- 27 Jul, 2021
- Topic of the Month

1. Introduction
“The only constant in the technology industry is change.” – Marc Benioff
The proliferation of the Internet and smart mobile devices has fundamentally changed our lives. The latest smart mobile devices, which can be found in the pockets of almost everyone, also present new types of challenges.
The security of smart mobile devices must be a priority. The reason for this is straightforward: we all have at least one device in our pockets through which we live our lives. A smart mobile device, be it a mobile phone or a tablet, can be compared to a computer in terms of its capabilities, and as such, it faces the same risks as a computer. However, this recognition is unfortunately not considered common for the average user: even if they use it to perform similar activities, they do not devote sufficient time, energy, and money.
The term “smartphone” was first used in 1997 by Ericsson for the GS88 ‘Penelope’.

Source: The evolution of the smartphone
The expansion of mobile devices is of paramount importance to many organisations today, as increased mobility helps improve businesses’ operations and productivity. However, the increase in organisational mobility also increases the number of mobile devices that reach the organisation’s systems remotely and present more and more endpoints and threats that need to be protected in some way from attacks.
In the first part of the article, we briefly review cybersecurity concerns about mobile devices, then look at what is covered by the term ‘BYOD’, how it relates to mobile devices, and how the introduction of a BYOD plan influences the cybersecurity situation at a company.
2. What are the cybersecurity risks of mobile devices?
“Mobile is becoming not only the new digital hub but also the bridge to the physical world. That’s why mobile will affect more than just your digital operations — it will transform your entire business.” - Thomas Husson
2.1. Social engineering
Social engineering is one of the most widespread, most diverse, and least speculative forms of attack that exploits human weakness, predictability, and deception to obtain data or resources. It is ‘The art of manipulating people.’
How to protect against social engineering attacks?
The best protection against social engineering attacks is to teach users how to spot such attacks and how to avoid them.
2.2. Data leakage via malicious apps
One of the most significant cybersecurity vulnerabilities and threats stems from the fact that employees and individuals can choose from many applications and download them to mobile phones. When we download different apps on our phones, they ask for access to certain files and folders. But let’s face it, most of us do not read in detail what accesses we give to applications.
However, a lack of attention or even carelessness can make our mobile devices vulnerable and thus the company itself where we work. Even if the app works the way it is supposed to, it can still extract corporate data and send it to a third party.
How to protect against data leakage?
The best way to protect against data leakage is to use mobile application management (MAM) tools. These tools allow IT administrators to manage (delete or control access permissions) enterprise applications on their employees ’devices without disrupting their personal applications or data.
2.3. Spyware
Spyware is used to collect data and is most commonly installed on a mobile device when users click on a malicious advertisement.
How to protect against spyware?
Dedicated mobile security applications can help detect and eliminate spyware installed on the employees’ devices and used to access corporate data. Keeping employees’ operating systems and applications up-to-date can also ensure that their devices and data are protected from the latest spyware threats.
2.4. Unsecured public Wi-Fi
Public Wi-Fi networks are generally less secure than private networks. In the case of a public Wi-Fi network, we do not know who set it up, how it is encrypted (at all?), and who is accessing or monitoring it. More and more companies are offering their employees the opportunity to do their work remotely. Still, no one controls who and from what channel they access the company’s servers while working. The video below illustrates through an example very well the dangers of using public Wi-Fi:
Source: Wi-Fi publics - YouTube
How to reduce the risks posed by insecure public Wi-Fi?
The best way to protect your organisation from threats over public Wi-Fi networks is to require employees to use a VPN to access corporate systems and files. This practice ensures that their session remains private and secure, even if they use a public network to access their systems.

Photo by Bernard Hermant on Unsplash
2.5. End-to-end encryption gaps
Unencrypted public Wi-Fi networks are among the most common encryption vulnerabilities and pose a considerable risk to organisations. Since the network is not secure, cybercriminals can access information that employees share between their devices and systems. However, it is not just Wi-Fi networks that pose a threat: any unencrypted application or service can potentially give cybercriminals access to sensitive company information.
How to protect against end-to-end encryption gaps?
Encryption between endpoints is essential for any confidential work information. This includes ensuring that all service providers you work with encrypt their services to prevent unauthorised access and ensure that your users and systems are encrypted.
2.6. Lost or stolen mobile devices
Lost and stolen assets are not a new threat to organisations. However, more people work remotely in public places, such as coffee shops. Therefore, lost and stolen devices pose an increasing risk to organisations.

Photo by Tiitus Saaristo on Unsplash
How to protect your company against lost or stolen device threats?
