- 01 Dec, 2021
- Topic of the Month

1. Introduction
“Security leaders are under a lot of pressure to show quick wins while knowing full well that everything they do will be heavily scrutinized and challenged, and ultimately, they will pay the price for things that are not under their control.” - Yaron Levi
Cyber insurance is not yet a widely known concept, although it affects everyone who uses any IT device (a computer, a smartphone, or an IoT device). Because we use these tools not in isolation but on the network, our exposure to cyberattacks is inevitable whether we want it or not.
The roots of cyber-insurance go back three decades when various tech companies began to use so-called E&O (errors and omissions) schemes. In the 1990s, rudimentary cyber insurance products only covered third-party liability claims.
Over time, and with the spread of IT culture, more and more potential damage events have been included in the potential risks, such as unauthorized access or data destruction. For a long time, these could only be used as supplementary insurance, until 5-10 years ago, when the protection of confidential data was included in the risks managed.

Image source: VistaCreate. This image has been designed using images from crello.com.
Later, stand-alone cyber-insurance products were born, focusing primarily on two core areas that still dominate: network security and unauthorized data access.
In a very short time, the available insurance products have been diversified according to the needs of each industry. Today, in essence, the concept of cyber insurance can mean different things depending on which segment’s needs are being served and how and to what extent it is influenced by information technology. Many people still use E&O insurance to cover damage caused by defective performance, although these do not necessarily apply to technology services.
This article describes the relationship between cybersecurity and cyber insurance. At the beginning of the article, we discuss cyber insurance, then explain why this is necessary, referring to how much damage cyberattacks cause annually. Then we talk in a little more detail about what cyber insurance covers, what it does not cover, what you should consider if you want to take out cyber insurance, etc.
After this brief introduction, let’s look at what major cyber threats companies and individuals faced in 2020 and 21, how much damage cyberattacks caused, and what the most significant threat was in terms of volume and damage.
2. Cyber Threat Landscape 2021
“If you put a key under the mat for the cops, a burglar can find it, too. Criminals are using every technology tool at their disposal to hack into people’s accounts. If they know there’s a key hidden somewhere, they won’t stop until they find it.” - Tim Cook
IT systems are threatened by a number of threats and are subject to a wide range of attacks. Although they attack computer systems, cyber threats are not pure IT-related but problems with profound economic implications. Cyber threats are ranked by business leaders as one of the most prominent risks today. A common feature of cyberattacks is that they affect the overall operation of companies.
The European Union Agency for Cybersecurity (ENISA) published the 9th annual ENISA Threat Landscape (ETL) 2021 report. This report identifies and evaluates the top cyber threats for the period between April 2020 and July 2021.
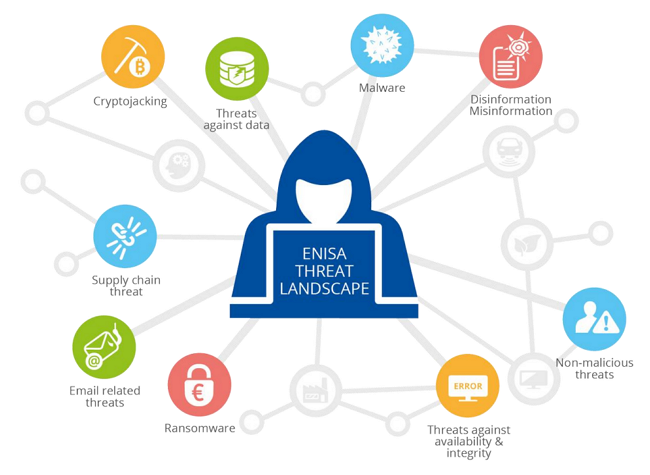
The report identified the following main threats:
- Ransomware
- Malware
- Cryptojacking
- E-mail related threats
- Threats against data
- Threats against availability and integrity
- Disinformation – misinformation
- Non-malicious threats
- Supply-chain attacks
The 117-page report is very detailed and discusses the attack techniques used, the notable events and trends recognised, and the mitigation measures proposed for each identified threat. Without wishing to be exhaustive, we also list some significant findings that support the legitimacy of cyber insurance and the need to take out such insurance.
- Ransomware has been the prime threat for 2020-2021
- Cybercriminals have been increasingly motivated to make money through cryptocurrency
- In the first quarter of 2021, the number of cryptojacking infections reached a record high
- COVID-19 is still the dominant lure in e-mail phishing campaigns
- DDoS campaigns have become more targeted, persistent and multivector
- The number of data leaks related to the health sector has jumped
- The COVID-19 pandemic became a multiplier of human and system failures, causing the most breaches in 2020
If we look at the extent of the damage caused by cyberattacks globally, the trend is perhaps best described by Statista. The amount of monetary damage caused by cybercrime reported to the Internet Crime Complaint Center (IC3) between 2001 and 2020 shows that the damage is growing exponentially. In particular, the last five years have seen drastic growth from 1 billion U.S. dollars in 2015 to 4.2 billion U.S. dollars in 2020.
