attack execution)
If the attacker had not yet achieved his goal in the previous point, the information obtained allows him to carry out the attack or damage planned initially.
5.5. Further exploitation of the same victim or tracing of a new victim
Once the attack has been carried out, the attacker may decide to continue exploiting his victim if the risk of exposure is low. In addition, the attacker may also decide to launch a different attack against the same victim based on the information gathered or to search for another victim in possession of the information obtained.
6. How Can I Reduce the Risk of social engineering?
“It is impossible to work in information technology without also engaging in social engineering.” - Jaron Lanier
Social engineering is typically a form of attack that is almost impossible to fend off. However, there are several ways to reduce the likelihood of a possible attack succeeding. The most important thing is to develop an appropriate safety policy and communicate the danger posed by social engineering to the employees.
- Educate yourself, attend training sessions, seminars etc.
- Raise your security awareness
- Be aware of the information you are releasing
- Never give up sensitive information
- Follow procedures, rules, security guidelines
- Always be mindful of risks
- Think before you click
- Slow down, research the facts
- Keep your software up-to-date
- Do not download files you do not know
- Keep all devices and endpoints secure
- Set your spam filters to high
Keep in mind: The best defence against social engineering attacks is knowledge
BackThe first step in developing protection is to assess the current situation and map the vulnerabilities, as knowledge of the areas that pose a threat is essential for implementing preventive measures.
Once the identified deficiencies are known, the problem can be remedied according to the results: the development of safety regulations, the modification of the currently applied rules, or the training of users on safety awareness.
The target of attacks is people, so adequate protection can only be achieved by increasing security awareness, an essential element of knowing different forms and attack methods.
It is important to note, however, that security is not a state but a process. Therefore, it is not enough to commit ourselves to draft our company’s security policy and implement the necessary measures: these only reflect the current state at the time of preparation (more or less) and become obsolete later. Therefore, it is essential to update the rules regularly, repeat staff training, continuously monitor and periodically review security measures.
Therefore, one of the most critical parts of effective defence against this type of attack is the development of security awareness in both individuals and organisations, which aims to make people aware of the importance of information security and prepare them to prevent and defend against an attack.
For the defence to be effective, it is essential to know the different forms of attack. Numerous forms of attacks aimed at obtaining confidential information are known, one of the most common methods of attack being social engineering.
The best defence against social engineering attacks is knowledge, a description of the techniques used by the attackers, which can only be acquired through information security education and security awareness training.
6.1. Vulnerability mapping
Today, every company must have security tools, regulations, and information security regulations. However, these only make real sense if they are always complete, up-to-date, and enforced continuously and successfully. To this end, the procedures used need to be checked and reviewed from time to time. Human factor vulnerabilities can be mapped through a general information security audit or even a penetration test.
6.1.1. Audit
An information security audit examines not only the structure and operation of a company’s IT system but also several areas that need to be addressed in order to prevent a potential social engineering attack. This includes examining the company’s physical protection, IT equipment and media management, access protection, and corporate culture and user training.
6.1.2. Penetration Test
In a penetration test, company employees become victims of a simulated attack. Intrusion tests are performed by experts from information security companies and use only requested or authorised methods by the customer.
Employees should be aware that such tests may take place at the company, and the purpose of these tests is not to attack employees but to test workplace rules and tools.
Colleagues who may have been successfully deceived should not be reprimanded but should be properly trained and encouraged to follow the rules and apply what they have learned so that a scam like a test does not happen in real life.
It is essential to be aware that the survey results only reflect the actual situation at the time of its preparation. Over time, as a result of changes in the company’s life, risk factors also change. For example, think of a new employee or the introduction of new software that poses another vulnerability. Therefore, it is necessary to monitor security risks on an ongoing basis after the audit and review it from time to time.
6.2. Safety regulations and guidelines
Every company must have a security policy, one of the most important of which is the privacy and data security policy.
Physical security control of access to the building
The first step in preventing abuse of social engineering methods is the proper design of security rules for physical protection, the use of access control systems, a concierge service and security guards, and the development and use of appropriate identification procedures.
Visitors to the building must have some kind of ID, badge, temporary magnetic card or even an escort.
Empty/Clean desk policy
Employees are encouraged to keep as little information as possible on their desks. This applies to personal information, including photos, calendars, and notes. Once they are done, unpack from their desks and lock their belongings in the drawer. Not like the picture below:
- Tidy away papers and removable data storage media (USB flash drives, disks, etc.).
- Remove your documents from the printer, fax or photocopiers.
- Keep the essential media under lock and key, or even in a fireproof safe.
- If anyone leaves their PC unused for more than a few minutes, the screensaver should come on.
- A password should be entered to exit the screensaver and start work again.
- Use a special waste bin or a shredder to destroy sensitive paper documents.