Make sure employees know what steps to take if they lose their mobile devices. Since most devices have remote access to delete or transmit information, ask your employees to activate these services. Mobile device management tools (MDMs) can also help secure, encrypt, or delete sensitive corporate data from a lost or stolen device.
2.7. Poor password habits
Adequately strong password usage is one of the most important and most basic cybersecurity practices you can use to fight against cyberattacks. One source of the problem is that employees often use weak and easy-to-guess passwords, and the other is that the same password is very often used in personal and corporate systems.
These bad password habits pose a significant cyber threat to organisations whose employees use their personal devices to access corporate systems. Because both personal and work accounts can be accessed on the same device with the same password, this makes it easier for a bad actor to break their systems.
There are many lists of the worst passwords on the Internet. Below is a list of the worst 20 passwords from Komando.com:
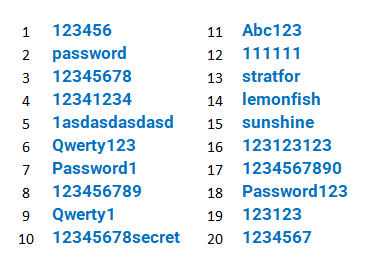
How to protect against poor password habits?
Educate employees since they may be unaware that their password habits could put their company at risk. Help employees change their bad password habits by making them aware of it and use security policies and two-factor authentication.
2.8. Out of date operating systems
Mobile security requires constant work to find and fix vulnerabilities. However, these fixes only protect the organization if employees are willing to keep their tools updated.
How to keep mobile operating systems up to date?
Both Google and Apple allow organisations to send updates to managed Android and iOS devices. Again, make employees aware of the threats, educate them on minimising the threats, use strong policies and continuously monitor the situation with a Mobile Device Management (MDM) tool.
2.9. Internet of Things (IoT) devices
The cybersecurity risks associated with IoT are described in the article ‘IoT: Is it a blessing or a curse?’ The basic problem is that there are many IoT devices, their use is unregulated, and often companies do not even know exactly how many such devices are connected to the company’s network. The first step in protection is to map out exactly how many IoT devices you have, what security risks they pose, and then manage those devices with a Mobile Device Management (MDM) tool.
3. Bring Your Own Device - BYOD
“BYOD presents a significant cultural shift for the CIO and their organisation. On the one hand, it presents increased complexity to management of data. On the other hand, it improves flexibility, capital exposure and employee morale.” – Tim Crawford
3.1. What is BYOD?
The acronym BYOD comes from the term “Bring Your Own Device” and describes a working model in which employees bring their own portable devices (laptop, tablet, smartphone) into the office and use them for both work and private purposes. It is an increasingly widespread trend or attitude in corporate culture, based on the goal of employees working on their private devices. These devices can be laptops, smartphones, tablets, and even desktop PCs to access corporate networks, applications, and data.

Photo by Vadim Sherbakov on Unsplash
In the case of BYOD, we actually ‘bring’ our tools to an office; more precisely, we use our own devices on the company’s network in order to solve our work and tasks for the company.
In today’s world (and especially since the outbreak of the pandemic), stationary work from the office is beginning to transform into a slightly more casual, less static type, where we can do our corporate work from almost anywhere.
An employee’s IT toolbox was recently exhausted on a desktop computer, possibly a corporate cell phone. However, new technologies are becoming more widespread, and employees are increasingly willing to use their devices not only at home but also on the go or for corporate work.
In the section on mobile devices, we have already looked at the cyber threats we face when using them. This section reviews the pros and cons of using BYOD, the cybersecurity risks we encounter, how to prepare for them, and the options we can give to minimise them.
4. What are the advantages of BYOD?
“Let’s face it: the future is now. We are already living in a cyber society, so we need to stop ignoring it or pretending that it is not affecting us.” – Marco Ciapelli
One of BYOD’s successes is that it provides specific benefits to both employees and employers.
BYOD is a relatively new phenomenon: it emerged around 2014. It mainly spread because employers saw its key benefit in cost reduction as the cost of IT equipment investments was drastically reduced with the introduction of BYOD.

Source: Slideshare
4.1. Advantages of BYOD to employees
1. High flexibility and workforce mobility
Enthusiastic fans at BYOD see high flexibility as their most significant advantage: working from anywhere, anytime. BYOD allows employees the flexibility to use a variety of tools to meet their work and personal needs. If employees have access to company data anywhere, anytime, they can usually work from anywhere, just like in an office.