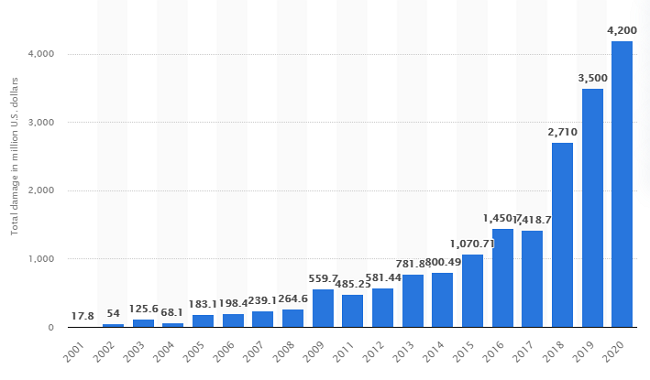
Statista: Amount of monetary damage caused by reported cybercrime to the IC3 from 2001 to 2020 (in million U.S. dollars)
Also, to support the need for cyber insurance, if we focus only on ransomware and consider their frequency and the extent of the damage they cause, we can state the following:
Ransomware incidents observed by OSINT (Open Source Intelligence) and collected by ENISA showed a steady increase since 2020 and a sharp increase in May and June 2021. As per Ransomwhere, the ransomware groups with the most significant financial gains in 2021 were Conti ($12.7 million), REvil/Sodinokibi ($12 Million), DarkSide ($4.6 Million), MountLocker ($4.2 Million), Blackmatter ($4.0 Million) and Egregor ($3.1 Million).
According to the “Ransomware Uncovered 2020 – 2021” Report by Group-IB, in 2019, the average ransom paid was around $80,000. In 2020, this more than doubled to an average of $170,000. The Unit42 Ransomware Threat Report for 2021 states that the highest ransomware demand grew from $15 million in 2019 to $30 million in 2020. Whatever source we look at, it is clear that the ransom demanded by the threat actors is increasing. And with record-high demands, we also see record-high pay-outs.
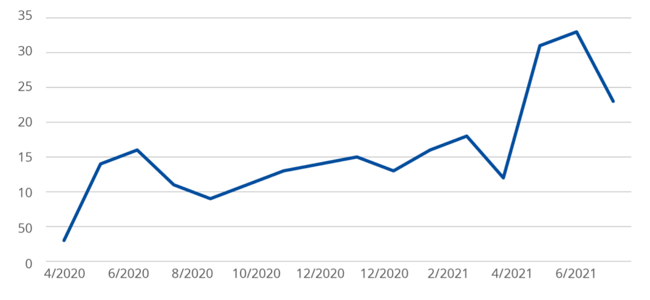
Ransomware incidents observed by ENISA (April 2020 – July 2021)
These are, in fact, self-aggravating processes, the assailants demand as much as they want, and as long as there is one to pay, the ransom will not be reduced. Nor should it be forgotten that the ransom is only one cost factor besides many others. Paying a ransom is no guarantee that you will get your sensitive data back, and no paralyzed IT system will become operational on its own by paying the claim.
On the contrary: the CoveWare survey showed that the overall cost of a ransomware incident more than doubled in only one year (the overall cost of remediating a ransomware attack increased from $761,106 in 2020 to $1.85 million in 2021).
The article ‘Ransomware: better to be afraid than to be frightened’ describes the types of ransomware, how they spread and the options to protect against them.
It does not matter which cyber threat we are talking about: the bad news is that we cannot avoid them; it is best to prepare for them and actively look for ways to defend and prevent them. There are many types and ways of prevention and protection, one of which is cyber insurance.
3. What is cyber insurance?
“As we’ve come to realize, the idea that security starts and ends with the purchase of a prepackaged firewall is simply misguided.” - Art Wittmann
Cyber insurance is an insurance product that can help organizations return to business after a cyberattack or data leak. More precisely,
“Cyber insurance is a tailor-made product that provides comprehensive cyber liability insurance and expenses a business may incur arising out of unauthorised use of, or unauthorised access to, physical and electronic data or software within an organisations computer network or business.” - SureWise
Cyber insurance can cover the losses and costs incurred by companies in connection with significant cyber intrusions, business disruptions, and other types of cyberattacks.
The video below summarizes and touches on the most basic questions about cyber insurance in less than 5 minutes. We get an answer to what cyber insurance is and whether companies and individuals need this type of insurance or not?
Source: What is cyber insurance?|Tech Talk
Comprehensive cyber security coverage can provide resources and reimbursement for, among other things, legal fees, incident preparedness and response support, loss of revenue and extra expenses, fines and penalties for non-compliance, data and hardware recovery and repair, and damage to reputation.
As with any other insurance product, we can enjoy the benefits of cyber insurance in the event of damage: if that happens, it can provide crucial support to help your business stay afloat.
4. Why do we take out any insurance?
“Let’s face it: the future is now. We are already living in a cyber society, so we need to stop ignoring it or pretending that it is not affecting us.” - Marco Ciapelli
The basic philosophy of taking out insurance on the part of the client is that in the event of damage, s/he can pass on the costs of the damage to someone else (the insurance company).
Cyber insurance works on a similar principle as any other insurance. If we buy a car, we take out insurance for it. There can be a wide variety of insurance options depending on the value of the car and the risks we want to ensure it against. But the same is true when buying an apartment or house, as we want to see our values safe.
We take out insurance so that in the event of an accident or incident, we do not have to pay the damage we have caused to someone else or the costs incurred after a burglary. In the case of cyber insurance, this is no different: IT solutions can be used to prepare for a cyber incident, but they cannot be avoided entirely. If the damage event (in this case, a cyberattack) occurs, it can have unforeseeable financial consequences.
If a company is “hacked”, or if an accident causes a computer system to be damaged, shut down, or destroyed, the company’s assets may be damaged, revenue may be lost, high unexpected costs or fines may be incurred. Malware can put valuable customer data into unauthorized hands. Concerning data protection liability (GDPR), it is thus quite clear that the problem is not primarily IT but economic.