Requirements for the handling of portable devices
When using these devices, it is necessary to prescribe appropriate encryption and the type of data that can be stored on them.
Requirements for discarded assets
Ensure that the contents of discarded computer equipment are disposed of by an appropriate procedure.
This advice, of course, applies not only to the office environment and companies but also to individuals. When you want to get rid of an old, worn-out computer, ensure your data has been entirely destroyed. Keep in mind that others may abuse your undeleted data on your hard drive or storage. The video below is a very good example of this case:
For further reading, please follow the link: Security Policy – Physical and Environmental Security
Requirements for the destruction of documents
It is imperative to destroy all documents with a shredder to prevent social engineering attacks using the ‘dumpster diving’ technique.
Requirements for the training of colleagues
In addition to occupational safety and accident training, employees must also attend information safety training. It is advisable to educate users at least once a year in which they can also hear about the methods of social engineering.
In addition to the above, the security policy should include requirements for valid e-mail, the correct conduct of telephone calls, and compliance with rules for terminated employees.
Finally, the information security rules should cover the principles of compliance methods and the definition of control and responsibilities.
6.3. Security awareness training
The purpose of security awareness training is to draw employees’ attention to the importance of information security and to explain the threats to employees and the possibilities of preventing and combating attacks.
Social engineering attacks do not only compromise employees who use computers, as many social engineering attack methods do not use computer systems.
It is essential to recognise that the education of all employees working for a given company is necessary, as the protection of the company can only be achieved if everyone is aware of the potential dangers.
An information security or social engineering related training aims to increase participants’ information security knowledge and develop the necessary skills. During the training, employees learn what to do, for example, in the event of a suspicious phone call, how to identify unknown visitors or recognise various social engineering attacks or techniques.
Those working in different positions have to attend personalised training sessions. Particular attention should be paid to customer service and reception staff training, as these are the most exposed employees to social engineering attacks.
7. Global social engineering landscape
“Social engineering has become about 75% of an average hacker’s toolkit, and for the most successful hackers, it reaches 90% or more.” - John McAfee
First of all, it should be noted that it is extremely difficult to quantify the extent of damage caused by social engineering. Although, on the one hand, social engineering itself is a complex multi-subject term (see this article), on the other hand, the attempt to influence and con others and the resulting inconveniences of estimating material damage is complicated. Not to mention that the victims often do not report these grievances as material damage, which can have many causes.
If we look at this phenomenon at the level of the individual, it can very often be the feeling of shame that prevents the scams from coming to light. The individual (but the same goes for companies) is, of course, not proud to have been deceived, harmed or exploited. So, the victim tries to disguise that he was deceived, exploited.
The same is true for companies in this respect: if it turns out that a company has fallen victim to an attack, the damage to reputation is much more significant than the material damage itself. This is why companies themselves often report that they have been the victim of fraud than to let people know from other sources what happened.
Based on all this, the data presented below are for information purposes only. Moreover, the below examples are just the tip of the iceberg only: most probably, the vast majority of cases are undiscovered or unreported and silenced.
Without wishing to be exhaustive, let us look at some examples from various sources of how significant social engineering is:
- Phishing remains the #1 threat action used in successful breaches linked to social engineering and malware attacks (source)
- From 2018 to 2019, there was a 640% increase in phishing attempts (source)
- Google blocked an average of 18 million coronavirus phishing attempts each day at the start of the pandemic (source)
- Cyberattacks projected to hit $6 trillion in annual loss in 2021, which has doubled since 2015 (source)
- 98% of cyberattacks rely on social engineering (source)
- 43% of the IT professionals said social engineering schemes had targeted them in 2020) (source)
- 71% of IT Professionals say someone at their company succumbed to a social engineering attack since the beginning of the Covid-19 Pandemic. (source)
- New employees are the most susceptible to socially engineered attacks (source)
- 60% of IT professionals citing recent hires as being at high risk (source)
- 21% of current or former employees use social engineering to gain a financial advantage, for revenge, out of curiosity or for fun.
- Social engineering spiked more than 500% from the first to the second quarter of 2018 (source)
- In 2020, 41% of higher education cybersecurity incidents and breaches were caused by social engineering attacks (source)
8. What is the situation in Luxembourg?
“‘Social engineering,’ the fancy term for tricking you into giving away your digital secrets, is at least as great a threat as spooky technology.” - Barton Gellman
In the spring of 2012, a group of psychology students at the University of Luxembourg pretended to be researchers in a survey asking 1208 passers-by from Esch sur Alzette, Diekirch and Luxembourg to investigate how people are manipulated into sharing their passwords with strangers in return for small gifts. The survey results can be read at the link below: Social engineering: password in exchange for chocolate. The main results and lessons of the survey are summarized below
Some participants received chocolate before being asked for their password, while those in the control group received chocolate only after the interview. Research has shown that this small gift significantly increased the likelihood that participants would sell their passwords. This life situation perfectly describes the definition of ‘quid pro quo’ on the website of ENISA.