Photo by Austin Distel on Unsplash
2. Faster adaptation
Employees adjust faster on familiar devices, speeding up the workflow and improve productivity. In addition, the use of familiar tools in the workplace at work can reduce learning time.
3. Increased productivity among employees
One of the reasons for increased productivity is the ability to work on your own and, therefore, a familiar device. The choice of the tool is entirely up to the worker, which reflects his needs. Tech-savvy employees can use their own up-to-date, cutting-edge devices, which can boost innovation and productivity.
4. Improved employee satisfaction
BYOD provides employees with more autonomy and flexibility, thus increasing satisfaction and work-morale.
5. Flexible working hours and a sense of freedom
Often, part of BYOD is that employees can work on their own devices and according to their own schedule, giving them additional flexibility and a sense of freedom.
4.2. Advantages of BYOD to employers
1. Reduced IT procurement costs
Companies see BYOD’s most remarkable advantage in not having to procure IT tools and make them available to employees. Many companies felt an irresistible desire to take advantage of this vast financial advantage and thus pass on the costs of equipment purchases and software licenses to their employees.
On the other hand, the biggest advantage of BYOD stems from one of its most significant drawbacks: it is more difficult, more complex, more complicated for the IT departments of employers to inspect employees’ machines.
2. Cutting-edge tools create a better image of the company
While the hardware offered by companies is often obsolete, the employees own devices usually represent the latest available technology, thus raising the company’s technological level in a figurative sense. BYOD is primarily about the world of start-ups, young employees, making them an essential indicator of the modern corporate image in the eyes of many.

Photo by Firmbee.com on Unsplash
3. Other benefits
Improved employee mobility, greater employee satisfaction, increased employee productivity and employee privacy are also among the drivers and benefits of BYOD for employers.
5. What are the disadvantages of BYOD?
“BYOD can be a nightmare for senior IT management for a variety of reasons, including high on the list issues around device support and system security. There is no guarantee any employee provided device, once connected to your corporate network, is going to behave in a predictable and secure manner.” - unknown
5.1. Drawbacks of BYOD to employees
1. Workers may not be able to afford the right tools
Of course, it sounds so good that everyone brings the best and latest, most perfect machine of their own. But let’s not forget that not everyone can afford to have such machines. On the other hand, it is also true that not everyone likes to work from their device to do company things.
Consider what work needs to be done and what software needs to be run on your machine, how well your machine’s configuration meets these expectations, what antivirus program is running on it, and so on. With rapidly obsolete tools, it can be difficult for an employee to work, not to mention managing updates and backups.
2. It is easier to divert the employee’s attention
Using a private device often impairs work efficiency, distracts the user as the boundary between corporate and personal use of their own device is more blurred. BYOD requires more attention and self-discipline on the part of the employees, as using their own tool as a work tool inevitably increases the chances of something distracting them from work.
“Cyberslacking” is a relatively new word in English that describes the phenomenon of employees browsing the Internet at their workplace not doing work-related activities. We have all met colleagues who hang out on social sites or in chat rooms most of the day and do not even mute their notifications, disturbing their colleagues at work.

Photo by Magnet.me on Unsplash
5.2. Drawbacks of BYOD to employers
1. IT department resistance - challenging to monitor and maintain devices
In many cases, the first reaction of system administrators and IT decision-makers is the rejection of the idea that employees work on their own machines on the corporate network. This fear is entirely natural for the integrity and security of the internal system, but a ban can only reduce the work efficiency and motivation of colleagues.
While the hardware cost is really out of the question, the employer should be aware of the “hidden costs” of BYOD. Imported mobile devices always incur additional costs for the IT department, as managing these devices requires high additional costs per mobile device.
This approach is fundamentally at odds with the rigorous mindset that centrally provides the entire IT infrastructure and requires new security measures. Suppose employees use the same machine at work while connecting to social networking sites in the evening, watching online movies, or playing online games. In that case, it also poses a number of new threats and a new non-existent attack surface against corporate data: out of a professionally protected, secure corporate environment, data becomes a much easier prey.
Frequently carried devices can be stolen on the go, lost by their owners, leaving company data in the wrong hands, or easily falling victim to viruses and other malware, which can infect the company’s network and machines in a matter of seconds.

Photo by Marvin Meyer on Unsplash
2. The question of integrability
The burden on the IT department continues to increase as employees use a variety of tools, resulting in a highly heterogeneous hardware and software portfolio due to the nature of the BYOD system.
3. Software license related challenges
Another conflict of interest could be the issue of software licenses: licenses purchased by companies do not apply to employees as private individuals. The software, which is installed on the employee’s device within the framework of BYOD, is also available in the employee’s free time beyond working hours.