Photo by RODNAE Productions from Pexels
Anyone who acts prudently prepares for a cyber threat on both the IT and insurance sides and builds their cyber defence system with an IT professional. Recent events, however, have highlighted that the use of traditional cybersecurity methods is no longer enough: the increasingly sophisticated malware, organized cybercrime, and the supply of the online black market call for a change of approach.
But not only should you prepare for a cyberattack as much as possible, but also for the potentially much greater economic impact of the risk. To do this, you should use the help of a cyber insurance expert, who helps you settle the damage, start with assessing the risks and develop the appropriate insurance protection.
5. Who is responsible for taking out cyber insurance?
“As cybersecurity leaders, we have to create our message of influence because security is a culture, and you need the business to take place and be part of that security culture.” - Britney Hommertzheim
Cyber insurance is not just the responsibility of IT but rather of economic professionals. On the one hand, you need to be prepared for a cyber threat from the information technology side. On the other hand, it is at least as important to do so from an economic point of view, as a cyberattack can have severe economic and financial consequences.
Think in processes both in terms of IT and economics. You can adequately prepare for a cyberattack if you know the weaknesses of your IT system and how you can strengthen them.
That is, you must first map out how vulnerable your current IT system is: in fact, you need to conduct a risk analysis and evaluate what cyber threats you face and what the consequences might be in the event of a successful attack.

Image source: VistaCreate (the image from Andrew Lozovyi has been designed using crello.com)
Last but not least, you need to plan how you can protect against possible cyberattacks and how you can get your IT system up and running as soon as possible.
Based on the above, it is easy to see that the decision-making process of taking out cyber insurance presupposes cooperation between several different departments within a company.
Of course, the IT department needs to organize activities related to the company’s IT infrastructure and cyberattack defence, but this also has obvious cost implications that need to be agreed upon with the company’s finance department.
In the case of cyber insurance, the IT department should inform the finance department and senior management about how vulnerable the IT system is and what effects of a cyberattack might be. The economics department can then make models of the economic impacts the company might face in the event of a cyberattack.
Those models need to be shared with the top executives of the company, who are the final decision-makers. Based on the data models, it is already possible to better determine what cyber insurance the company should take out.
6. Who needs cyber insurance?
“Cybercrime is the greatest threat to every company in the world.” - Ginni Rommety
Any company or organization that uses technology or data must be aware of cyber risks. Today, the list of cyber risks to organizations is growing exponentially. For example, ransomware is causing more and more severe and sophisticated attacks. However, this is just one of the cyber risks we need to understand, measure and manage.
With cyber insurance, you can transfer the risks to an insurance company and reduce the impact of cyberattacks on revenue and profits. Companies need to have comprehensive cyber risk security and complimentary risk management programs for proper risk management.

Photo by Kindel Media from Pexels
Ransomware attacks, risks to supply chain management and regulatory risks rank among the top 10 risks for company decision-makers as per Aon’s 2021 Global Risk Management Survey.
Ransomware attacks: In addition to the collapse of a company’s day-to-day operations, ransomware attacks can also have serious legal, reputational and financial consequences due to data leakage.
Supply chain-related risks: By attacking the supply chain through a single entry point, many organizations can be compromised at a later point in the chain, making them an attractive target for attackers. As a result of modernization and digitalisation, companies are exposing themselves to increased cyber risk.
Regulatory risks: Data protection regulations are becoming more stringent, and many organizations lack the comprehensive approach to address them. The GDPR is making more and more compliance requirements, and penalties are increasing.

VistaCreate image from Vitalik Radko
7. Individual problems - individual solutions
„Just as drivers who share the road must also share responsibility for safety, we all now share the same global network and thus must regard computer security as a necessary social responsibility. To me, anyone unwilling to take simple security precautions is a major, active part of the problem.” - Fred Langa
For any company, a significant portion of its operating costs are the acquisition and processing of the IT tools, hardware, software, databases, and information used. These types also show incredible variety, not to mention how they are organized into a system; the possibilities are essentially endless.
However, the problem is the lack of unified practices: preparing any offer by an insurer requires a severe preliminary examination. Such an examination requires a constantly trained workforce with up-to-date knowledge that few insurers have. Also, it is not easy to assemble a team with such extensive knowledge because insurance company professionals need to understand insurance and IT in detail. They need to understand what cyberattacks a company may face and the consequences, as this is the only way to calculate adequate insurance for their customers.
Hacker attacks can cause severe financial loss to companies; no wonder more and more people want to make out insurance to cover their damage. The greater the damage caused by attacks, the more difficult it is for insurers to set acceptable prices to both parties and determine what the insurance covers. Insurers are also wary that, unlike natural disasters, it is unpredictable how often and how much damage cyberattacks can cause.
The diversity of risks is also a difficulty. To name a few typical examples that a cyber insurer has to deal with: improper handling of personal data, network security, loss of corporate information, reimbursement of investigation costs, reimbursement of fines, restoration of company reputation, data recovery, copyright, downtime.

Image source: VistaCreate (the image from Andrew Lozovyi has been designed using crello.com)
In the case of cyber insurance, it is also difficult to speak of territorial scope, as all data accessible from an external network is subject to a potential attack, and this attack can come from virtually anywhere.
At the same time, there is a vast potential in the cyber insurance sector, primarily due to the growing threat. The increasing number and magnitude of claims catalyze the growth of demand and thus the segment quickly.
Companies have recognized the threat of cyberattacks and are increasing the size of their budget for cybersecurity. It is also an increasingly important phenomenon that, in addition to cyber security measures and developments, an increasing number of companies consider mitigating potential damage just as important.