The research report on “An Empirical Study on the Willingness of People to Communicate Personal Data” showed worrying results: 29.7% of all participants interviewed revealed their password to the interviewer. In addition, an additional 48.3% gave a valuable tip for their passwords. This means that almost four out of five people have revealed personal information for people they do not know. Nevertheless, the study demonstrated that people are willing to give important personal information to a stranger in the street with the help of a simple incentive (like a bar of chocolate) and the principle of reciprocity.
The example above also shows that the situation in Luxembourg is not very good either. Therefore, you may want to enlist the help of companies like Secmentis IT Security Services, which conducts penetration tests to map your company’s weaknesses.
Raising people’s awareness and training employees are key against social engineering attacks. Therefore, it is worth participating in the social engineering training of The Knowledge Academy, for example.
We need to keep in mind that Cybersecurity is a journey, not a destination. Pascal Steichen, CEO of SECURITYMADEIN.LU explained below the need to train employees and users to defend against social engineering attacks:
“Social engineering is where an individual becomes a target and is being abused to get access to data and systems. Awareness and training for “non-techie” users are becoming more important and more urgent in this respect to ensure that everyone has the basic knowledge and reflexes.”
9. How can SECURITYMADEIN.LU help?
“Social Engineering – The art of replacing what works with what sounds good.” - Thomas Sowell
As mentioned above, the human factor is at the heart of social engineering attacks. Every organisation, no matter its size, is prone to social engineering attacks. It only takes one empathetic employee to compromise your entire security network and leave your company vulnerable. Ensuring your entire workforce understands the various tricks of cybercriminals can be your best defence against social engineering.
9.1. CASES
CASES (Cybersecurity Awareness and Security Enhancement Services) is part of SECURITYMADEIN.LU. It has multiple services available to the public to raise awareness. The goal is to give every organisation the necessary tools and information to define its risk maturity and improve it. CASES offers the following tools:
TOOLS:
LINKS:
- Social engineering
- SOS – I am Being Asked for Confidential Information
- SOS – One of my Colleagues Knows my Password!
- SOS – Recognising a Suspicious E-mail
- SOS – Someone Asked Me Why My Colleague or My Boss Was Not at Work!
- SOS – A Colleague Wants to Borrow my LuxTrust Card!
- Security Policy - Human Factors
Fit4Cybersecurity: a self-assessment tool to help business owners implement a better cybersecurity strategy. This free online survey aims to assess the maturity of an organisation in terms of applicable good practices in information security.
CASES Diagnostic: a CASES expert visits your organisation (in Luxembourg) and presents a 2-hour-long interview. The expert will identify vulnerabilities, evaluate the level of maturity concerning your information’s security, and issue recommendations.
Monarc (Optimised Risk Analysis Method): a tool and method that allows optimised, precise, and repeatable risk assessment.
TACOS (TrustApp CASES for Obvious Security): a cybersecurity awareness application. It is a mobile app to educate users about cybersecurity risks with short articles, videos, tips and tricks.
Besides the above tools, the CASES website contains a large number of valuable articles on cybersecurity.
The video below introduces some of the social engineering techniques described in this article and gives some tips on how you can easily ward off these attacks:
10. Conclusion
“You can never protect yourself 100%. What you do is protect yourself as much as possible and mitigate risk to an acceptable degree. You can never remove all risk.” - Kevin Mitnick
It should be borne in mind that traditional security solutions (firewalls, anti-virus programs, intrusion detection and prevention systems, etc.) do not provide complete protection. Moreover, the security awareness of the human factor must also be taken into account. After all, with the development of security technology, vulnerabilities are reduced and causing attackers to target humans to obtain confidential information.
Therefore, effective protection can only be provided by technology solutions and security-conscious users who comply with security governance and rules and understand how everyone wants to influence the acquisition of confidential and inside information.
Overall, human-based social engineering techniques perfectly illustrate how to access the means of manipulation with little effort (follow-up, preparation) into a building and obtain confidential information. Therefore, it is of paramount importance to increase employees’ security awareness to reduce the likelihood of social engineering attacks occurring. Furthermore, in order to be prepared for such attacks, one must be able to recognise threats.
All right, you have made it; you have read this long article. Congratulations! You have taken a huge step towards being tricked less often and your data being more secure, whether personal or company data.
Finally, please watch this video that briefly summarises the main message.
The Past, Present, and Future of Phishing and Social Engineering:
“So, you can have the best technology in the world and spent hundreds of thousands of dollars on the best new shiny firewalls and intrusion detection systems and prevention systems. And if I could just call, dive in fish with an e-mail, and I can call one person inside that company on the telephone and convince them to do something on their computer… I bypass all that technology.” – Kevin Mitnick