4. Software updates related issues
The broad diversity of BYOD models and operating systems makes it difficult for the IT staff to manage individual devices and keep them on the latest updates. For any business that follows the BYOD practice, it is worth calculating the additional cost of a so-called Mobile Device Management (MDM) system to manage data stored on personal mobile devices securely.
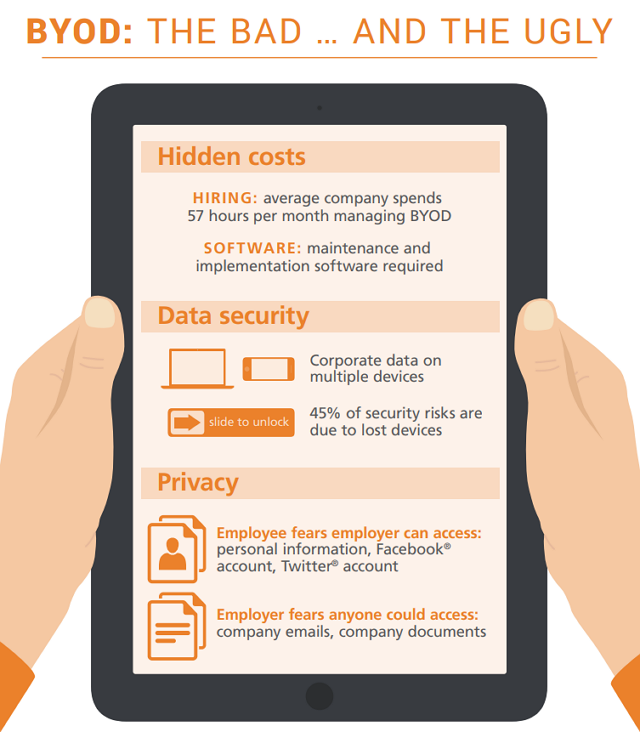
Source: Slideshare
5. Data protection and data security
Data protection and data security are the biggest challenges of the BYOD system - hence, for example, strictly prohibited in public administration.
With the vast amount of data stored by BYODs, it is not easy to distinguish between corporate and personal data. This situation increases the chances of cyberattacks because IT administrators have little or no control over this data.
6. Data compliance
Strict adherence to the rules on access, use or dissemination of data is mandatory. With BYOD, there is a good chance that employees can share their device data with other people outside the organisation. Therefore, the implementation of BYOD makes it more difficult to enforce compliance.
One of the biggest challenges for the IT department is to adhere to data compliance regulations, such as GDPR, in a BYOD-type work environment. Boundaries are often blurred in terms of the workers’ own machine and the corporate and private data on their machine, and the regulations and legislation that apply to them.
Remember: the employer is always responsible for complying with data protection provisions, even if the employees use their own devices to work without the express permission of the employer.

Photo by Lars Kienle on Unsplash
For the effective implementation of BYOD, it is advisable to enter into a user agreement with the employee, which regulates, among other things, what data must be deleted and when, and when and to what extent the employer has the right to control the employee’s assets. It is also worthwhile to stipulate in a contractual form how the employee can manage company data on their device - for example, to ensure the possibility of immediate termination of remote access in case of loss or theft of the device.
7. Training of the employees
There is an additional cost to the training required, as it is essential that BYOD employees adequately protect company data on their devices.
8. Lost or stolen devices
The promise of higher mobility is also an influential risk factor, as the employee takes the assets everywhere, increasing the exposure to asset theft or the risk of loss, which is an absolute nightmare from the data protection point of view.
9. Malicious apps
When employees download malicious applications to their mobile devices, they grant unauthorised access to critical corporate data to a third party. Installing security software and adding updates and patches to these devices is cumbersome because IT administrators have no control over these devices.
10. Encryption - a solution to BYOD problems?
Proper encryption of corporate data is essential to use an effective BYOD system. You can encrypt the entire background storage of a device or certain parts of the storage.
Any servicing of the BYOD devices may involve additional data protection risks, which even the most effective encryption cannot solve: the devices on which we handle sensitive company data must always be serviced only in qualified stores!
6. BYOD Statistics and figures
“The top two reasons enterprises hesitate to enable BYOD to relate to company security and employee privacy.” - Anurag Kahol, CTO of Bitglass
- The BYOD market is to exceed $ 366.95 billion by 2022
- The Asia-Pacific region is growing at the fastest rate
- An average BYOD employee works an extra two hours daily
- Email, calendar, and contact management are the most popular mobile apps
- 69% of young employees (millennials) believe regular office attendance is unnecessary
- Employees can increase their productivity by 34% with a portable device
Intel introduced the BYOD concept first in 2009 when its management began encouraging the employees to bring their devices with them and connect to corporate networks. Intel was followed by other IT giants, like IBM, Unisys and Citrix.