8. Cyber insurance trends
„If security were all that mattered, computers would never be turned on, let alone hooked into a network with literally millions of potential intruders.” - Dan Farmer
There is a vast, largely untapped potential in cyber insurance. The importance of cybersecurity is beginning to be recognized in all sectors in an increasingly complex and high-risk digital environment. More and more insurance and reinsurance companies want to take advantage of this highly profitable but still emerging, less regulated market. Cyber insurance may soon be an expected service for customers, and hesitant insurers may miss out on significant business opportunities if cyber products are missing from their portfolios.
Meanwhile, many insurers themselves face significant cyber exposure in various business areas. Developing effective proprietary internal protection measures is also vital for insurers in the cybersecurity market to gain and retain credibility.
However, it is much more than just the credibility of insurers against their customers. Insurers need to invest adequately in their cyber security to store highly sensitive data from their customers (e.g. information about their customers’ cyber risks and defences) if they want to take out cyber insurance. And compromising or losing this data would lead to a loss of trust that would be extremely difficult to recover. Therefore, one of the top priorities for insurers is to assess and manage their cyber security exposure.
The chart below shows Global Data’s forecasts for the development of the global cyber insurance market between 2015 and 2025.
The data clearly show that between 2019 and 2020, there was an exponential increase in the market of cyber insurance products due to increased demand. The sharp growth is expected to slow in the future, but GlobalData still forecasts a $ 7 trillion market (in 2020) to grow to $ 20.56 trillion by 2025.
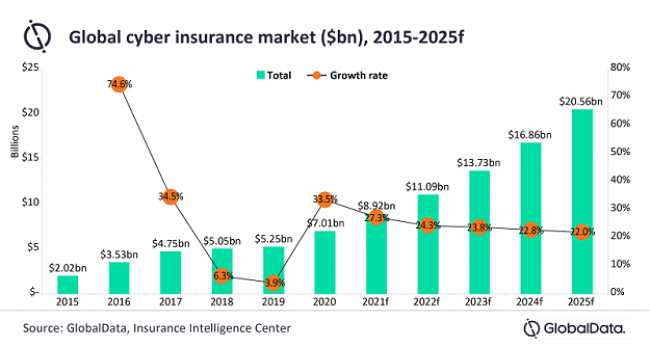
“The cyber insurance market has seen rapid expansion in recent years, with customers enjoying high coverage limits, flat rates, and abundant capacity as insurers sought to capture business in a highly competitive market. Despite lower cover limits and increasing premiums, we expect the cyber insurance market to see continual strong year-on-year growth up to 2025. The need for robust cybersecurity and cyber insurance is becoming apparent to businesses of all types and sizes, as the frequency and severity of cyberattacks continue to rise.” - Ben Carey-Evans, Insurance Analyst at GlobalData
9. Global cyber insurance market outlook
“Cyber threats have become the risks of the century, and if cyber security is one step behind new cyber threats, cyber insurance is two steps behind.” - Munich RE
With the rapid digitalisation of society, the demand for cyber insurance has never been as high as nowadays. As per the Accenture report Cyber Insurance: A profitable path to growth says, ’Cyber insurance premium income worldwide could grow by $ 25 billion by 2025, a 500% increase from today’s $ 5 billion premium level.’ So the potential is enormous in this insurance segment, but the challenges are also significant, as the risks are new and complex.
In recent years, there has been a surge in cyber incidents, particularly ransomware and data hacking, as well as DDoS attacks, many of which have been carried out using phishing techniques. In particular, the frequency and severity of ransomware have increased, facilitated by the RaaS (Ransomware-as-a-Service) service model and new attack methods such as double extortion. In the latter case, the attackers, on the one hand, encrypt the data and, on the other hand, steal it and threaten the victim to make it public so that the majority of victims would rather pay the attackers the desired amount.

Photo by Saksham Choudhary from Pexels
Cyber risk has long been seen as a problem for large IT companies. However, it has become increasingly clear that medium and small businesses, but also individuals, can be targets and victims. As a result of the COVID-19 epidemic and the spillover increase in the number of teleworkers, medium and small businesses have also felt the horror and dire effects of cyber attacks.
The long-term trend towards teleworking - and with it access to remote systems - will continue. Companies, regardless of size, and individuals need to be prepared for this, as they have to face new challenges and threats when working remotely.
As a result, insurance companies at the end of the cybersecurity supply chain need to rethink their strategies and develop new products to mitigate the increased cyber security threats of remote work.
Given these growing risk factors, it is hardly surprising that there has been a significant increase in interest in cyber insurance coverage. However, claims payments increased more than demand, leading to significant fee increases, especially in the US markets.
Cyber insurers reported a surge in losses in 2020 as companies were hit by costly cyberattacks and ransomware incidents. As a result, they have responded with significant price increases for their cyber insurance products since 2020.
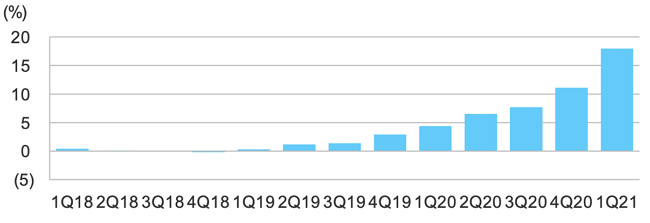
Source: The Record (Quarterly change in cyber insurance renewal premium rates)
The rise in prices in the cyber insurance market has given a special impetus and has led to the exclusion of certain players: for small and medium-sized businesses (who would need this product the most at the moment), cyber insurance has become unavailable or simply unaffordable.
- The damage caused by cyberattacks globally is growing exponentially (from $ 1 billion in 2015 to $ 4.2 billion in 2020)
- Ransomware has been the prime threat for 2020-2021
- The average ransom paid is also growing: from $80,000 (2019) to $170,000 (2020)
- The cyber insurance market is forecast to grow from $ 7 trillion (in 2020) to $ 20.5 trillion by 2025
- The price of cyber insurance has been rising since the first quarter of 2020
- The average annual growth rate of the cyber insurance market is around 20 per cent in Europe
- The European market is growing rapidly but still lags far behind the US market
- The dominance of the US cyber insurance market is prominent (it is bigger than the European and Asian-Pacific altogether)
Pricing for cyber risks is still in its infancy. In the case of ransomware insurance, it is still unclear to what extent the risk can be insured in the long run, especially since the availability of cover encourages and ultimately finances attackers.
Insurers need to find ways to increase supply profitably. Market players need to work together in ransomware-based claims settlement services, integrated risk-taking for dynamic pricing, or innovative technologies in cyber insurance products.
A great example of the latter is the partnership between Microsoft and the cyber insurance company At-Bay, to help the insurance industry create cyber insurance products and increase the security of small and medium-sized businesses in the United States. Under this partnership, U.S. businesses using Microsoft 365 can take advantage of At-Bay’s cyber security products at a discounted price if they use specific security controls, such as multi-factor authentication and Microsoft Defender.
While large companies, especially the most exposed (financial institutions, retail and healthcare companies), buy more comprehensive insurance packages, the SME sector is developing more slowly.
A wide range of cyber insurance policies are available, but the elements of both underlying cyber risk assessments and cyber coverage are diverse, making the cyber insurance market less transparent.
Because of the sensitivity of the information, policyholders are often reluctant to share details of their security measures and incident history. Difficult transparency and lack of information do not help the proper pricing of cyber insurance products and slow down the learning process for all parties - policyholders, insurers and reinsurers alike.
Other essential information and factors for good insurance contracts, such as independent certifications and risk assessments, business continuity plans, cyber security measures, or senior management commitment, are generally not available. It should be understood that cyber insurance goes hand in hand with good cybersecurity and strategy, but it cannot replace it.
In an environment of ever-changing technological threats, the insurance industry needs to find appropriate solutions to its customers’ risks without losing sight of disciplined insurance obligations.
10. European cyber insurance market
„When it comes to data protection, small businesses tend to be less well prepared. They have less to invest in getting it right. They don’t have compliance teams or data protection officers. But small organizations often process a lot of personal data, and the reputation and liability risks are just as real.” - Elizabeth Denham
In one of its recent surveys, the European Insurance and Occupational Pensions Authority (EIOPA) found that although the European cyber insurance industry is small, it is growing rapidly: insurers reported a 72% increase in gross premium income by 2018, amounting to € 295 million in 2018.
In the US, for 2018, the total cyber insurance market was $ 3.6 billion. Although the annual growth rate of the U.S. cybersecurity market has slowed, the U.S. still accounts for the majority of the global cybersecurity market.
EIOPA’s Summary Report of the EU-US Insurance Dialogue Project also stated that the cyber insurance market is still relatively new and evolving in Europe. Also, it is still underdeveloped relative to other commercial insurance products. Further development of the design of cyber insurance products will be required to cope with the dynamically changing cyber risks.
One of the key findings of the EIOPA’s report “Understanding Cyber Insurance - A Structured Dialogue with Insurance Companies” is a need for a deeper understanding of cyber risk, a fundamental challenge for the European insurance industry.
Statista predicts that the European cyber insurance market will grow exponentially between 2020 and 2030 and double between 2020 and 2025. The average annual growth rate of the cyber insurance market will be around 20 per cent in Europe. However, behind the high growth rates is not the prevalence of high-quality and widely used cyber security and insurance products but the backwardness of the European market compared to the US.
The International Association of Insurance Supervisors (IAIS) made a report called ‘Cyber Risk Underwriting: Identified Challenges and Supervisory Considerations for Sustainable Market Development’.
The report provides a comprehensive picture of the European cyber insurance market. It is also an excellent starting point for understanding how the European market is developing and how big it is compared to other markets.
The graph below shows a forecast of the changes in the cyber insurance market over time for the period 2018-2025 for the North American, European and Asian markets. The dominance of the US market is striking. It is also clear that the European market is growing rapidly but still lags far behind the US market.
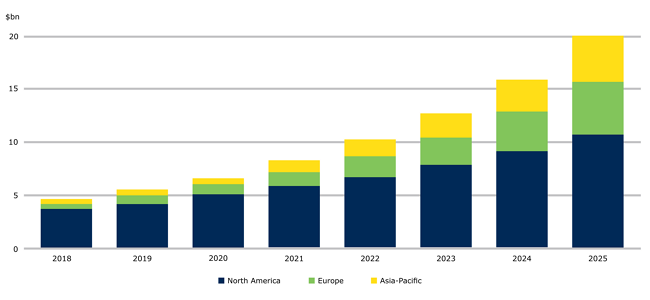
Source: IAIS calculations based on Munich Re, IAIS December 2020 (on Reports Insurance Europe)
11. Why is so much scepticism surrounding cyber insurance?
„Most people are starting to realize that there are only two different types of companies in the world: those that have been breached and know it and those that have been breached and don’t know it. Therefore, prevention is not sufficient, and you’re going to have to invest in detection because you’re going to want to know what system has been breached as fast as humanly possible so that you can contain and remediate.” - Ted Schlein
There is very little publicly available data on the extent and financial impact of cyberattacks. The difficulties caused by the lack of data are intensified by the rate of development and spread of threats.