The growth of BYOD was gradual between 2010 and 2014, but its adoption has been increased steeply ever since.
The pandemic had a significant impact on the further expansion of teleworking and BYOD. COVID-19 has had a lasting effect on people’s work, and as a result, telecommuting has become the new norm. We have seen more employees than ever before using their tools to succeed remotely while away from the office.
Without wishing to be exhaustive, here are some interesting data with their sources about BYOD:
- The BYOD market is expected to exceed $ 366.95 billion by 2022, up from just $30 billion in 2014 (Source: BetaNews).
This is due to the widespread use of portable devices and the growing number of businesses introducing enterprise mobility solutions that allow and encourage employees to work anytime, anywhere, from a wide variety of devices. - US is the largest market for BYOD; the Asia-Pacific region is projected to grow at a faster rate (20.8%) (Source: BetaNews).
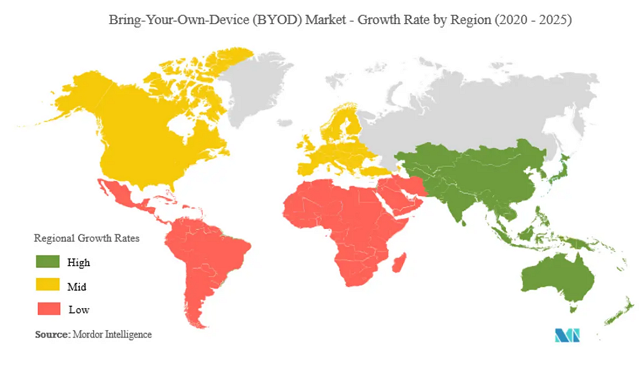
Source: Mordor Intelligence
- Companies supporting BYOD achieve annual savings of $ 350 per employee (DMS Technology).
- An average BYOD employee works an extra two hours daily (Finance Online).
- According to 61% of employers, improved mobility is the most significant driver for BYOD (TechJury).
- Email, calendar, and contact management are the most popular (84%) mobile apps enabled on BYOD (TechJury).
- Providing access to business-critical information to employees, regardless of geographical location, encouraged the rapid adoption of BYOD solutions (Mordor Intelligence).
- Smartphones are by far the most preferred devices for BYOD employees (Mordor Intelligence).
- 69% of young employees (millennials) believe regular office attendance is unnecessary (TechJury).
- The compound annual growth of the BYOD market will be 15% between 2021 to 2025 (Mordor Intelligence).
- Employees can increase their productivity by 34% with a portable device (Finance Online).
After the statistics showing the benefits of BYOD, let’s look at a few examples of what factors hinder or slow the rapid spread of BYOD. The greatest barriers to the spread of BYOD are as follows:
- 39% of companies identify security concerns as a major barrier to taking over BYOD (TechJury).
- 72% of companies say data leakage/loss is the top security concern for BYOD (TechJury).
- 56% of BOYD companies use remote wipe and MDM to deal with security (TechJury).
- Only 14% of companies have a preferred mobile security app for their employees (TechJury).
According to a survey conducted by Bitglass in 2020, the following main concerns were identified by the companies surveyed:
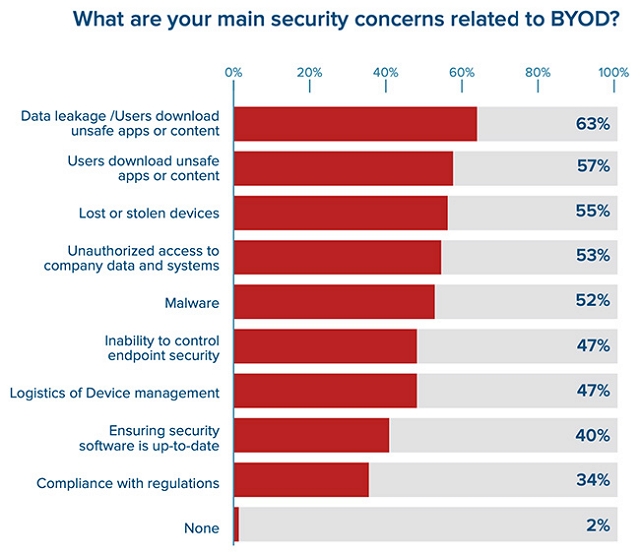
Source: Bitglass
The survey data show that most companies fear the leakage of sensitive company data (63%), the downloading of insecure apps by employees (57%), and the disappearance and theft of devices (55%) after switching to BYOD.