While the approximate costs of restoring the systems can be estimated, there is insufficient historical data to determine the indirect costs (for example, brand reputational damage). Market participants are increasingly concerned about the increasing frequency of cyberattacks and the ability of less experienced insurers to withstand possible series of high-loss claims.

VistaCreate image from Vitalik Radko
The benefits of cyber insurance do not end with minimizing financial losses. One of the biggest problems in the information security market is that it is difficult to quantify the return on investment (ROI) to reduce information security risks. However, it is often difficult to persuade management to spend on something intangible (no security incident has occurred because of the money spent).
However, the risk assessment underlying cyber insurance and the related insurer pricing models make it easier to quantify the amounts spent on information security, which directly impacts business leaders’ management budgets and indirectly on the information security market. The beneficial effects of this may also be felt in the insurance market in the future since the more extensive and accurate set of information available may simplify and refine price calculation models.
12. What to look for when taking out cyber insurance?
„We shouldn’t ask our customers to make a tradeoff between privacy and security. We need to offer them the best of both. Ultimately, protecting someone else’s data protects all of us.” - Tim Cook
It is beneficial for companies to take out cyber insurance for several reasons. In addition to reducing the financial risks associated with cybercrime, companies can better understand their IT preparedness and information security maturity. A comprehensive analysis of current information security capabilities and existing risks is a prerequisite for taking out such insurance.
The risk analysis helps identify and understand companies regulatory and legal exposure, incident response times, and the potential costs of reputational loss. Various insurance schemes are also available in the market to mitigate the damage caused by cyberattacks. Each insurance product is diversified based on industry-specific specialities.
In addition to minimizing business disruption and providing financial protection during an incident, cyber insurance can help with post-incident legal and regulatory action.
It is imperative to note that cyber insurance alone does not protect an organization’s IT systems; it does not prevent criminals from taking successful action against the company’s IT infrastructure or resources. As with an apartment or car, the owner’s responsible behaviour (installing locks, alarms) to avoid damage is very important and largely determines the terms or price of the insurance to be taken out.
In other words, it is the responsibility of users (whether individuals or companies) of computer products on the network to behave carefully, be aware of potential threats, demonstrate preventive defensive behaviour, and do their utmost to avoid becoming a victim of a cyberattack.

Source: Picjumbo – Viktor Hanacek
12.1. What do cyber insurances cover?
This section outlines what a cyber insurance offer may contain. Because companies can be very different and threatened by different cyber threats, cyber insurance is also company-specific. In each case, a thorough review of the contract with the insurer is required; the following are guidelines only.
A detailed cyber insurance policy covers three main categories of financial risks:
First-party expenses:
This category includes costs that an organization would typically have to pay to mitigate losses related to a data breach or a privacy incident. These costs may include incident response and digital forensic services, PR services to deal with reputational damage caused by breaches, stakeholder notification, and other costs related to responding directly to cyber incidents.
Third-party expenses:
This category covers the costs of protecting fines and sanctions imposed by regulatory authorities, for example, legal fees to protect lawsuits against the company.
Cybercrime costs:
It is about the financial losses that result directly from a crime. An example of this is the theft of funds as a result of digital fraud.
The most prominent cyber risks are security, operational, privacy, and service risks. In most cases, cyber insurance is designed to protect you against these primary risks through these insurance arrangements:
- Privacy liability
- Media liability
- Network security
- Network business interruption
- Errors and omissions
Privacy liability
Privacy liability coverage protects your company from obligations arising from a cyber incident or data protection law violation.
Media liability
This liability provides coverage for intellectual property infringement resulting from the advertising of your services. It applies to both your online as well as printed advertising.
Network security
The network security aspect of cyber insurance covers your business in the event of network security failure. It can include a data breach, malware infection, ransomware, or business e-mail compromise. Network security coverage may include
- Legal expenses
- IT forensics
- Breach notification to consumers
- Public relations expenses
- Negotiation and payment of a ransomware demand
- Data restoration
Network business interruption
This liability helps when your network goes down due to an incident, so you can recover lost profits, fixed expenses and costs incurred for the time your business was impacted.
Errors and omissions (E&O)
E&O applies to claims arising from fault or failure to perform your service.

Photo by RODNAE Productions from Pexels
12.2. What do cyber insurances not cover?
Cyber insurances exclude certain types of claims. Here are some typical examples for exclusions:
- Bodily injury
- Potential future lost profits
- Property damage
- Contractual liability
- Utility failure
- Intentional dishonest
- Impairment due to theft of intellectual property
- Acts committed before the retroactive date
- Betterment: the cost of developing internal technology systems, including software or security updates after a cyber event
The best cyber insurance is company-specific: as there is no standard product suitable for every life situation, the insurer needs to know your company, its preparedness against cyber threats and the risks your company may face.
13. Relationship between insurance and risk in the case of cyber insurance
„We’re all going to have to change how we think about data protection.” - Elizabeth Denham
Several factors hamper the development and evaluation of cyber insurance products. The risks involved have different characteristics from those that can traditionally be provided. The main ones stem from the frequency of events and the intertwining of the cyber world.
13.1.The occurrence of cyberattacks is very common
Cyberattacks are very frequent, and the material loss caused by each attack can be in the tens of millions or even hundreds of millions of dollars in some cases. Insurers may face a series of severe losses if they do not carefully assess the risks when selling a cyber insurance product to their customers.
13.2. Additional indirect losses that are difficult to calculate
Business process disruptions and systems improvements cause additional indirect losses, such as fines, legal costs, and reputational damage. All companies operate in an increasingly interconnected ecosystem: not only their own systems and data are vulnerable but also the data and IT systems of their connected suppliers, customers, and strategic partners. The enhanced prevalence of IoT further increases the degree of connectivity and vulnerability for all companies interconnected in the same supply chain.

Photo by Nicola Barts from Pexels
13.3. It is difficult to detect, assess and financially assess risks
There are only limited data available on the financial impact of IT security attacks, making this type of risk difficult to assess and price. While the cost of restoring systems can be estimated based on recovery data from fire or water damage, there is not enough data to quantify the additional loss of brand reputation caused by cyberattacks and compensation payments. Uncertainty is exacerbated by the fact that IT security intrusions, by their very nature, can go unnoticed for months or even years, risking additional or even cumulative losses.
Last but not least, it is worth noting that it is delicate and inconvenient for companies affected by cyberattacks to declare and publish how much damage they have suffered in a cyberattack. Many times, the losses resulting from a loss of reputation are far more significant than the damage itself.
13.4. Data sharing can refine pricing
The key to more accurate pricing is more efficient data sharing. Customers are reluctant to acknowledge information security breaches for reputational reasons, while insurers are reluctant to share data because of concerns about losing competitive advantage.
However, based on the above, it can be stated that to form a reasonable price, the insurers need to have as much data as possible and understand what risks their clients face and the financial implications of these risks. However, GDPR’s legislation on the obligation to notify data breaches can help increase the amount of data available.

Source: Picjumbo – Viktor Hanacek
13.5. Pricing approach in the cyber insurance market
Fair pricing to cover payments is critical for insurers. Due to the novelty and immaturity of cyber insurance and the little historical data available, pricing of cyber insurance products requires more sophisticated pricing techniques and models in contrast to the traditional, well-defined risk-loss relationship. Insurers are constantly refining their risk-based pricing techniques and models despite the difficulties as the insurance market increasingly understands the cybersecurity industry.
One of the basic principles for insurers’ pricing is how much they can lose and how much they can afford.
Insurers strive to understand companies’ cyber security threats better, collect as much relevant data as possible, and devise a plan to calculate their insurance amounts and build a product portfolio. To design threat and customer vulnerability assessment systems as efficiently and accurately as possible, insurers involve specialists. Specialists working in different business and technology areas need to work together to create the right products and prices.
Instead of all-encompassing contract terms, insurers use individual pricing with a full screening of counterparty vulnerabilities when creating cyber insurance quotes.
In addition to cyber security risk analysis, a full screening may include an assessment of customer processes and responsibilities and also reviewing the operation of management. It can also include assessments and attack simulations for industries or individual businesses to test vulnerabilities and plan responses.
Therefore, the pricing process and methodology are very similar to when an average person takes out life insurance and the insurer asks a series of questions about the client’s health before giving the draft. However, while a person’s health status cannot usually be changed positively after a risk analysis, preventive technologies and procedures can be developed to reduce the company’s cyber security exposure and thereby reduce the cost of its cyber insurance.
Both insured and insurers benefit from a better understanding and control of accepted risks, which allows for more accurate pricing.
13.6. Continuous review of insurance contracts
In addition to annual contract renewal cycles, there is a growing need for real-time contract renewals. This dynamic approach is comparable to security software updates.
14. You are not alone!
„Amateurs hack systems; professionals hack people.” - Bruce Schneier
Remember, you are not alone: companies and agencies can help you in Luxembourg if you have a question about cyber insurance or want to take out such insurance. Visit the CYBERSECURITY Luxembourg National Cybersecurity Portal and search among companies in the Ecosystem.

VistaCreate image from Andrew Lozovyi
Besides the well-known companies like AXA Luxembourg and Aon Global Risk Consulting Luxembourg, you may find other companies with cyber insurance-related products or services on their palette.
From the Foyer website, you can gain cyber insurance-related knowledge and learn about their product called Cyber insurance pro. What is more, you may even download the document Protect your data from cyber attacks (in French).
EASI (Enterprise Applications and Services Integration) Luxembourg provides IT infrastructure & security solutions and services both on-premise and in the cloud. Besides offering penetration testing, forensic analytics and vulnerability scanning services, EASI also offers security audits. EASI is teaming with HDI: EASI provides cyber defence, and in the event of a successful attack, recovery services, while HDI protects to limit the impact of an attack with its cyber insurance product.
Nacora (Luxembourg) S.à r.l. is an independent commercial insurance broker specializing in risk and claims management. Besides cyber risk assessment and cyber insurance, Nacora provides Cargo Insurance, Logistics Liability, Trade Credit and Commercial Insurance Packages.
ABIL (Advisory, Brokerage & Insurance Leaders S.A.) is a Luxembourg-based company specialized in risk management, advisory and insurance brokerage services.
Willis Towers Watson Luxembourg S.A. is a leading insurance brokerage and advising company in Luxembourg. It provides an integrated, holistic and comprehensive approach to Cyber Risk Management. First, they assess your risk, then they quantify your exposure to risks, and finally, they protect your organisation.
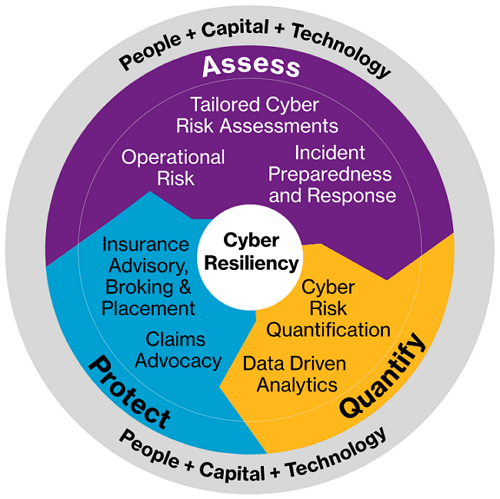
Source: Willis Towers Watson’s Cyber Risk Management
15. How can SECURITYMADEIN.LU help?
„The knock-on effect of a data breach can be devastating for a company. When customers start taking their business—and their money—elsewhere, that can be a real body blow.” - Christopher Graham
SECURITYMADEIN.LU is the cybersecurity agency for the Luxembourg economy and municipalities: its three departments (C3, CASES, and CIRCL) help achieve its goals.