Perhaps the most important conclusion we can draw from the survey is that while BYOD adoption is growing rapidly, many companies are unprepared and lagging in balancing security and productivity.
When Bitglass surveyed companies’ mobile enterprise messaging security capabilities obtained the following results:
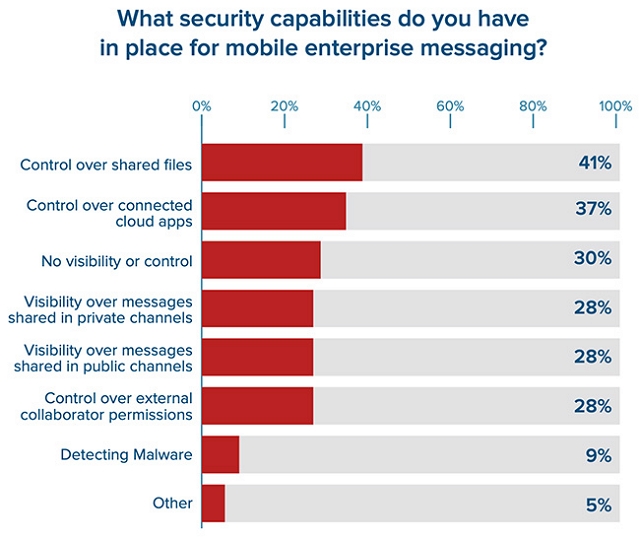
Source: Bitglass
The research shows that some organisations implemented BYOD without taking the right steps to protect corporate data: 41% of the organisations surveyed have no control over file-sharing applications, 30% have no visibility over mobile corporate messaging devices, and only 9% have cloud-based malware detection.
Companies are often in a state of urgency. Due to technological advances and the recent pandemics, they are forced to support remote work and BYOD, allowing their employees to work on their own devices and even remotely. With these drastic changes, the companies IT departments are often unable to keep up.
7. Is it worth implementing BYOD?
“IT Security is a form of Problem Management. It looks to proactively prevent Incidents.” - Unknown
After discussing the many advantages and disadvantages of BYOD, the question arises as to whether it is worthwhile for companies to implement it? The answer is not always: organisations should only implement the BYOD policy if they are fully prepared to deal with it. Before introducing BYOD, the following factors are worth paying attention to:
7.1. Clarify policies and permissions
It needs to be fixed in advance which colleagues the company will support the transition. Those who can use their own machine need company training that includes security conditions for accessing company data. The system of rights needs to be clarified, meaning that no one should have access to more than they need for their work. It is necessary to lay down the permitted and prohibited applications and uses for the device involved in the work. The established IT policy must be followed as strictly as possible.
7.2. Protection of company data
Since mobile devices are not only used for work, it is also possible to use forms of communication in which sensitive company data can come out of the company. Today, several management solutions can be used to centrally control data communications so that phones and tablets can be managed and disabled remotely, similar to corporate PCs.
7.3. Support business applications on mobile
With ever-evolving business mobile applications, every phase of office work can be handled on portable devices. If a company makes these programs available with the proper permissions, its employees can also do full-fledged work from their own mobile devices, which significantly increases efficiency - in return for increased security risk.

Photo by NordWood Themes on Unsplash
7.4. Private cloud
One of the most significant security risks is the connection of remote users to corporate networks. However, security and efficiency can be enhanced by private cloud-based solutions that can create “in-house” conditions for such employees.
7.5. Prepare for problems
Always have a replacement tool available so you can keep your work running smoothly. It is also advisable to prepare for the possible exit of the employee. A pre-arranged agreement can ensure that all confidential company data can be deleted from phones and tablets when an employee leaves the company.
7.6. Develop a written BYOD policy and introduce it to employees
By weighing the advantages and disadvantages, along with compliance issues, organisations should develop a written BYOD policy that comprehensively addresses BYOD security issues. The BYOD policy should include compliance aspects such as:
- What types of data can be accessed through a personal device?
- How is data transferred between personal devices and business servers?
- How and when company data should be deleted from a device?
- What type of encryption should be in effect?
The prerequisites for a successful BYOD transition are that employees know the answers to these questions and are aware of safe practices for using their tools within corporate networks. The BYOD policy can be any detailed; if employees are not aware of the BYOD rules and do not know how to use their tools and data, then the company’s exposure to cyberattacks and threats remains very high.
8. Mobile Device Management (MDM)
“I think the biggest change, and the one we’re already starting to see take shape, is that globally the majority of internet usage will be done via a mobile device and for most people, the mobile web will be their primary – if not their only – way of experiencing the internet.” – Peter Rojas
With many mobile and BYOD devices, it is not easy for businesses to manually manage and monitor all devices on their networks. A mobile device management (MDM) solution is necessary, which provides a centralised dashboard for efficient management and monitoring of the entire device portfolio.
With a suitable MDM system, the following activities can be performed:
8.1. Remotely control devices
With the comprehensive MDM solution, you can remotely monitor and manage files on your device from any browser. If a device is stolen, you can take a photo of the thief with the device’s camera and send it to the competent authorities before erasing the data remotely from the device.
8.2. Enforce a strict password policy
You can enforce a strict password policy across multiple devices. By applying password policies across multiple devices, you can save time and improve cybersecurity. You can force password specifications, such as password length, number of failed attempts, or time interval before auto-lock. If a device is lost or stolen, you can change passwords, delete data remotely, and restore factory settings.
8.3. Find, track and create location history of devices
Using MDM, you can track the location of each device and create a complete location history. You can also enable location history for a group, department or role, and specify the periods during which records should be logged.
8.4. Remote device management
You can manage hundreds of mobile devices remotely. You may group them according to department, role or job function. You may also customise the settings of the devices per group. Utilising the MDM application, email and Wi-Fi settings can be remotely configured.
8.5. Enforce VPN usage
With free Wi-Fi almost everywhere, telecommuters can access very insecure networks such as cafés, hotel lobbies, airports, etc. To provide a direct connection to the data you need to get the job done, you need to include a VPN solution on every device without compromising your company.

Photo by Dan Nelson on Unsplash
9. Implementing a BYOD policy
“IT is ever-changing, and there is the need to evolve in order to stay relevant.” – Ryan Ogilvie
A BYOD policy is a clearly defined set of rules covering the permitted and prohibited conditions in a BYOD program. The BYOD policy should specify at least the following:
- What devices can be brought in?
The employee may only use the device(s) in the BYOD program of which the employer is aware.
- Strict device authentication methods.
Alphanumeric passwords or two-factor authentication is required, the details of which must be regulated.
- Which apps are allowed?
The employer needs to know about the applications used on the employee’s devices besides the devices themselves.
- Employee exit strategy
When an employee leaves the company, there should be a procedure on know how to secure the company data stored on that employee’s device.
The rapid spread and development of mobile devices require a new regulation and approach. In the age of tablets, company data protection is partially based on trust in the end-user, although this alone is not enough. But IT will not be able to manage all devices at once, according to experts.
Companies can prepare for the new type of operation and regulate in advance the conditions for the usage of their assets and their connection to the corporate system. Clarifying the terms of use of a mobile device is the responsibility of the company’s IT or IT security department.
Did you know?
Nearly 60 percent of businesses allow employees to bring their
own devices, but only 39 percent have a BYOD policy in place.
(Your BYOD plan – savior or security threat?)
10. Tips for achieving secure BYOD
**“If security were all that mattered, computers would never be turned on, let alone hooked into a network with literally millions of potential intruders.”
- Dan Farmer**
The introduction of appropriate tools and measures will not only make mobile work safer but also simpler and more efficient.

Source: Slideshare
10.1. Educate users
One of the cornerstones of a secure BYOD strategy is that both company executives and employees are aware of the threats of using their own devices and the reasons for various security measures. It is easy to outline what to do and what to expect and educate users about emerging threats. Besides, at certain intervals, it is worth testing the knowledge and reactions of employees to see if they comply with all regulations and advice in practice.
10.2. Monitor access from mobile
Ensure that company information accessed and used on non-standard devices is monitored. You can apply unique settings, among other things, to cases where employees work with data from a remote location. In this case, make sure that the company files are never saved on the device so that sensitive data remains safe.
10.3. Adhere to access control policies
Also, make sure that only the right people and devices have access to your company data and applications. Do not allow a particular smartphone or tablet to access corporate resources if the systems cannot identify the user, if the device does not meet any compliance requirements (for example, it is not set to use a PIN and screen unlock code), or if it is not running the required software (such as an antivirus program). For remote access, you may also want to check where the device is located and whether it is using an encrypted connection.
10.4. Extend device management to mobile devices as well
If employees use smartphones and tablets for their day-to-day work in the same way as desktops, these mobile devices need to be monitored in the same way as devices within a secure corporate infrastructure.