CASES (Cybersecurity Awareness and Security Enhancement Services) has multiple services available to the public to raise awareness concerning cybersecurity. The goal is to give every organisation the necessary tools and information to define its risk maturity. CASES offers the following tools:
Fit4Cybersecurity: It is a self-assessment tool to help business owners implement a better cybersecurity strategy. This free online survey aims to assess the maturity of an organisation in terms of applicable good practices in information security.
CASES Diagnostic: a CASES expert visits your organisation (in Luxembourg) and presents a 2-hour-long interview. The expert identifies vulnerabilities, evaluates the level of maturity concerning your information’s security, and issues recommendations.
Monarc (Optimised Risk Analysis Method): a tool and method that allows optimised, precise, and repeatable risk assessment.
- A comprehensive risk analysis is a prerequisite for taking out cyber insurance
- During risk analysis, you can map out your company’s weaknesses
- By recognizing your company’s weaknesses, you can be better prepared for possible cyber attacks
- Cyber insurance is not only the responsibility of IT but also of economic professionals
- Good cyber insurance is always tailor-made and company-specific
- Be aware of what is covered and what is not covered by the insurance
- Cyber insurance can help you get back into business faster
TACOS (TrustApp CASES for Obvious Security) is a mobile cybersecurity awareness app to educate users about cybersecurity risks with short articles, videos, tips, and tricks.
In addition to professional CASES training sessions, you may also get valuable information on the SECURITYMADEIN.LU portal, where you can read articles, register for the Cybersecurity Breakfast series, watch the Lëtz Talk About Cyber series or read cybersecurity-related news, besides other things.
The Computer Incident Response Center Luxembourg (CIRCL) is also part of SECURITYMADEIN.LU, with the initiative to gather, review, report and respond to computer security threats and incidents. One of their services is information leak analysis, and you may check the list of reported detected information leaks in Luxembourg.
CIRCL develops different tools, one of which is called the AIL- Analysis Information Leak framework. It is open-source software that can be installed to find a leak of information.
The Cybersecurity Competence Center Luxembourg (C3) helps organisations reach a mature level in managing their cybersecurity competence.
The ROOM#42 simulator is one of the vital training infrastructures of C3 and a unique concept in Europe. Its specific immersion training approach brings up to 8 trainees in a one-hour realistic cyber-attack simulation, offering deep and comprehensive learning based on an intense experience.
16. Conclusions
„A breach alone is not a disaster, but mishandling it is.” - Serene Davis
If you are still reading this article, you are definitely interested in cyber insurance. In the below 45-min-long conversation with Daniel Kasper (Cyber Risk Researcher & Economist), you may learn a lot about the considerations behind cyber insurance.
We get answers to questions such as what cyber risks can be insured, how big is the cyber insurance market, how much cyber insurance costs, and what are the misconceptions about cyber insurance?
Source: Discussion with Daniel Kasper: What is Cyber Insurance?
Risks from cyber threats can affect an entire company at any time. Today’s companies rely heavily on technology in various areas. Failure to use a proper cyber insurance product can lead to brand and reputation damage, data theft, regulatory investigations, stakeholder dissatisfaction, and financial losses.
The continuous, increasing digitization of companies and their environment is a clear trend, which opens up new perspectives for the insurance market: it offers the possibility of developing and introducing new insurance products. As a result, one of the fastest-growing branches of the insurance market is cyber insurance, which covers the risks of the new area.
Companies are also trying to keep up with the changing risk environment due to digitalisation, emphasising cybersecurity and incorporating cybersecurity and information security risk reduction into their strategies.
One of the biggest problems in the information security market is that it is difficult to quantify the return on the investment spent on reducing information security risks. However, through cyber insurance, with the underlying risk assessment and associated insurer pricing models, this becomes more tangible.
The number of information security incidents and the rate of data theft related to intellectual property, primarily patents, is increasing year by year.
Advanced cyber security technologies cannot stop all cyberattacks, as cybercriminals use advanced technologies to bypass protection mechanisms and exploit vulnerabilities.
As a result, the cybersecurity market is primarily reactive, and as the information security market grows, customers are increasingly buying cyber insurance products to mitigate the adverse financial effects of information security incidents.
The increasing digitalisation and globalization of our environment, the growing interdependence of companies in supply chains, and the proliferation of telework are all factors that increase the cyber threat and vulnerability of companies and individuals. It has long been impossible to talk about any actor being ‘immune’ to cyberattacks, as new types of threats emerge every day.
Based on the above, the legitimacy of cyber insurance is unquestionable. In the future, cyber insurance is likely to be as widespread in the product range of insurance companies as life or property insurance products.
As anti-virus programs appeared and became widespread in the 1980s, various cyber insurance policies are becoming more prevalent. We will soon reach a time when it is no longer a question whether a company or even an individual has this type of insurance.
So, is cyber insurance indispensable or unnecessary? If someone wants to take out insurance, then, as a customer, they consider how likely certain damage or loss will occur.
According to a 2017 article in Security magazine, there were more than 2,200 cyberattacks per day that year; in other words, an average of 39 cyberattacks per second in the world. Since then, the situation has only worsened…