10.5. Encrypt sensitive data
It is a good idea to encrypt all data stored on non-standard devices that is corporate property, including corporate email messages from employees. This way, company information does not fall into the wrong hands even if the device is lost or stolen.
11. How can SECURITYMADEIN.LU help?
“Education has always been a profit-enabler for individuals and the corporation. Education, both conception and delivery, must evolve quickly and radically to keep pace with the digital transition. Education is a part of the digital equation.”
― Stephane Nappo
BYOD has been one of the most frequently mentioned phenomena among corporate IT professionals for years. The question is not how successful it will be in the future or whether we will accept it, but rather how to prepare for its introduction and application.
The essential preconditions for preparation and successful application are getting to know BYOD, organising awareness-raising training for the company’s employees, preparing employees for the new life situation and mitigating the resulting cybersecurity threats.
CASES (Cybersecurity Awareness and Security Enhancement Services) is part of SECURITYMADEIN.LU. It has multiple services available for the public to raise awareness in connection with cybersecurity in general and BYOD in particular.
CASES has already addressed BYOD in the article BYOD un risque et une opportunité en même temps in 2014. CASES experts also hold regular information security awareness sessions that cover, among other things, this topic.
You may also read about BYOD in the CASES article How to Discuss Cybersecurity with Your Employees? Use BYOD! and about teleworking in the article Teleworking: How to Secure your Employees Wherever They Are.
In addition to professional CASES training sessions, you may also get valuable information on the SECURITYMADEIN.LU portal, where you can read articles, register for the Cybersecurity Breakfast series, watch the Lëtz Talk About Cyber series or read cybersecurity-related news, besides other things.
12. Conclusion
“Threat is a mirror of security gaps. Cyber-threat is mainly a reflection of our weaknesses. An accurate vision of digital and behavioral gaps is crucial for a consistent cyber-resilience.” - Stephane Nappo
Of course, one can argue against BYOD, but the change cannot be stopped, and for now, it seems to be the direction.
- BYOD is a risk and an opportunity at the same time
- How to Discuss Cybersecurity with Your Employees? Use BYOD!
- Teleworking: How to Secure your Employees Wherever They Are
- The Ultimate Guide to BYOD Security
- 43+ Stunning BYOD Stats and Facts to Know in 2021
- Your BYOD plan - savior or security threat?
The emergence of a wide variety of frequently changing tools in the corporate environment can ultimately lead to IT professionals being unable to keep up with ever-changing technical requirements and guarantee the security of business data.
According to IT experts, the most pressing issues are security and data protection, as well as the compulsion to deal with IT support for multiple mobile platforms, as opposed to a unified enterprise IT background. The biggest challenge for IT managers is to balance between security and at the same time support requirements with the cost and efficiency benefits provided by BYOD.
While cutting IT costs with a short-term approach may have immediate results in the cash flow, it can ultimately cost the company more in the long run - if the switch to BYOD practice is not cautious enough.
We are increasingly getting where BYOD is no longer a privilege for employees but a requirement for companies. Companies have begun to realise that BYOD is well worth it for them if kept within the proper framework. It is an attractive option for companies to work with employees outside the office since they do not have to finance the assets.
And with more and more outsourced staff and the advancement of telecommuting with the Internet, it can become more and more common to work with someone without even meeting them.
Technology favours BYOD
The growth of BYOD is also predicted by the direction of technological development. BYOD is now more than a corporate email and a VPN client that connects an employee to the company’s servers. With the cloud and applications that provide solutions to enterprise processes, more and more business tasks can be managed remotely.
With the development of apps, work becomes even more flexible, the possibility of working together online further develops, and communication becomes more efficient. The Internet of Things (IoT) is also entering the realm of BYOD: think of wearable devices, sensors in different objects.
BYOD requires more attention
As BYOD continues to expand and becomes more complex, it will be more important than ever to create a policy and develop a strategy to address this transition within the company. IT departments need to map out how they can manage this area. There is a need to define standards and usage requirements, proper administration, monitoring, support and control mechanisms.
What does the future hold for BYOD?
Certainly, BYOD will continue to grow among employers and employees in the future. The process seems unstoppable, and the pandemic has fundamentally changed our work habits and given a final push to the further spread of BYOD.
The question is no longer whether to switch to BYOD, but rather how we can do it to make the most of it. Successful implementation depends on how to implement BYOD with enterprise resources, streamline the process for users, and, most importantly, ensure all of this while maintaining personal and corporate data integrity.
